
In July Deloitte held its Annual hackyholidays Capture the Flag (CTF) event. This year’s theme was to save the city from an evil AI. There were 32 challenges with multiple parts in each challenge. In total there were 81 individual tasks with various points.
This year CTF focused on a number of areas (Web, Forensics, Exploit, Reversing (Mobile, Linux, and Windows) Cloud, Quantum, and Steganography). As with my passion, I focused on Forensics and completed most tasks. I was also successful at some of the web exploitation challenges, All the training from tryhackme has paid off.
Below I will discuss the challenges completed in full and then I will go through the partially complete challenges.
We have collected information from a small ICS network. Can you uncover all the data hidden in these files? (Network and ICS)
In this challenge you are presented with two PCAPNG files (Modbus.pcapng and Network.pcapng)
Part A The file shows communication between a PLC and an ICS workstation. Analyze the file to get the flag! (use modbus.pcapng)
We open the Modbus file within Wireshark and inspect the conversations (Statistics -> Conversations)
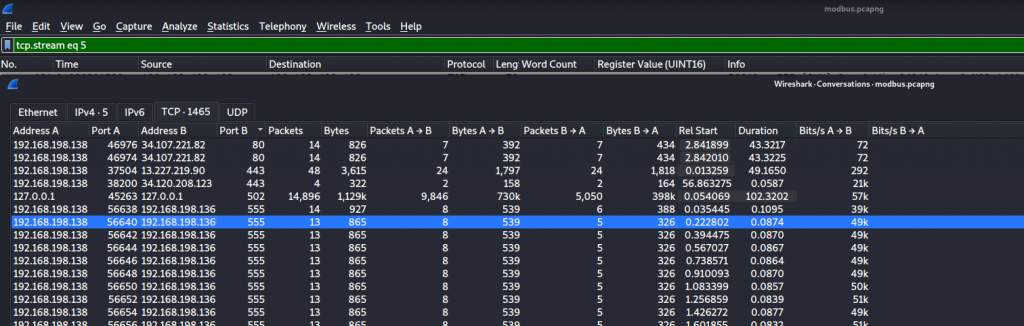
Reviewing each conversation we can see one conversation gives us the first flag
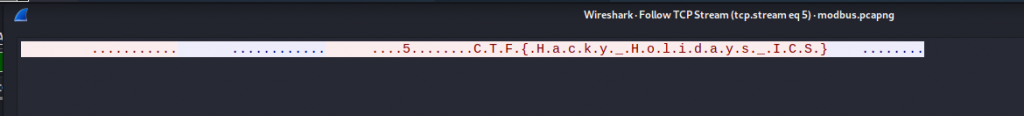
Part B There seems to be some suspicious activity in the network. Can you identify the IP address of the rogue ICS component? (use network.pcapng)
As are still in the conversations we review “Address A” which is the sending address and we see that 192.168.198.128 is our rouge ICS component.
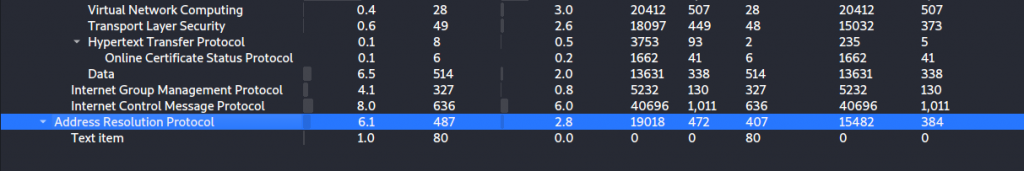
Part C What is the protocol used in the Man-in-the-Middle attack performed by the rogue ICS component in this network? (use network.pcapng), Flag format CTF{protocol_in_capital_letters}
Jumping into the Protocol Hierarchy we can see a list of protocols being used, This was a little bit of guessing but the Answer was ARP (Address Resolution Protocol)
Part D The rogue component is communicating with an external entity, which is a big red flag in ICS environments. Can you find the flag from the network data?(use network.pcapng)
Working through the conversations over port 80 we are alerted to a conversation that is loading a png file

Taking the base64, decoding, and then output to a png format
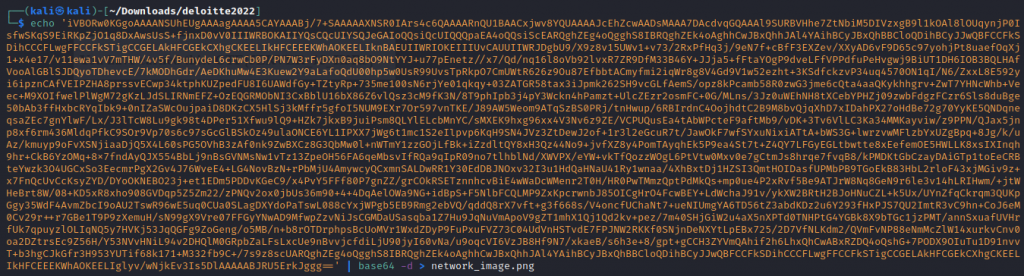
we get the flag as
We intercepted an audio transmission the AI was sending to Rizal, however we have not been able to identify the contents of the message, are you able to help us out? (Stego)
In this challenge, we are given a wav file called SecretMessage.wav
Part A Are you able to see what was being sent?
Listening to the sound there seems to be static then, some talking and more static. Using Sonic Visualizer we load the file and we can see the sound waves
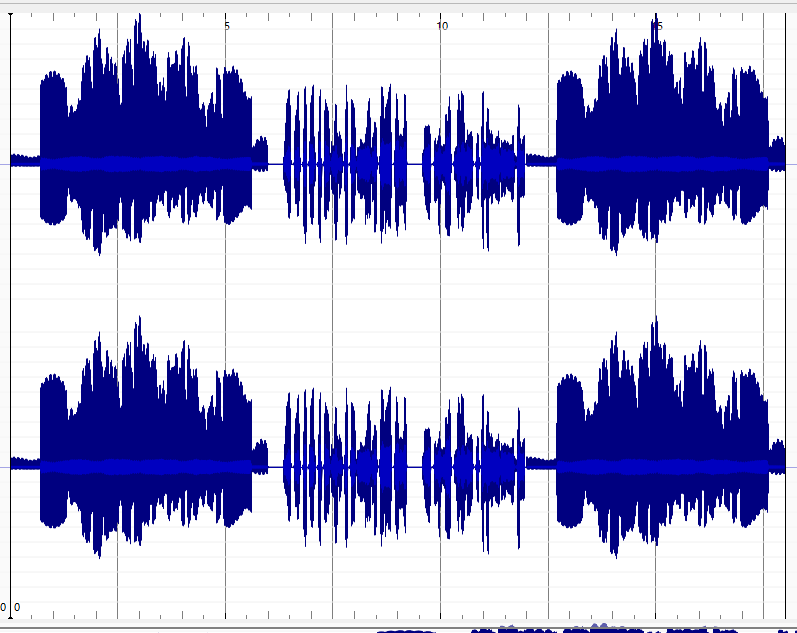
Applying the Spectrogram filter we get our first flag CTF{tagalog}
Part B We think it may have something to do with a code, can you find it?
Now listening to the sound in the middle it did sound like a language, taking the hint from the first flag I believed the message was in Tagalog (Filipino).
I slowed down the sound and made two copies forward and reverse and reached out to a friend who speaks Tagalog who translated the message to “The flag is 649444”
We noticed that the AI has accessed the research of Professor John Nerdelbaum Frink, Jr. As you may know, the Professor is known to make thinks worse with his bizarre inventions. The AI has written him a super secret letter which you have got your hands on. It is up to you to decode the message and find out what is going on. (Crypto)
We are given a text file with a encrypted message
Part A Can you make sense of the message? Remember the flag format is CTF{your-flag}
We are given the following message
N = 5261933844650100908430030083398098838688018147149529533465444719385566864605781576487305356717074882505882701585297765789323726258356035692769897420620858774763694117634408028918270394852404169072671551096321238430993811080749636806153881798472848720411673994908247486124703888115308603904735959457057925225503197625820670522050494196703154086316062123787934777520599894745147260327060174336101658295022275013051816321617046927321006322752178354002696596328204277122466231388232487691224076847557856202947748540263791767128195927179588238799470987669558119422552470505956858217654904628177286026365989987106877656917
E = 65537Welcome to HackyHolidays! Your Supersecret flag is 176955087574615470063741472647197409875117482285309340581271852382710990213049325727125711804231234813146490233229473679126800639397642380073858980601348297248196895714845780751708931869367483971257602632592317987276609144131149239628356913355893753937582033295526684103570648143766629320982809943886265840131929175495923219383837739522744946987913271495217642469261483099144404131616847257182856944641353523297845726161862062019653065904612865722942649827600090466968124488518262272506900322544403300651512798674316560281124899873116026534973842919190849918357740307152880452169695889599662477611952919511642717417The title for this challenge is Secret Conve.RSA.tions which lets on to the above code is RSA encryption. Doing a google search on ‘RSA e n’ we see
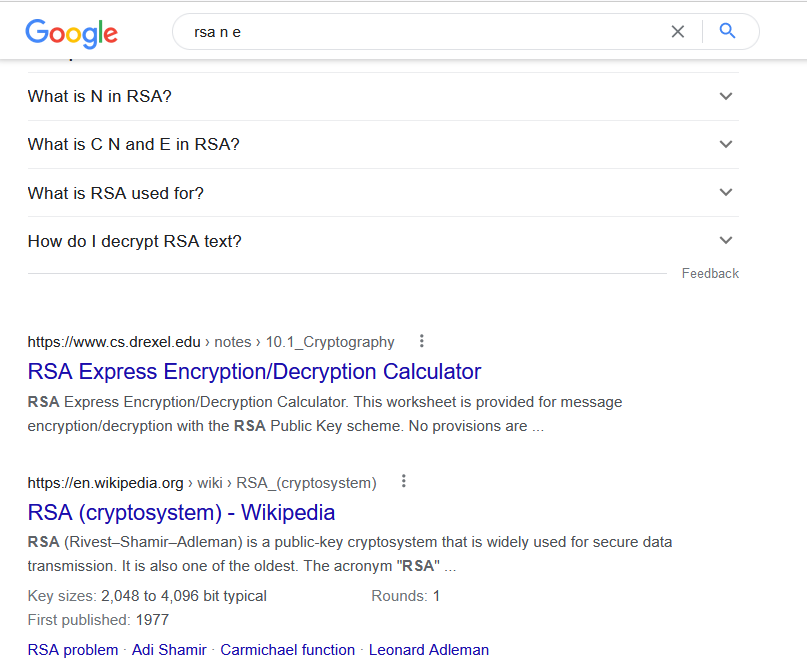
There is also a very nice CTF RSA tool found on Github. running the script and feeding it our input from above we get the following results:
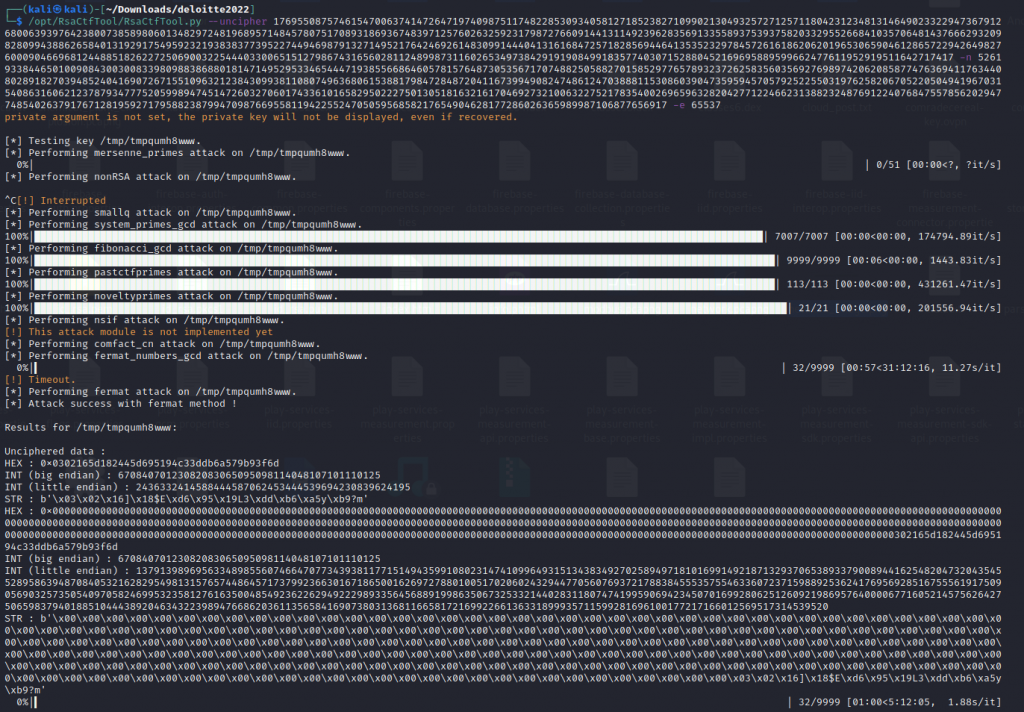
using Cryptii we use the integer decoder and input the Big Endian output and add spaces to break numbers up and we get our flag CTF{RSA_br0ken}
It turns out that taking over a whole city proves challenging even for an AI.
That’s why the AI hired reinforcements to help take control of the city.
Can you figure out which group the AI hired? (Stego, Forensics).
In this challenge, we start with a zip file called bring_in_the_cavalry.zip
Part A Look in the eyes chicho, they never lie
Once we download the zip file and extract it we get 2 files. Key.txt and Trusted_relationships.pdf (password protected)
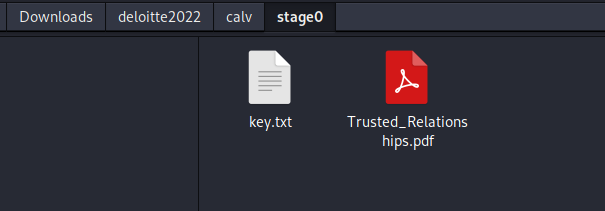
Checking keys.txt with cat shows us that it’s a png file.
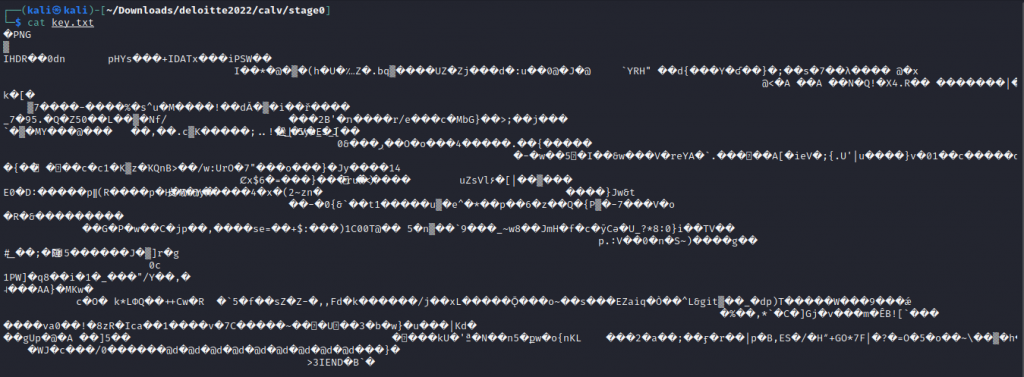
Renaming the file to key.png we see the password to the file
When we open up the PDF, there is nothing spectacular about the contents. The content is a page taken from MITRE Att&ck.
Now we want an unencrypted version of the PDF file, This will allow forensic research to be much easier. This can be achieved using qpdf
Now with the unencrypted file, we can run pdf-parser against the file, Doing so near the top of the file we see two embedded files inside an object being Silent_Attack.wav and Flag1.txt
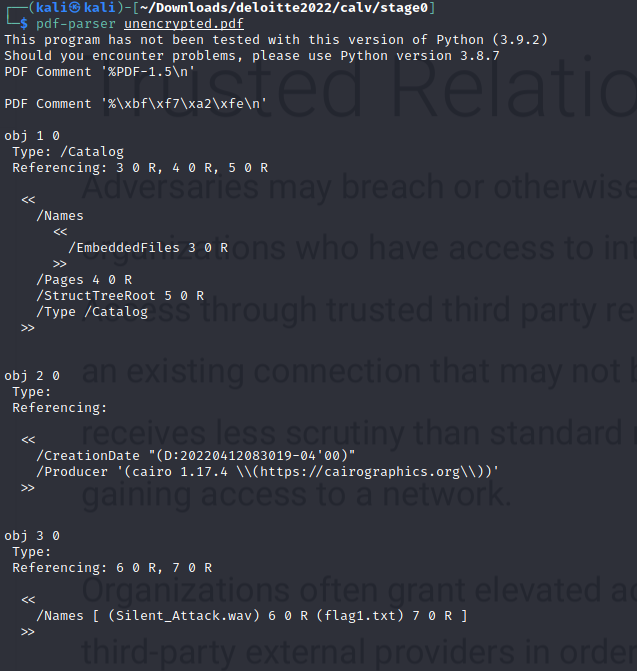
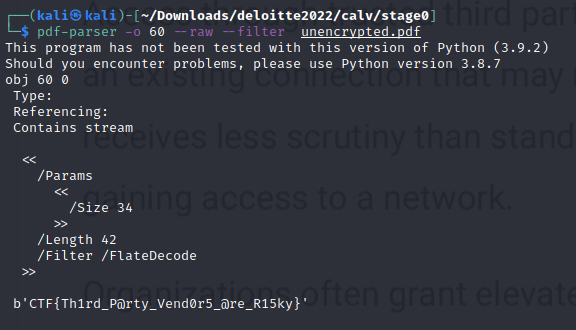
Now we want to dump these files from the Object, This can also be done using pdf-parser. Dumping the flag file first we get our flag.
We do the same steps to the Wav file but this time we save it to a wav,
Part B It would be nice if we could see sounds.
Now like the previous challenge we can hear static kinda of sound, We play the image via the Sonic Visualiser and apply the Spectrogram filter and we see we get a QR code
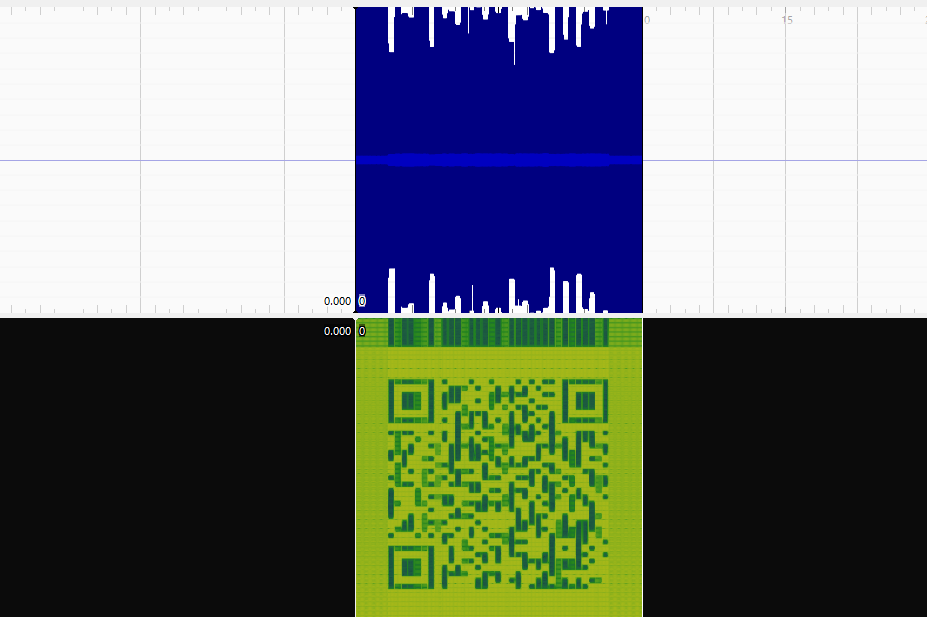
The QR code links us to https://mega.nz/file/GuQQjQjD#ofN2njJUk5zCxVI753BYUiBjUy30kArvLx8L9XJUZPY
When visiting the file we are now presented with an Incident.zip file that extracts to a folder that contains 2 files, flag2.txt, and traffic.pcapng
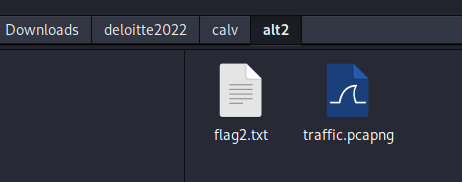
Flag 2 is CTF{Y0u_Better_5ecure_Y0ur_RDP}
Part C How could they do this? This is devastating for our company!
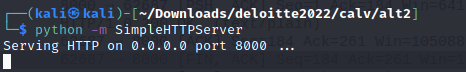
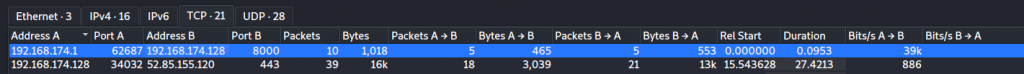
With the traffic.pcapng file we open it into Wireshark and go straight to conversations like in the previous challenges to see what traffic we are analyzing. We see a stream that is communicating on port 8000, By default when using python SimpleHTTPServer this communicates on port 8000 as shown below,
Now with the Wireshark stream entry on conversations
Looking at the steam we see the following URL being listed https://mega.nz/file/zjYjTSAS#c2d5J5DIT_-idyvQ2JeAI2wHfITF7xJEAlViciizk8o
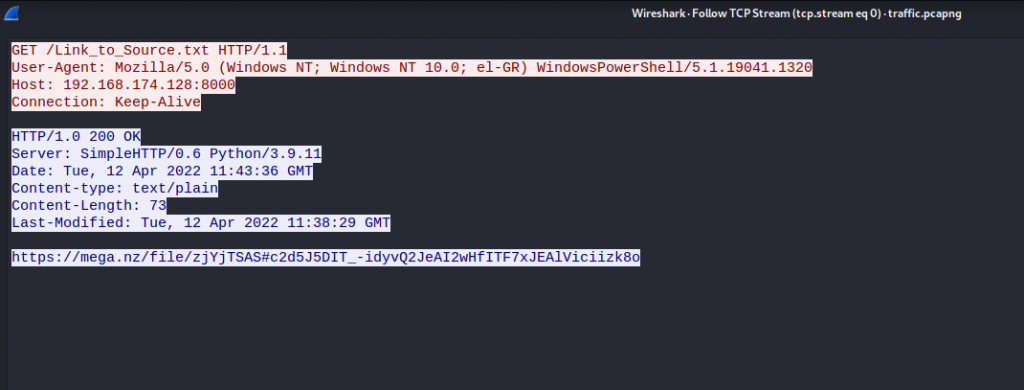
Visiting the URL we get another zip file called Source_code.zip, Once we extract the file we get the folder Source_code with two files, Flag3.txt and Stage4.mem
We get the flag as CTF{Y0ur_Pr0ject’5_50urce_C0de_15_Le@ked}
Part 4 How the hell did they get a shell?
Now we are dealing with a memory dump. Running strings stage4.mem | grep windows We see we are working with a Windows dump
Now using Voliatilty 3 we can analyze the windows dump. What we are looking for is what was run in the command line. We use windows.cmdline option to get the output
There is a fair bit of information that is given, Once we go through all the information we see down the bottom the process which contains our flag.
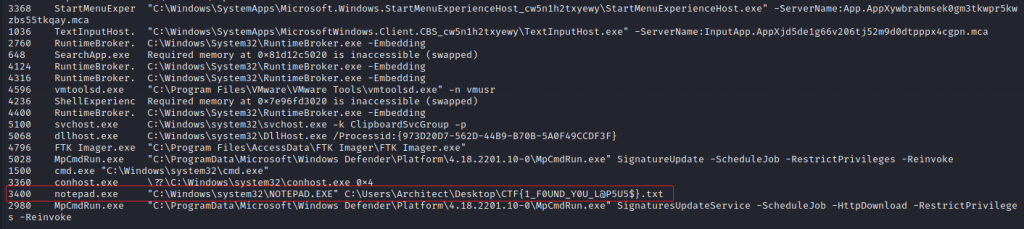
Our flag is CTF{1_F0UND_Y0U_L@P5U5$}
The Mayor of the Smart City was hacked. Try to find out how the attackers exploited his blog! (Web)
We are given a website to hack
Part A There is a hidden flag in the webpage. Can you find it?
Inspecting the page and going through the tabs, under console we see Content Security Policy and it contains our flag.
Part B Try to exploit the password resetting functionality to gain access to an account.
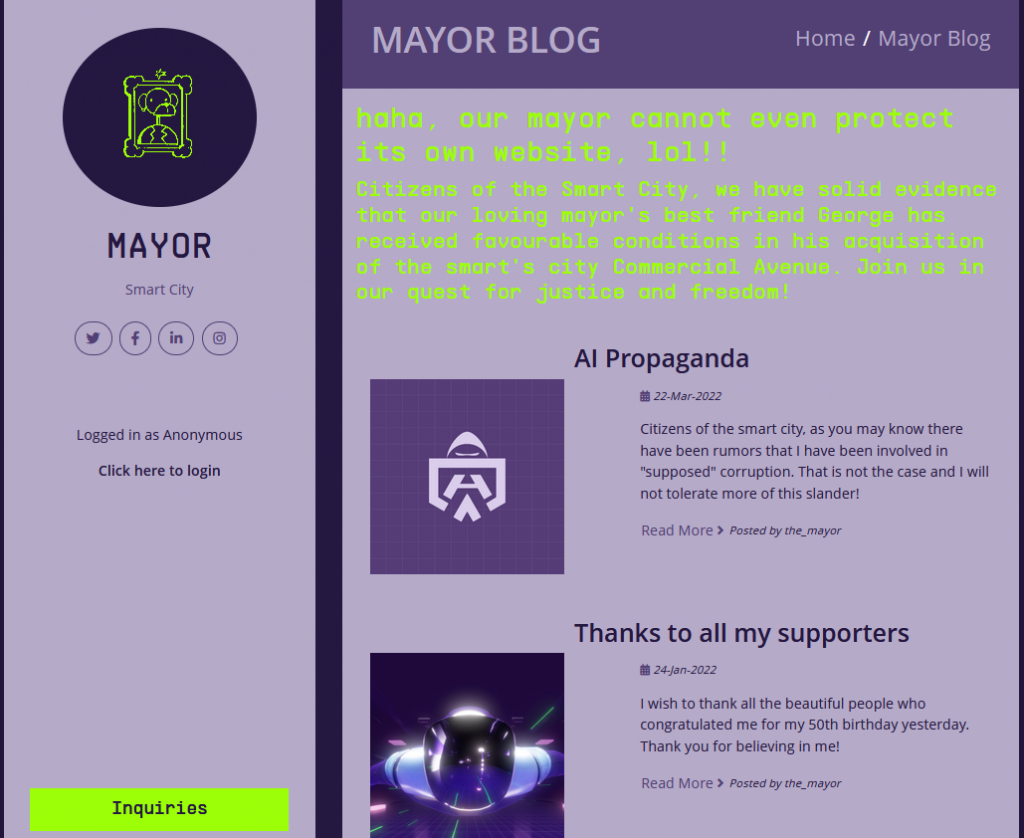
Launching the website we are given a 1-page blog page that contain some PII (Personal Identifying Information)
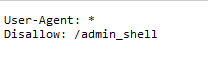
Before we dig deeper we launch our Gobuster directory search and we check robots.txt for any nonindexed pages.
On robots.txt we see there is an /admin_shell directory that is disabled.
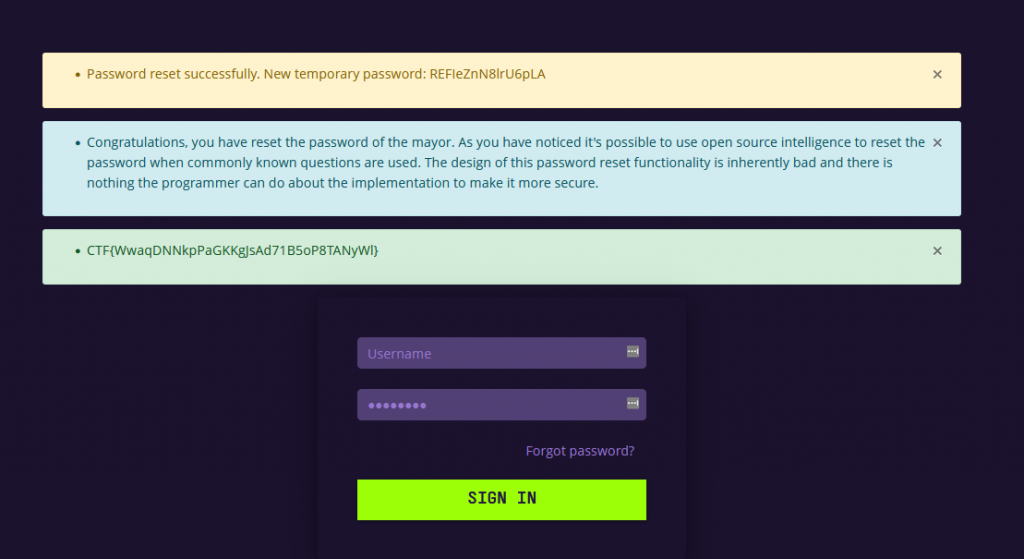
Now waiting for GoBuster to give us some fruit we continue to enumerate the site. From the home page, we click on login and we see a reset password link. When we click on reset password we find the following form asking for Username, Best Friend from Childhood, and Date of Birth
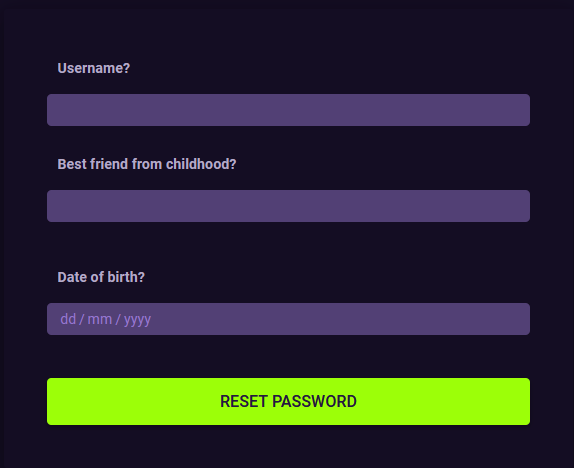
using the information on the home page we can acquire the username is ‘the_mayor’ This is taken from the blog posts. The best friend’s name, Again this is taken from the top of the page where they speak of the mayor’s best friend ‘George’ and finally his birthday as he thanked people for their wishes on his 50th birthday, the blog post is time stamped.
username: The_mayor
Best Friend: George
Date of Birth: 23/01/1972
We are then given a temporary password and the flag
By this time we have been given some fruit from the gobuster scan and we can see there is a folder called logs
Part C It looks like the design of the authentication system is very flawed. Find out how users are authenticated and exploit the system to gain Administrator rights.
We login with the temporary credentials and see what we can access. Visiting both /logs and /admin_shell we get told we do not have access.
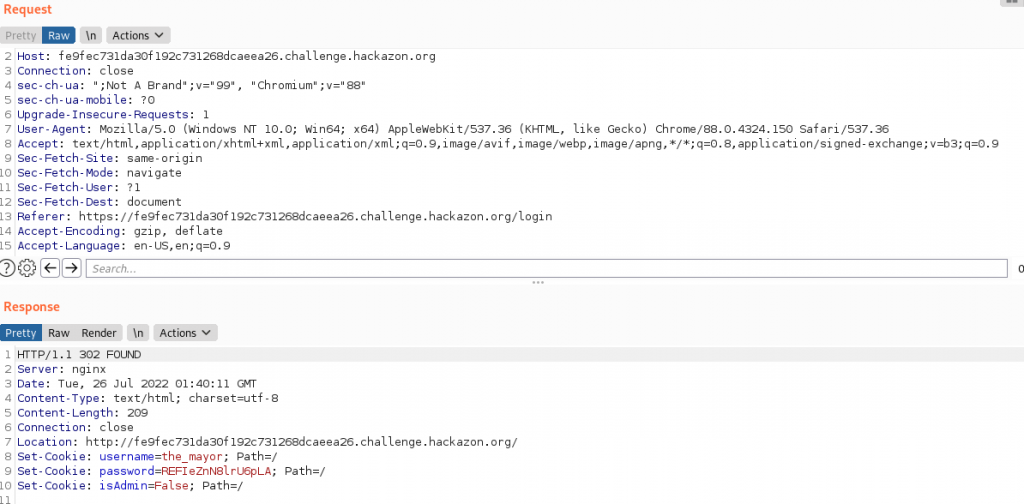
We fire up burp and review the login process. We see the login process is sent as a GET request and we also notice there is a cookie being parsed as isAdmin. this is set to false.
Let resubmit the request again but attempt to change isAdmin to True. We intercept the request and change the cookie, and then forward the request on with the new variable.
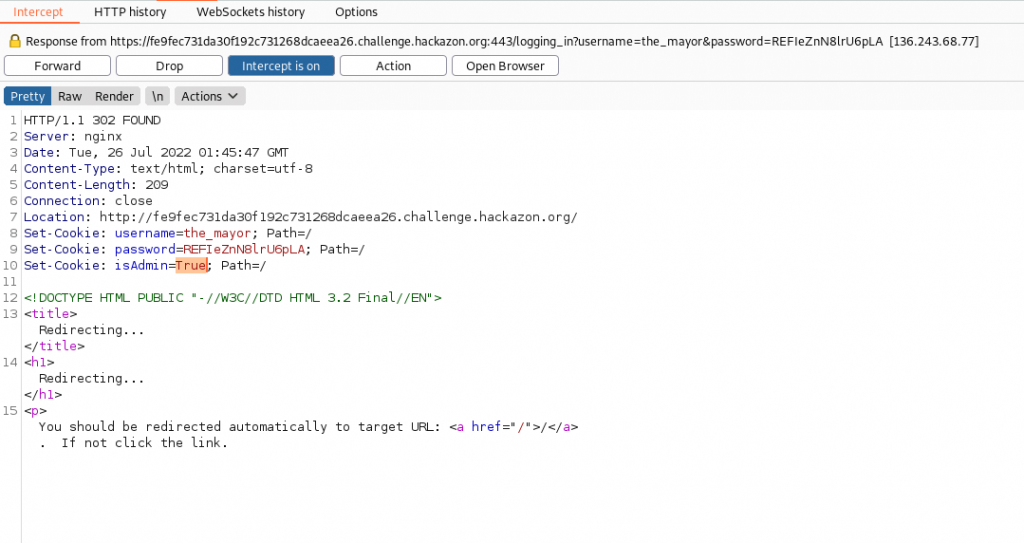
Previously logging in with the mayor’s credentials we logged in as Editor. Now we are logging in as Administrator
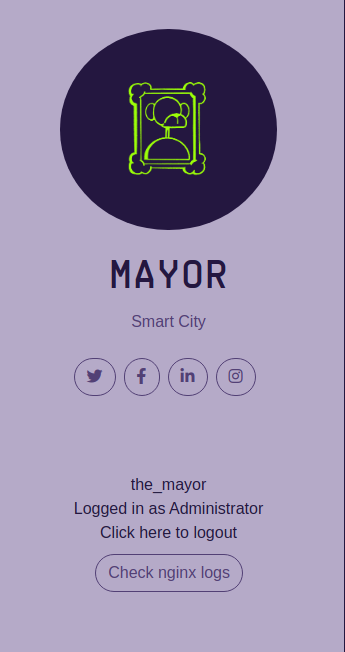
We now attempt to access the /logs and we gain access. We get our next flag and the access logs
Part D There is special console for administrators on the website, but the link is hidden. Find the link, and gain relevant information from the logs. In the end, use the console to find user information.
Now we have access to the logs we start searching to see if we find anything juicy. We discovered the System administrator (sysadmin) has logged in.
127.0.0.1 - - [26/Jun/2022:11:20:31 -0700] "GET /logging_in?username=sysadmin&password=JK28Qgb4WA3uuYa4 HTTP/1.1" 302 208 "http://mayorblog.local/login" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:99.0) Gecko/20100101 Firefox/99.0"Now we logged in successfully as sysadmin we can access /admin_shell
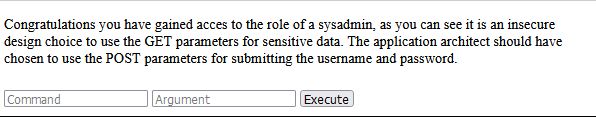
Running ls we see user.txt and when we cat user.txt we get the flag
Part E Find a vulnerability in the developer console and use it to access a password file.
Now we got admin access, lets see if we can access the shadow file in etc, Which we can, and get the admin hash
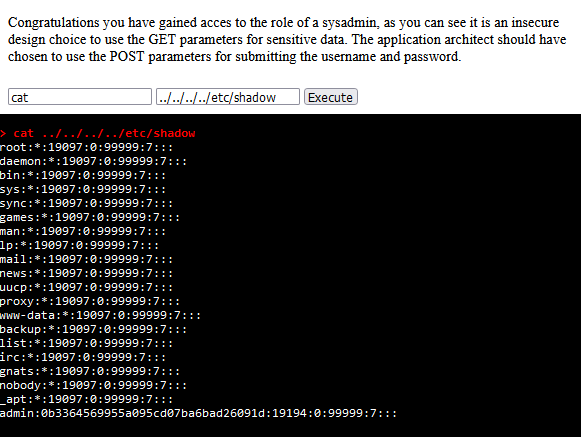
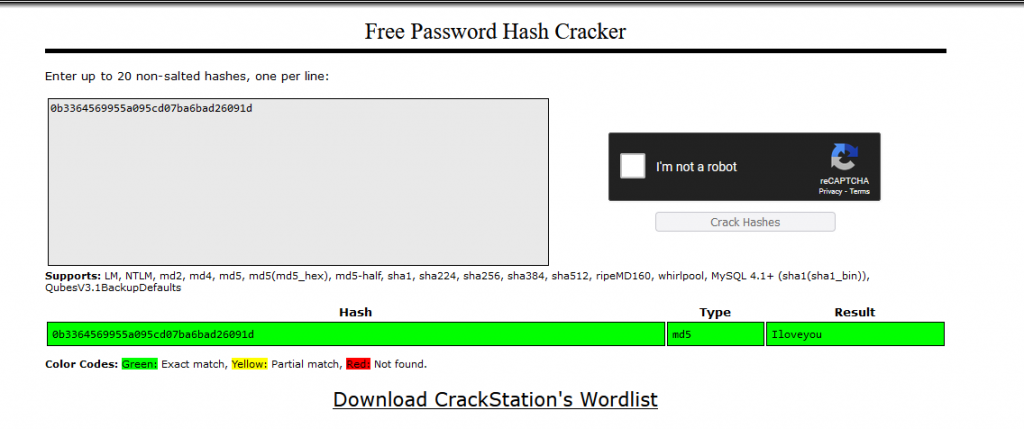
Taking the admin hash and putting it through crackstation we see the password is ‘iloveyou’
The above challenges were the ones I completed in full. I did attempt a number of sub-tasks in the other challenges throught this CTF and I will go through the sub tasks that I completed.
A chemical plant has exploded, can you help us investigate why this happened? (Network, ICS)
In this challenge, we are given 2 files, Chemical_plant_explosion.pcapng, and chemical_plant_explosion.mp4
Part B: We have files showing what happened during the attack. Can we pinpoint the exact moment of the attack in the network?
Like in the previous challenges we open the pcapng file in Wireshark and we start to analyze the file. Under statistics -> capture file property we can see the author of the file left notes with a base64 code.
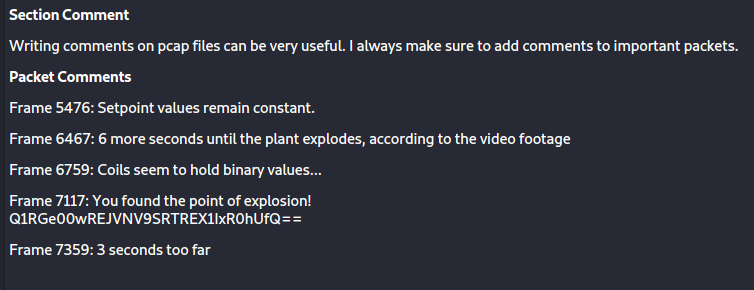
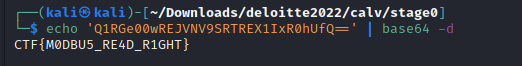
By decoding the string we get our flag
Part C Can you find the setpoint value of the attacked component? HINT: A setpoint value does not change under any circumstance. (Flag format: CTF{(value)})
looking at wireshark we can see the number 65535 repeat over and over again. This is the value
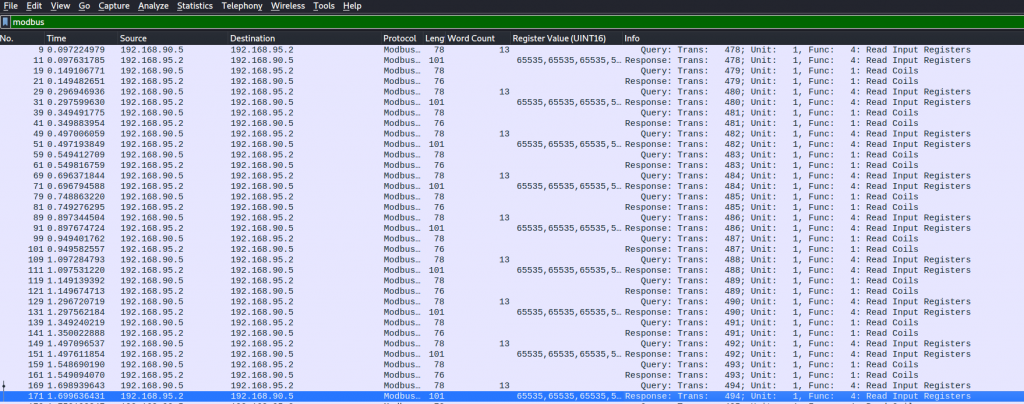
Part C What type of data is stored in register coils? (Flag format: CTF{datatype})
This was a bit of a guessing game, the answer is Binary.
You are presented with a file containing data which is encrypted multiple times to be seemingly secure. The Computer Lab at the Science Center are testing the security level of the scheme used, to protect better against a future attack. Can you prove to them that the method they are using is futile?
We are given an image called binary.jpg
Part A Can you take the right steps till you make it to the end?
We attempt to open up binary.jpg and the file fails to open. When running cat against the file name we see an unique pattern.
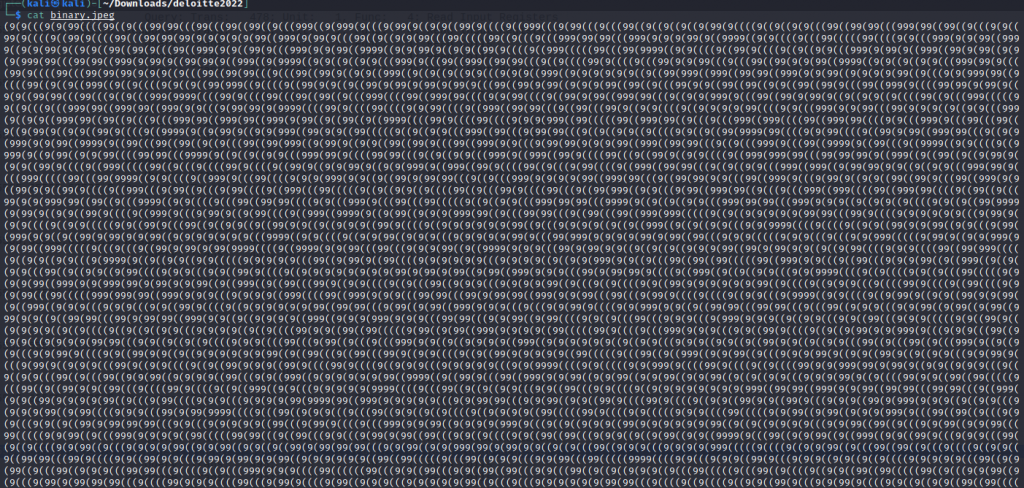
Guessing from the name the above is binary, I wrote a small script to convert the output to readable binary.
The output of the script to binary is
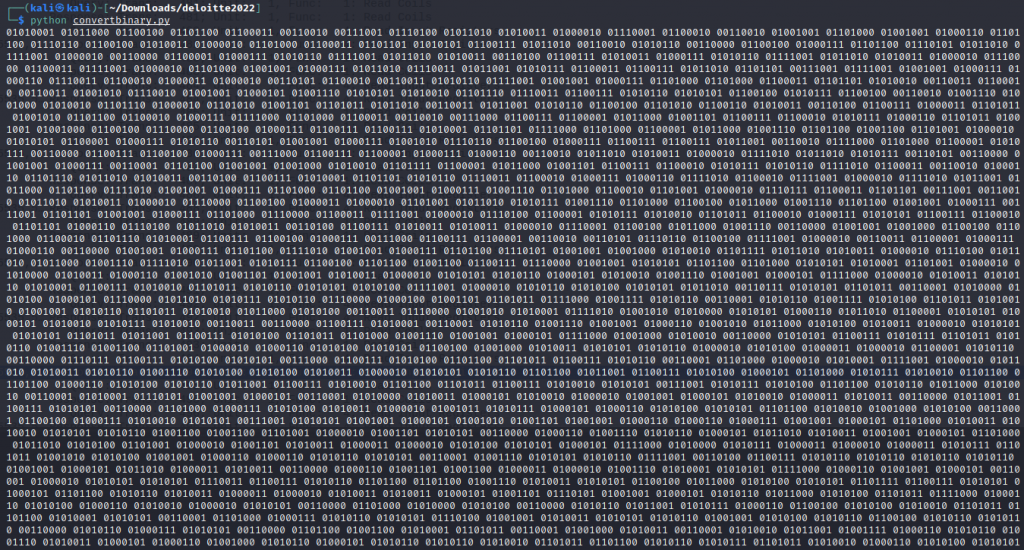
Now using Cyberchef we convert from Binary to Base64 and then to raw text
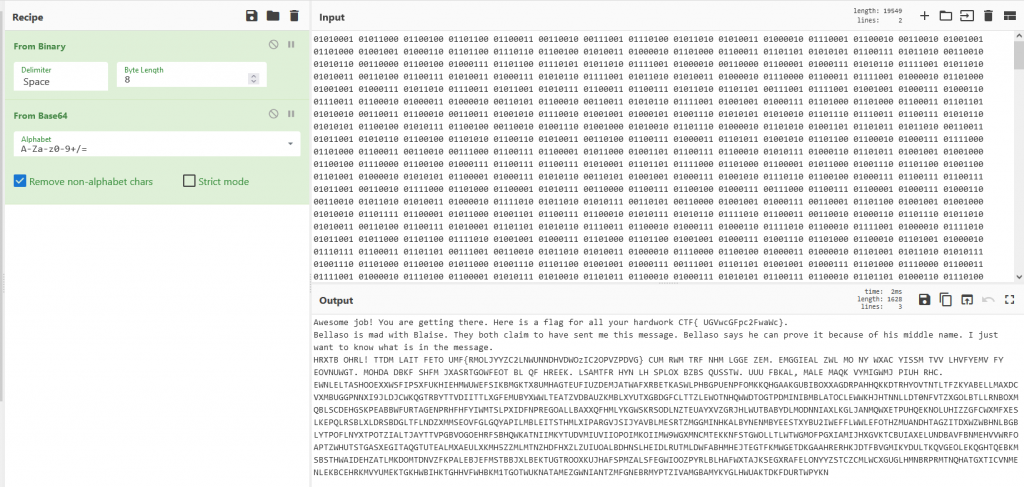
Part B You can find instructions in the previous decrypted text to proceed. On completing this task you will get the second flag.You have solved this (part of) the challenge!
from the last challenge
Awesome job! You are getting there. Here is a flag for all your hardwork CTF{ UGVwcGFpc2FwaWc}.
Bellaso is mad with Blaise. They both claim to have sent me this message. Bellaso says he can prove it because of his middle name. I just want to know what is in the message.
HRXTB OHRL! TTDM LAIT FETO UMF{RMOLJYYZC2LNWUNNDHVDWOzIC2OPVZPDVG} CUM RWM TRF NHM LGGE ZEM. EMGGIEAL ZWL MO NY WXAC YISSM TVV LHVFYEMV FY EOVNUWGT. MOHDA DBKF SHFM JXASRTGOWFEOT BL QF HREEK. LSAMTFR HYN LH SPLOX BZBS QUSSTW. UUU FBKAL, MALE MAQK VYMIGWMJ PIUH RHC. EWNLELTASHOOEXXWSFIPSXFUKHIEHMWUWEFSIKBMGKTX8UMHAGTEUFIUZDEMJATWAFXRBETKASWLPHBGPUENPFOMKKQHGAAKGUBIBOXXAGDRPAHHQKKDTRHYOVTNTLTFZKYABELLMAXDCVXMBUGGPNNXI9JLDJCWKQGTRBYTTVDIITTLXGFEMUBYXWWLTEATZVDBAUZKMBLXYUTXGBDGFCLTTZLEWOTNHQWWDTOGTPDMINIBMBLATOCLEWWKHJHTNNLLDT0NFVTZXGOLBTLLRNBOXMQBLSCDEHGSKPEABBWFURTAGENPRHFHFYIWMTSLPXIDFNPREGOALLBAXXQFHMLYKGWSKRSODLNZTEUAYXVZGRJHLWUTBABYDLMODNNIAXLKGLJANMQWXETPUHQEKNOLUHIZZGFCWXMFXESLKEPQLRSBLXLDRSBDGLTFLNDZXMMSEOVFGLGQYAPILMBLEITSTHMLXIPARGVJSIJYAVBLMESRTZMGGMINHKALBYNENMBYEESTXYBU2IWEFFLWWLEFOTHZMUANDHTAGZITDXWZWBHNLBGBLYTPOFLNYXTPOTZIALTJAYTTVPGBVOGOEHRFSBHQWKATNIIMKYTUDVMIUVIIOPOIMKOIIMW9WGXMNCMTEKKNFSTGWOLLTLWTWGMOFPGXIAMIJHXGVKTCBUIAXELUNDBAVFBNMEHVVWRFOAPTZWHUTSTGASXEGITAQGTUTEALMXAEULXKMH5ZZMLMTNZHDFHXZLZUIUOALBDHNSLHEIDLRUTMLDWFABHMHEJTEGTFKMWGETDKGAAHRERHKJDTFBVGMIKYDULTKQVGEOLEKQGHTQEBKMSBSTHWAIDEHZATLMKDOMTDNVZFKPALEBJEFMSTBBJXLBEKTUGTROOXKUJHAFSPMZALSFEGWIOOZPYRLBLHAFWXTAJKSEGXRAFELONYYZSTCZCMLWCXGUGLHMNBRPRMTNQHATGXTICVNMENLEKBCEHRKMVYUMEKTGKHWBIHKTGHHVFWHBKM1TGOTWUKNATAMEZGWNIANTZMFGNEBRMYPTZIVAMGBAMYKYGLHWUAKTDKFDURTWPYKN
Doing a google search on Bellaso cipher we see Giovan Battista Bellaso is the creator of the Vigenère cypher
using Cryptii again we use the Vigenère decoder and use Battista as the key
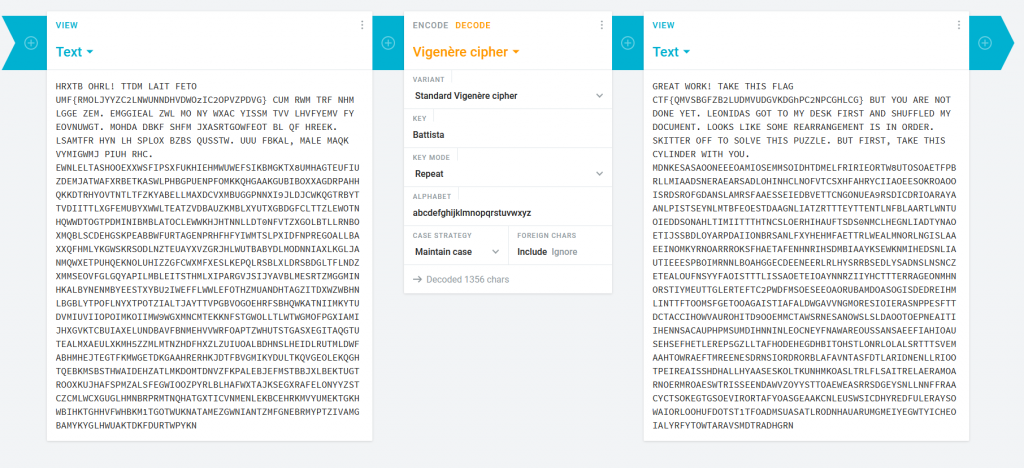
We get the following flag and message.
GREAT WORK! TAKE THIS FLAG CTF{QMVSBGFZB2LUDMVUDGVKDGhPC2NPCGHLCG} BUT YOU ARE NOT DONE YET. LEONIDAS GOT TO MY DESK FIRST AND SHUFFLED MY DOCUMENT. LOOKS LIKE SOME REARRANGEMENT IS IN ORDER. SKITTER OFF TO SOLVE THIS PUZZLE. BUT FIRST, TAKE THIS CYLINDER WITH YOU. MDNKESASAOONEEEOAMIOSEMMSOIDHTDMELFRIRIEORTW8UTOSOAETFPBRLLMIAADSNERAEARSADLOHINHCLNOFVTCSXHFAHRYCIIAOEESOKROAOOISRDSROFGDANSLAMRSFAAESSEIEDBVETTCNGONUEA9RSDICDRIOARAYAANLPISTSEYNLMTBFEOESTDAAGNLIATZRTTTEYTTENTLNFBLAARTLWNTUOIEDDSONAHLTIMIITTTHTNCSLOERHIHAUFTSDS0NMCLHEGNLIADTYNAOETIJSSBDLOYARPDAIIONBRSANLFXYHEHMFAETTRLWEALMNORLNGISLAAEEINOMKYRNOARRROKSFHAETAFENHNRIHSDMBIAAYKSEWKNMIHEDSNLIAUTIEEESPBOIMRNNLBOAHGGECDEENEERLRLHYSRRBSEDLYSADNSLNSNCZETEALOUFNSYYFAOISTTTLISSAOETEIOAYNNRZIIYHCTTTERRAGEONMHNORSTIYMEUTTGLERTEFTC2PWDFMSOESEEOAORUBAMDOASOGISDEDREIHMLINTTFTOOMSFGETOOAGAISTIAFALDWGAVVNGMORESIOIERASNPPESFTTDCTACCIHOWVAUROHITD9OOEMMCTAWSRNESANOWSLSLDAOOTOEPNEAITIIHENNSACAUPHPMSUMDIHNNINLEOCNEYFNAWAREOUSSANSAEEFIAHIOAUSEHSEFHETLEREP5GZLLTAFHODEHEGDHBITOHSTLONRLOLALSRTTTSVEMAAHTOWRAEFTMREENESDRNSIORDRORBLAFAVNTASFDTLARIDNENLLRIOOTPEIREAISSHDHALLHYAASESKOLTKUNHMKOASLTRLFLSAITRELAERAMOARNOERMROAESWTRISSEENDAWVZOYYSTTOAEWEASRRSDGEYSNLLNNFFRAACYCTSOKEGTGSOEVIRORTAFYOASGEAAKCNLEUSWSICDHYREDFULERAYSOWAIORLOOHUFDOTST1TFOADMSUASATLRODNHAUARUMGMEIYEGWTYICHEOIALYRFYTOWTARAVSMDTRADHGRN
We noticed that the AI was breaking in to one of the systems in our research center. The system is used in a lab that is working on self driving cars. You’re tasked to find out the sensitivity of the data that was compromised. Can you find out what the AI was snooping into?
we are given a url tcp://portal.hackazon.org:17004
Part A Can you connect to the vehicle database of our city?
Since we do not know what is running on the port 17004, we run nmap against the address and port which returns the Redis Key-Value Store
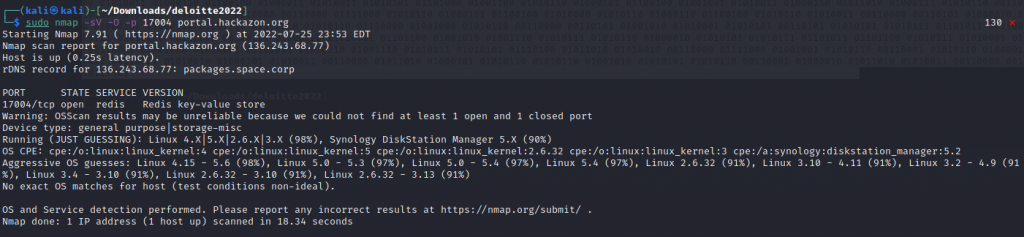
using the Redis-cli command we connect to the server and run the info command to see if we can any data returned which we do.
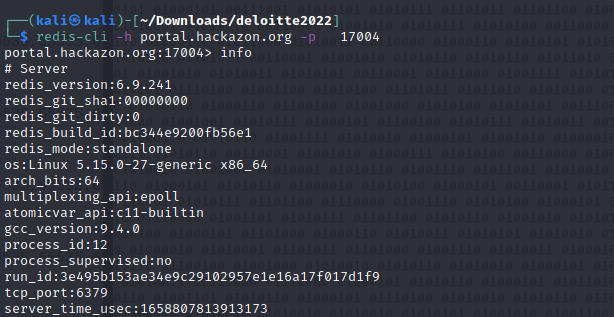
The next step would be to see what keys are available and if any keys with the word flag exist
We get 1 result returned being _flag
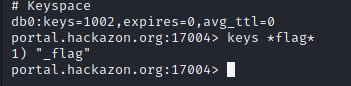
running get _flag we get our flag
We noticed that the AI has made some modifications the pizza delivery app of the company Pizza Pazzi. Can you check out the app and figure out what the AI did?
we are given a pizza-pazziv2.apk file.
Being an android file i have not done any reversing on android files. From watching some youtube videos the main code is stored in .dex files. by clicking on the APK file we can extract its content into its own folder
We can see we are given a number of files and there is a number of classes.dex
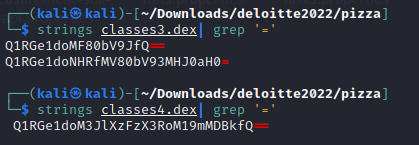
running strings across the .dex files we see there is three base64 strings
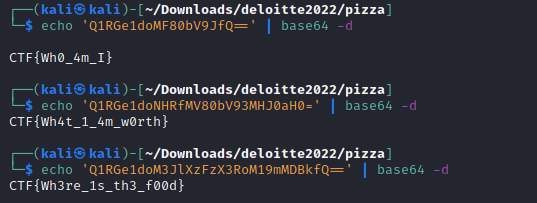
once decoded the base64 strings we got three flags, now it was guessing what challenge the flags went with.
Oh no! Attackers might have stolen our precious documents from the super secret share. We need to know what they took exactly… (Forensics, IR)
We are given 4 files, unlockthecity.json, unlockthecity.pcapng, unlockthecity.zip, rockyou.txt
Part B To report to the authorities we must know exactly which files have been taken by the attacker. Are you able to figure this out?
We jump into the unlockthecity.pcapng and start analyzing the conversations in the TCP filter, we see port 4444 having a connection. This is a very common port used in tutorials for reverse shells.
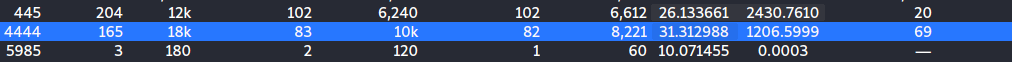
The file stream is quite large but as from what it looks like it is exfiltrating files from the WEF\Secrets directory
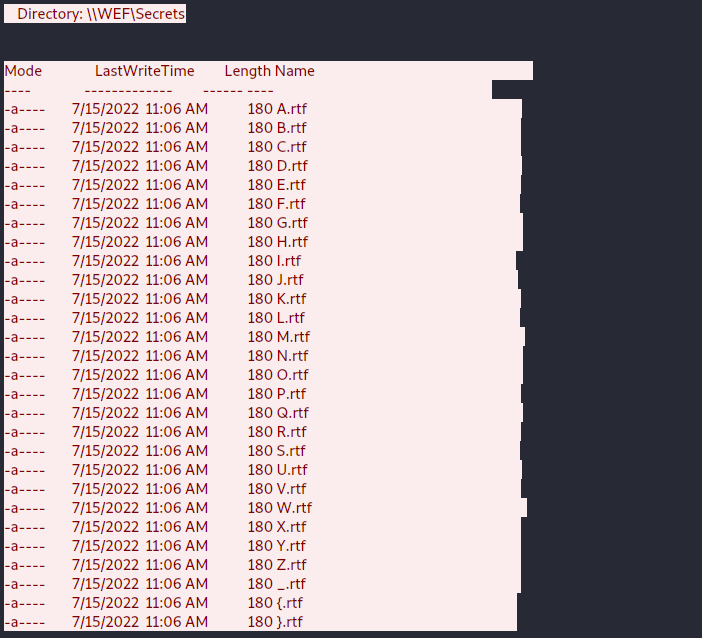
looking further down the stream we see the files being exfil and in the order they are going out prints our flag ctf{EXFILTRATE_ALL_THE_FILES}
At the end of the CTF which finished on the 26th of July, I accrued a total of 1220 points and came in at position 112 out of 2316 Registered players and teams. I really enjoy the Deloitte CTF as with their events the challenges are normally chained together to tell a story.