PHaaS or otherwise known as PHishing As A Service is not a new endeavor as it became popular is 2016. PHaaS allows people with no experience to launch Phishing campaigns targeting people. PHaaS comes in many different forms from active Phishing campaigns to validating records that can be purchased on the dark web in a username and password lists
I recently came across a Phishing campaign brought to our attention by NetCraft. The campaign was targeting office365 clients, Upon investigation, we discovered this was no your standard Phishing campaign but was using a variation of PHaaS. The following excerpt was found from an index file that was uploaded.
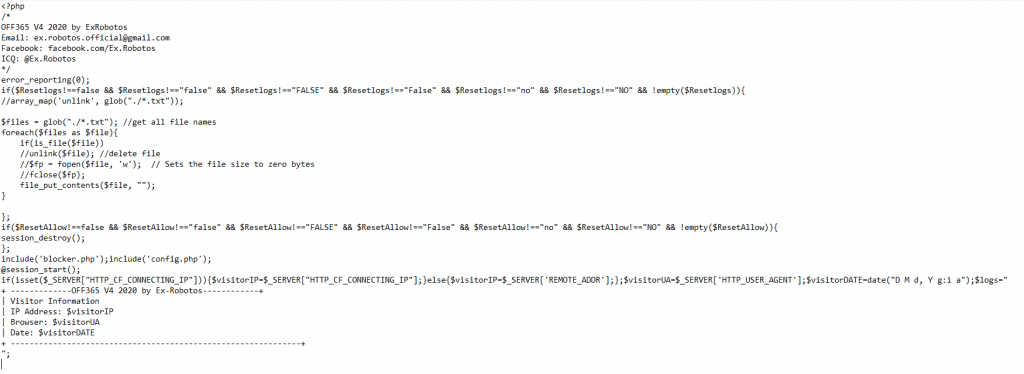
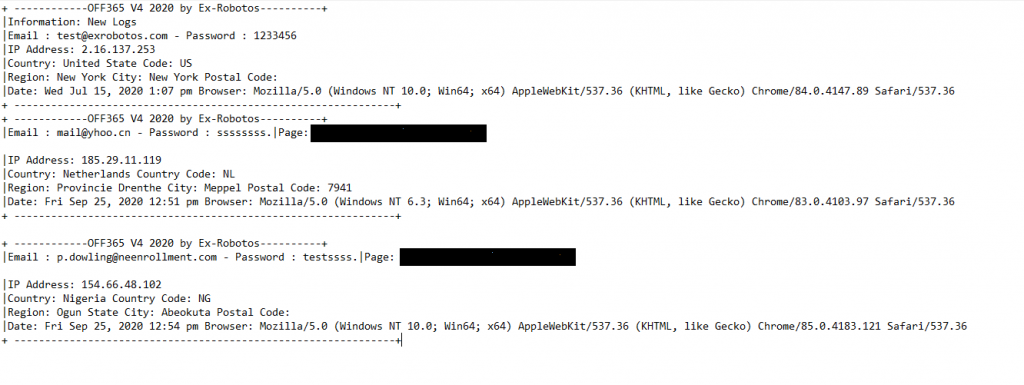
As you can see the actual script is created by ‘Ex Robotos’ and the users did not bother in removing any of the identifying comments relating to the creator. A search of the files also lead to the finding of a log file (logs.txt) that consisted of usernames and passwords that have been harvested from this campaign,
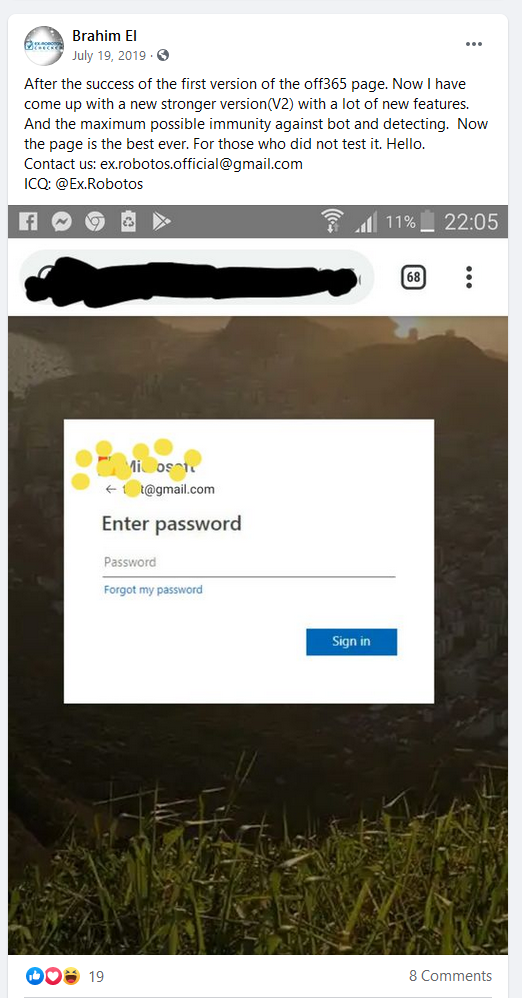
Searching for the creator behind the PHaaS script leads us to a Facebook page created for selling the service

There is direct evidence that links this Facebook page/person to the Phishing script, As below you can see the creator boasting about how successful his script is.
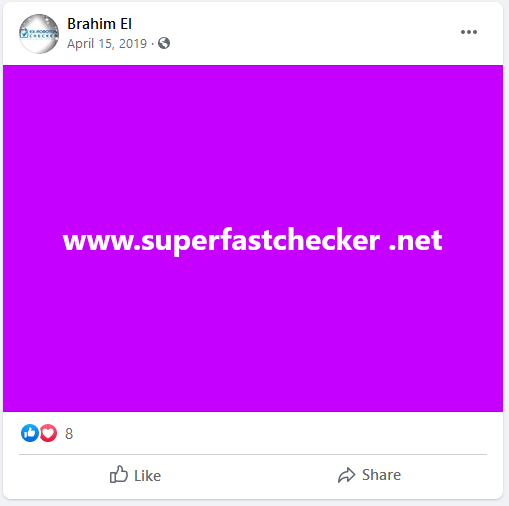
He has listed a few links where you could go ahead and purchase the scripts from such as superfastchecker.net however these URLs have been taken down.
The creator also created a YouTube video as a marketing tool to show how the script works. At the present time, the video can be seen below
This script in the video shows how you can validate credentials. With this particular PHaaS they’re charging a fee to validate passwords.
5 $ ==== 35,200 Credits (paypal / bitcoin)
10 $ ==== 80,800 Credits (paypal / bitcoin)
20 $ ==== 173,200 Credits (paypal / bitcoin)
50 $ ==== 460,000 Credits (paypal / bitcoin) 1
Credit == 1 Email check.
This particular PHaaS creator has a decent data footprint on Google. Searching ‘Ex Robotos’ leads to a number of links relating to his scripts.
As with Phishing; this has been around since 1995 (Source: https://cofense.com/knowledge-center/history-of-phishing/) Now with Cyber Criminals and malicious actors looking at other ways to capitalize with Phishing I would suspect we will see new waves of PHishing as a Service campaigns