Between 18th October and 25th October 2021 Hack The Box (HTB) hosted Auth0’s CTF Event. Auth0 is an Authentication provider specializing as Authentication-as-a-service, Please check out the website here.
The event consisted of 6 categories (Web, PWN, Crypto, Reversing, Forensics, and Misc), I am relatively new to the CTF space and it was very good to see a category dedicated to Forensics an area that I am very fond of.
Forensics Challengers
Log
Brief: I recently found a file in my personal folder which is not mine. I don’t know what it is but I hope that none messed with my PC.
We are presented with a Packet Capture (PCAP) file, When we inspect the file in Wireshark we can see multiple streams of data from USB devices
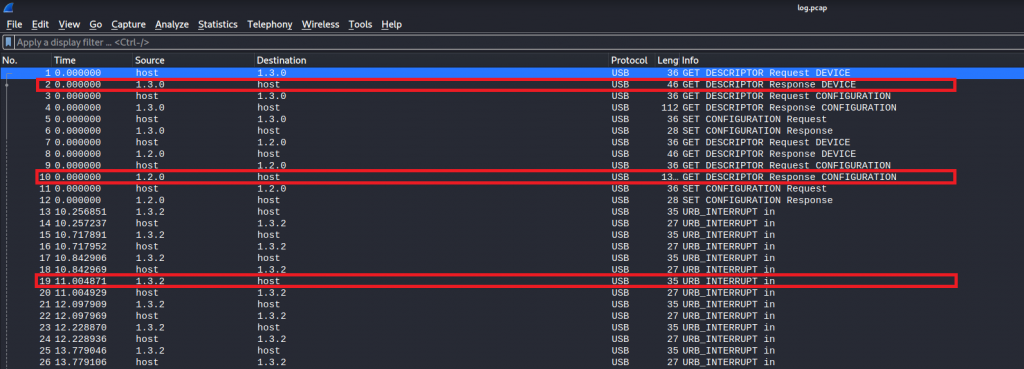
Once we had exported the individual streams we noticed with stream 1.3.2 there is leftover capture data.
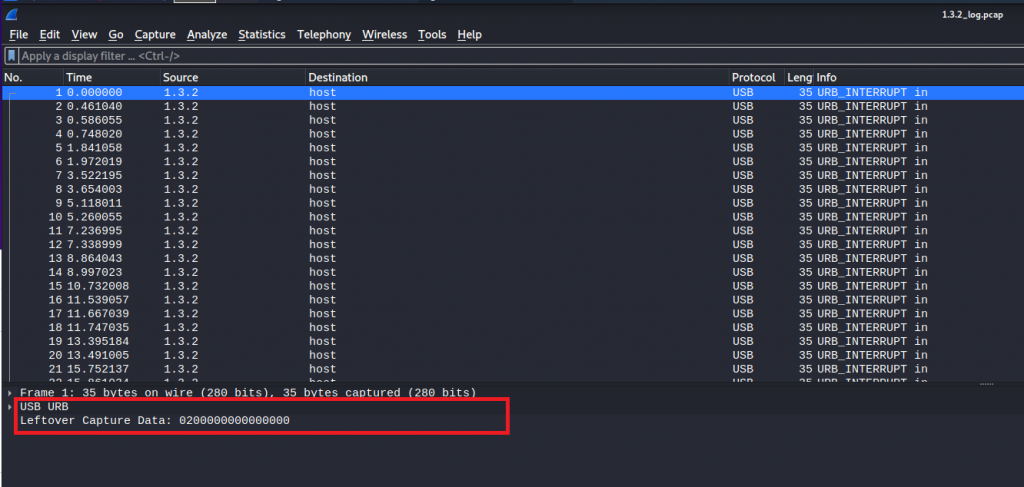
Doing a google search on “Wireshark leftover capture data” I came across the following blog article that explains how to translate the Leftover Capture Data into something meaningful. Once I ran tshark against the PCAP data we got the following data.
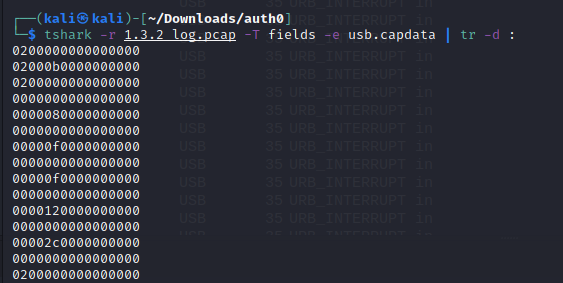
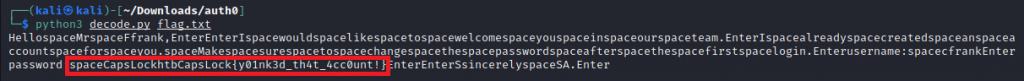
Once copied into a file and ran against the script in the blog article we get the message which contains the flag for the challenge.
Compromised
Brief: Along with the previous attack, we suspect that there were more following. They believe that they can gain access to every system we own without being detected. Do they have enough skills?
Find the attacker’s IP
Find the malicious’s process ID
Find the timestamp that the malicious process had been initiated
Flag format: HTB{attacker’s-IP_malicious-proc-ID_YYYY-MM-DD_HH:MM:SS}
After downloading forensics_compromised.tar.gz and extracting the contents we were given a raw file, comromised.raw.
Running strings against the file we can see it’s a windows memory dump file.
using Volatility3 (Vol) a Memory analyzing program we can pull out the information we need. Searching on google for ‘Volitatility3 Windows Cheatsheet’ I found https://book.hacktricks.xyz/forensics/basic-forensic-methodology/memory-dump-analysis/volatility-examples
Referring back to the Brief “Along with the previous attack, we suspect that there were more following.“, This made me think some commands were ran. In Vol we can pull the commands that were executed. We see a powershell process executing what looks like a base64 string
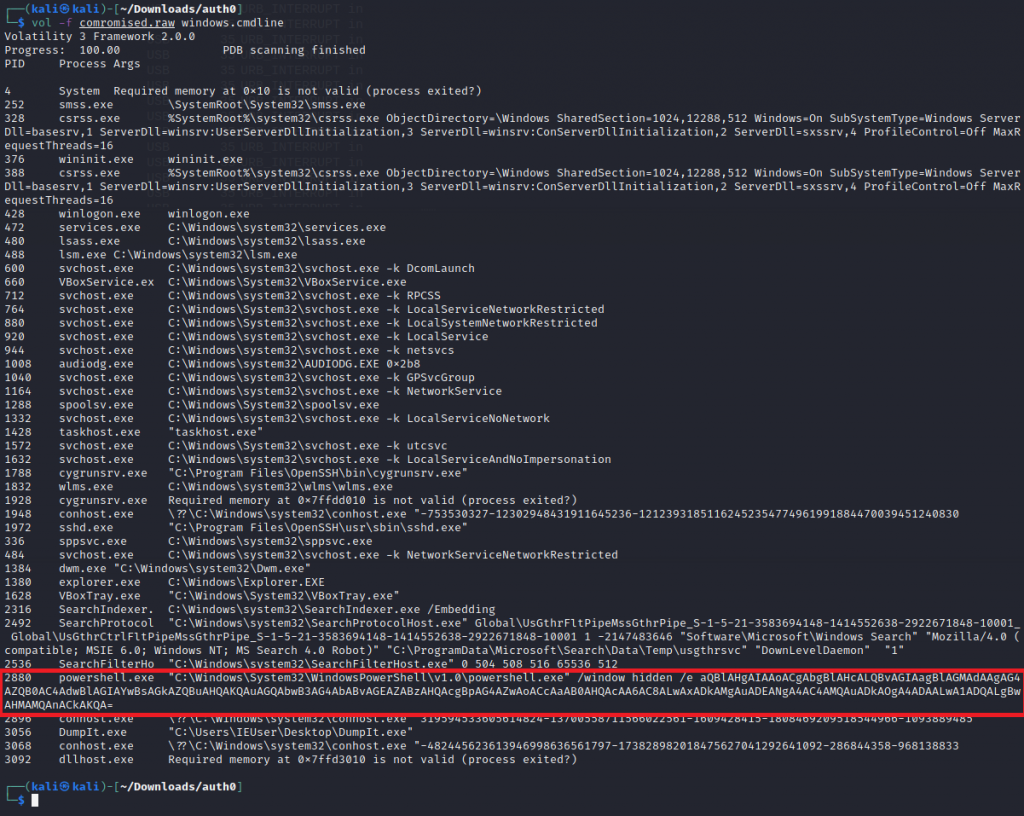
Once we decoded the base64 we can see some malicious code being run as a ps1 script. This has also gave us the IP of the malicious actor (192.168.1.9)
Now we know the PID (2880) that was running the script we can look at PsList to obtain more information about the Process.
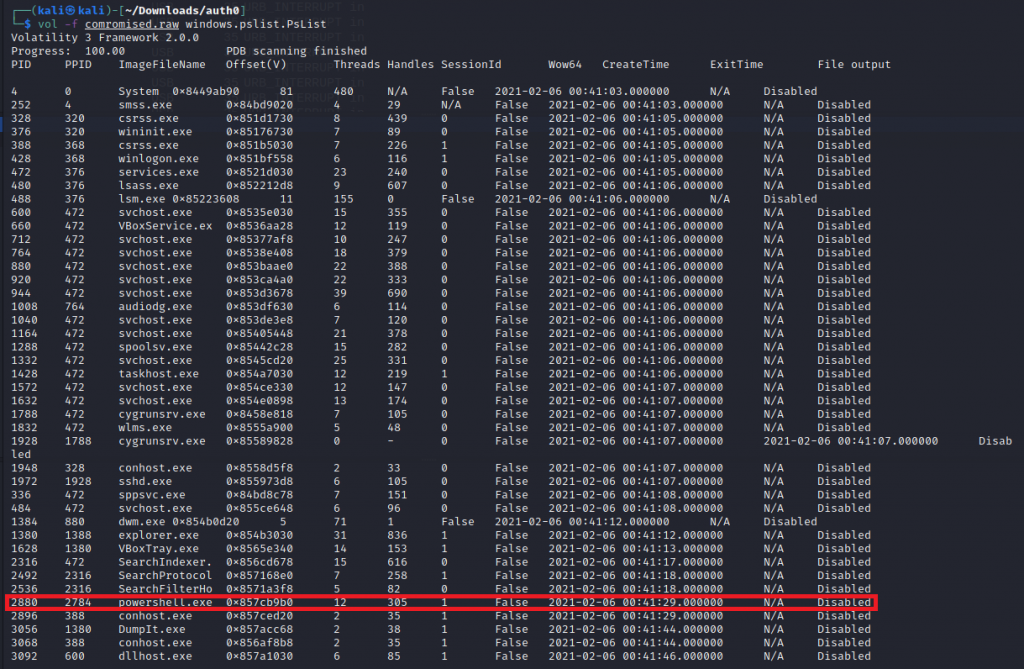
Now we have obtained all the information that we need to craft our flag. As the brief requested Flag format: HTB{attacker’s-IP_malicious-proc-ID_YYYY-MM-DD_HH:MM:SS}, Our flag is HTB{192.168.1.9_2880_2021-02-06_00:41:29}
Suspicious
Brief: We have noticed that one of our IT employees has access to servers and files that he should not. We confronted him but he denied every accusation. Can you prove him wrong?
We are presented with another PCAP file, This time the PCAP contains FTP and HTTP streams.
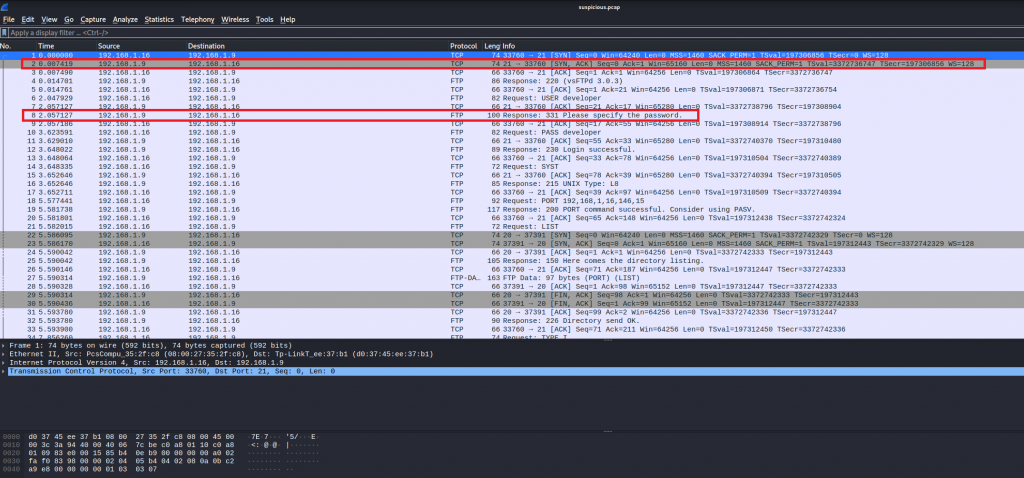
WireShark allows us to view steams via conversations. Under the TCP tab we can see three steams
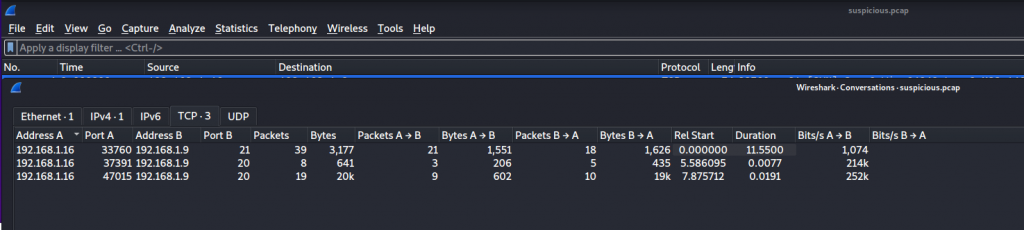
Reviewing the first stream we can see this is a transcript from vsFTP 3.0.3. IT indicates the developer has logged on and downloaded Financial_statements – Transactions.pdf. This information does not contain the flag we are looking for but its an indication we in the right direction.
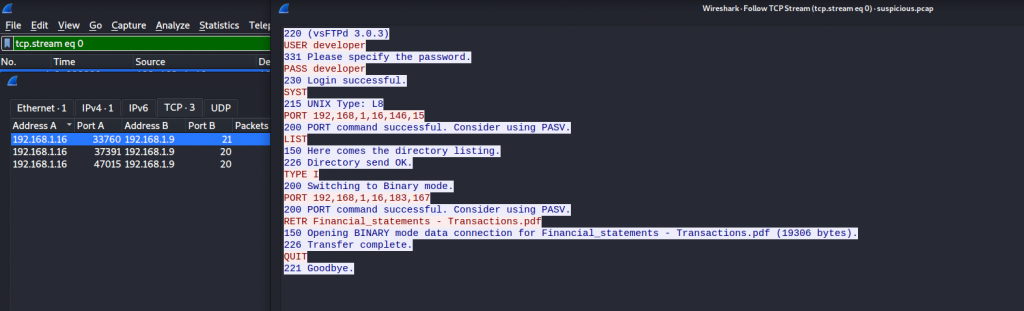
Stream 3 indicates we are looking at the PDF file that was downloaded. The data is being displayed as ASCII, We are able to save the file but for it to be successfully exported the data needs to be set as raw.
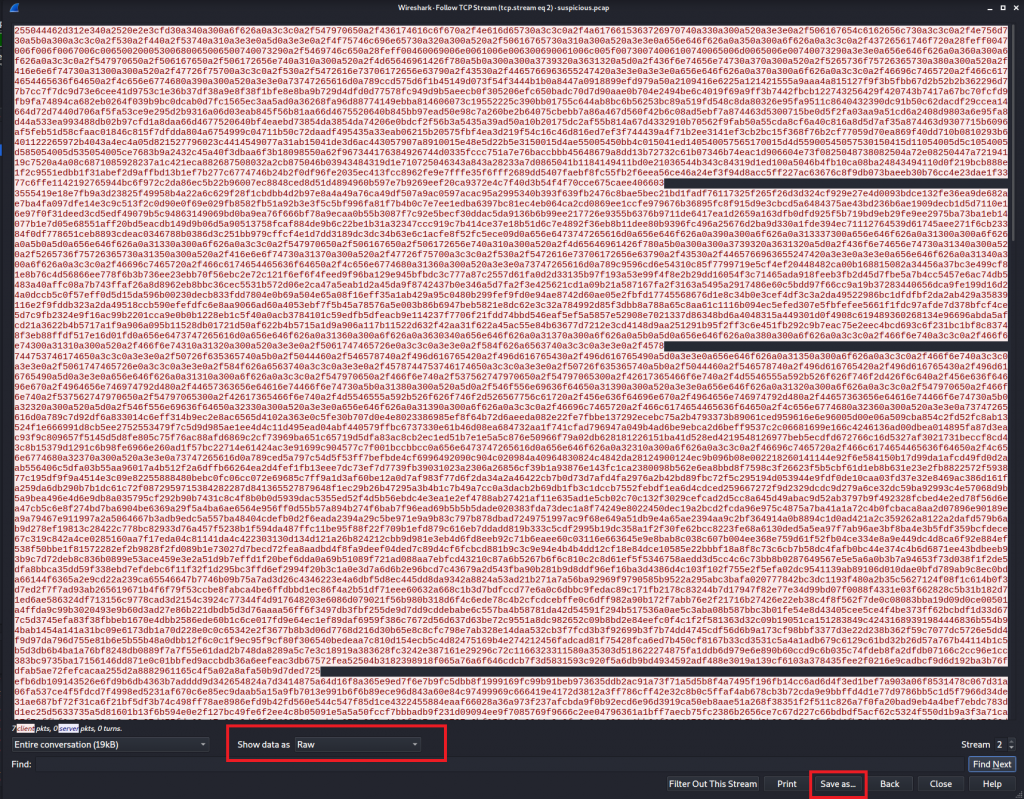
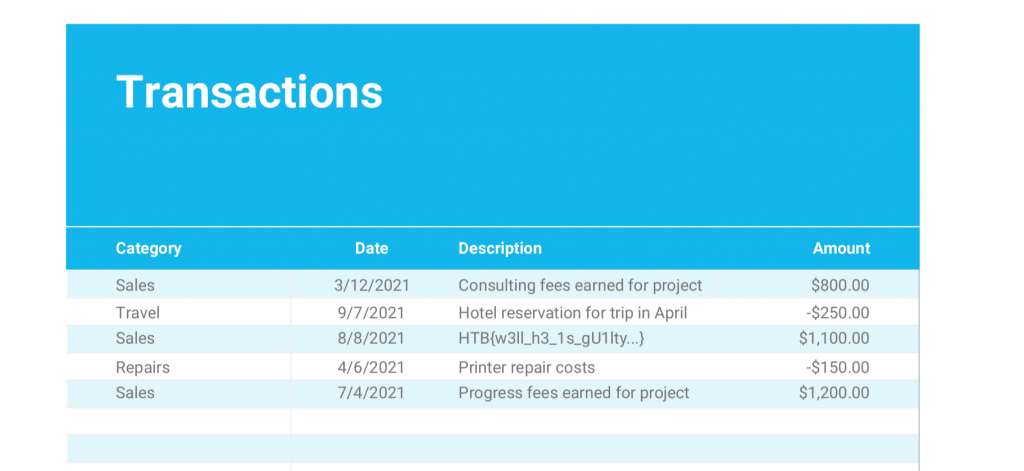
Once the PDF was saved we could open the file and we were presented with the flag
Thanksgiven
brief: I recently received an email from ou HR that promts us to fill the dates we want to leave from work during thanksgiving. The problem is that I am not able to edit the file even if I enable editing like the document suggests.
We are given a .xlms (excel spreadsheet with macros enabled). When opening the file we are advised ‘This document is protected’
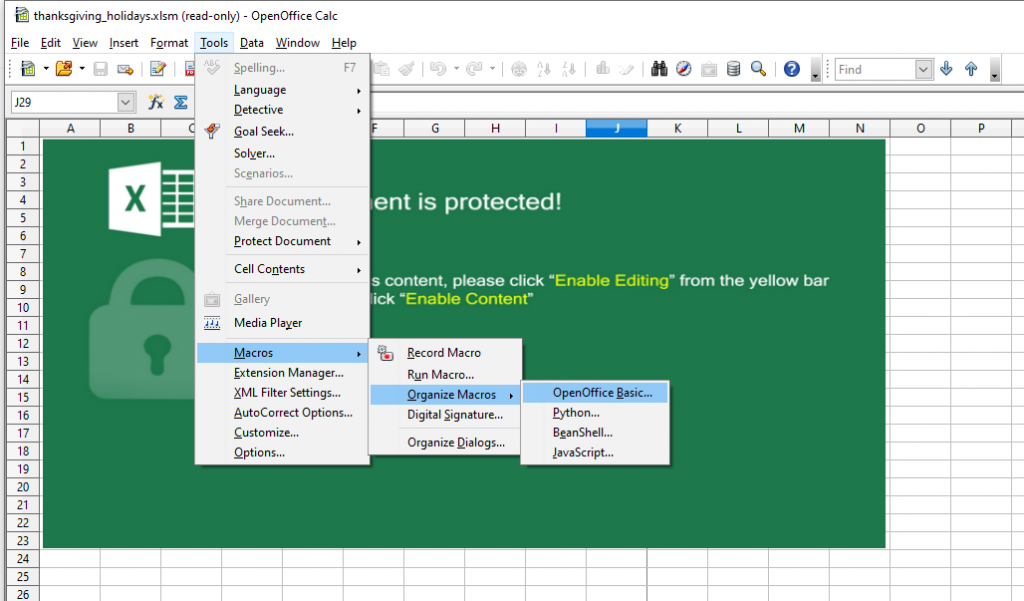
Being a macro-enabled spreadsheet, in Openoffice, we can inspect macros under organize macros > OpenOffice Basic…
Once we open the worksheet macro we can see there is some encoded strings.
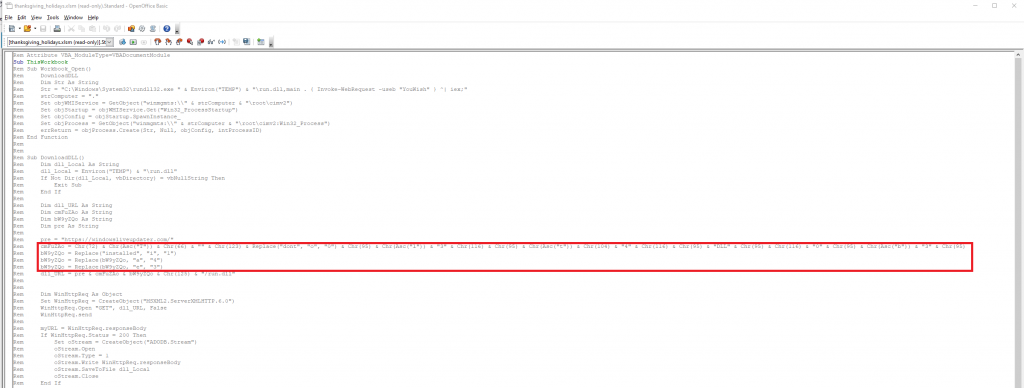
Once we decoded the strings we are given our flag.
Conclusion to Forensics challenges
It was really welcoming to have some real-world examples where I got to use WireShark and Volatility, I have used both of these in labs on Try Hack Me but nothing as in-depth as these challenges. The password hidden in the macro was a fun challenge and I do enjoy decoding strings. From these challenges I have learned a lot which I can take to the next CTF event.
Due to time constraints, I attempted the other challenges and managed to solve two.
EsQuelle – Web
Brief: We think our agency’s login panel application might be vulnerable. Agent, could you assess the security of the website, and help us prevent malicious actors from gaining access to our confidential information?
When visiting the webpage we are only presented with a username, password fields, and a submit button. No other links, Nothing hidden in the source code.
Running through MySQL login bypass methods found in https://pentestlab.blog/2012/12/24/sql-injection-authentication-bypass-cheat-sheet/ We were able to get in using admin’ –
Gate-Reversing
brief:In order to proceed, you need to pass through the gate. Do you know the secret password?
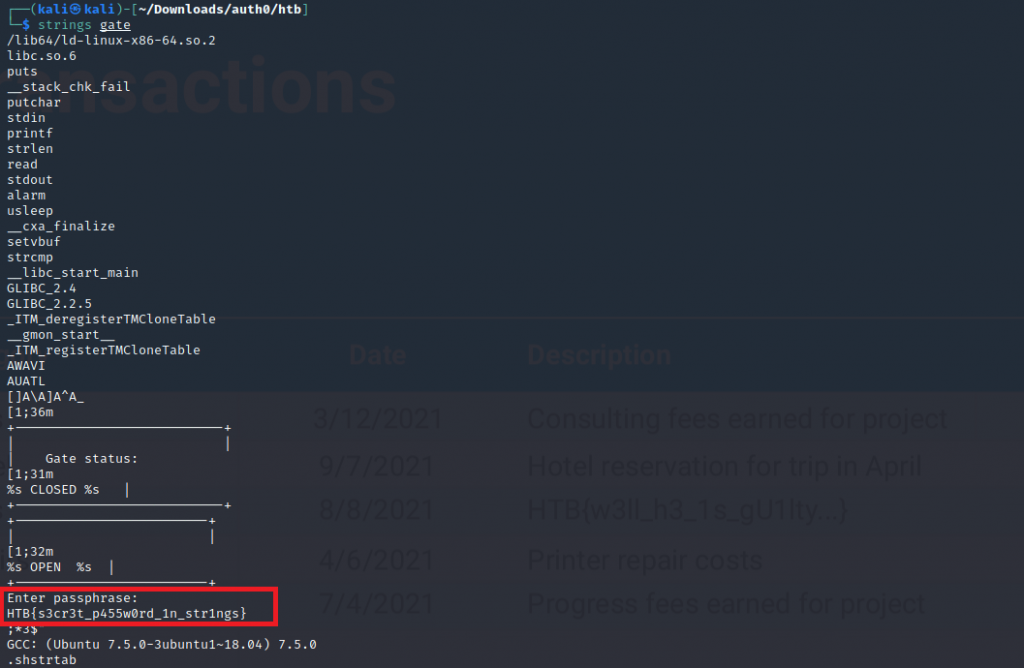
We are given a binary called gate. The first step I did was running strings against the file
From running strings we found our flag in plain text
Summary
This was my first capture the flag event I entered solo, It was great to test my knowledge and learn new skills. Even tho I did not rank in the top #100 (I ranked #154, it was awesome to give it a good try).