For testing Malicious scripts and Software I run a Windows 10 Virtual Machine with 4Gb Ram and 2 CPU cores. The Virtual machine is setup as host only with no internet access. I also run REMNux 7 which will be explained later on. My Malware test environment is a running project and having new applications and tools added to it. I will go through a few of my tools I use now to decode/reverse malicious code I find.
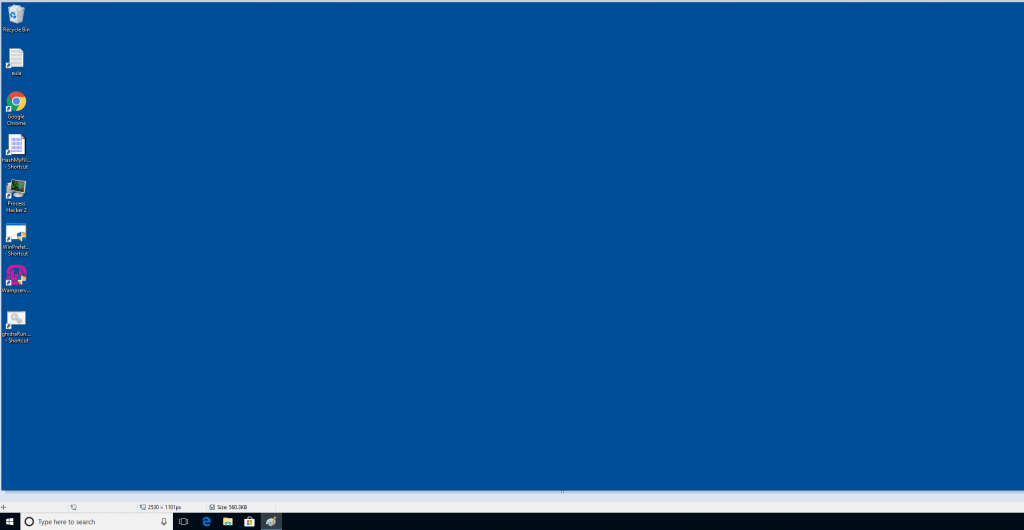
PHP Script Testing
For PHP script testing I run XAMPP, XAMPP is a PHP Development environment that runs on your local PC. It supports
– Apache (Web Server)
– MySQL (Database)
– Filezilla (FTP Server)
– Mecury (Mail Server)
-Tomcat (Running of Java applets)
Decoding Windows Executables
Decoding/Reversing Windows Executables can be done a few ways, I prefer using the Open Source CIA tool Ghidra, Ghidra was made available after the Wikileaks leaked the tool (for more information on the leak please see here)
Ghidra is useful at pulling malware samples apart, finding and can be used to analyze how the program works.

There is many videos on youtube that shows how ghidra works and many free tutorials.
HashMyFiles
HashMyfiles is a application that allows you to run your scripts and programs and generate the required hashes.
Using hashes you can search websites like Virus total for known hits.
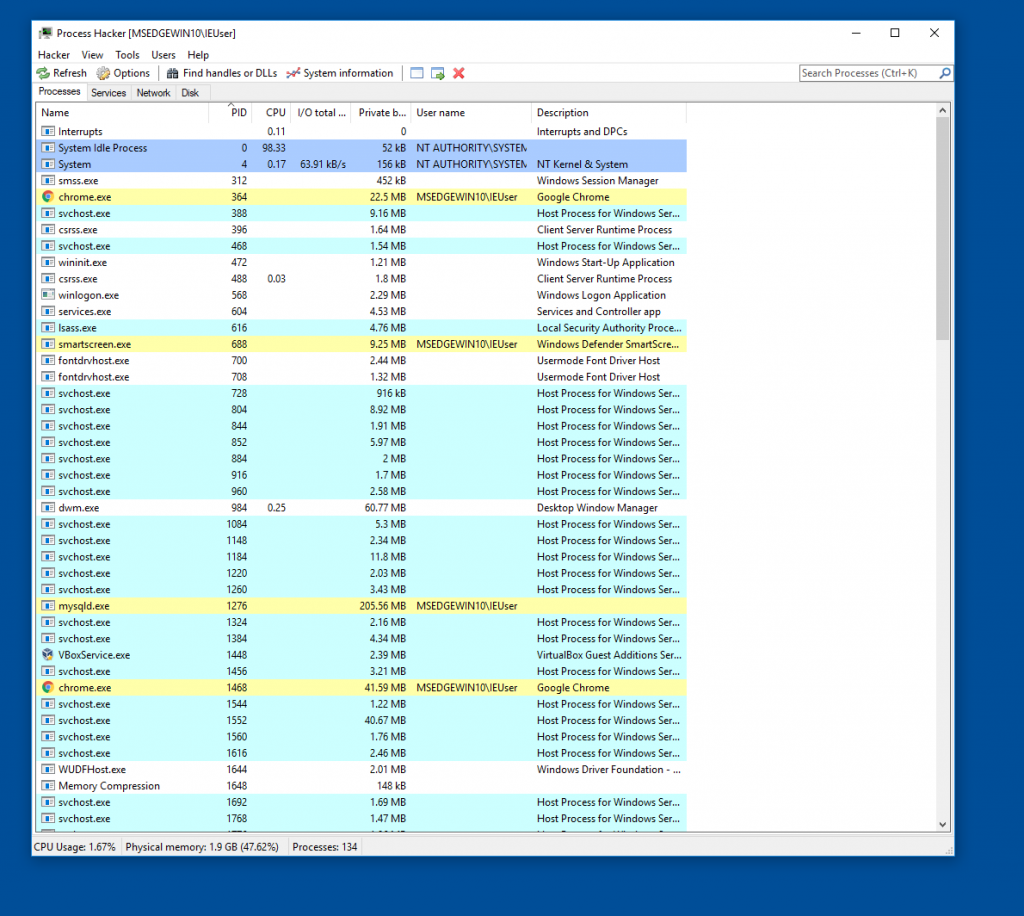
Process hacker
Process hacker is a freeware application that allows you monitor the processes running in windows, It is very useful for when you launch the malicious script to see if it spawns new processes.
WireShark
Wireshark is a network monitoring tool which allows you to catch raw packets on your network. It is very useful to monitor outbound connections once you start running pieces of malicious code. With Wireshark you can filter specific ports or protocols.
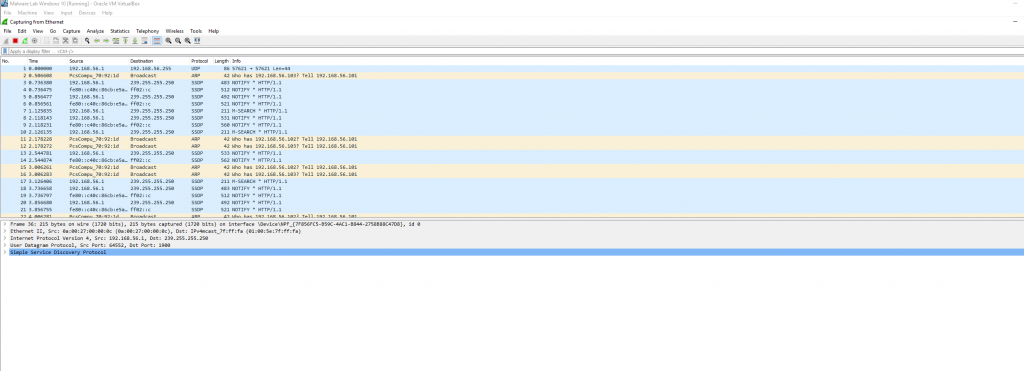
Like Ghidra there is a number of videos on youtube on how Wireshark works and tutorials on setting up wireshark and how to use it.
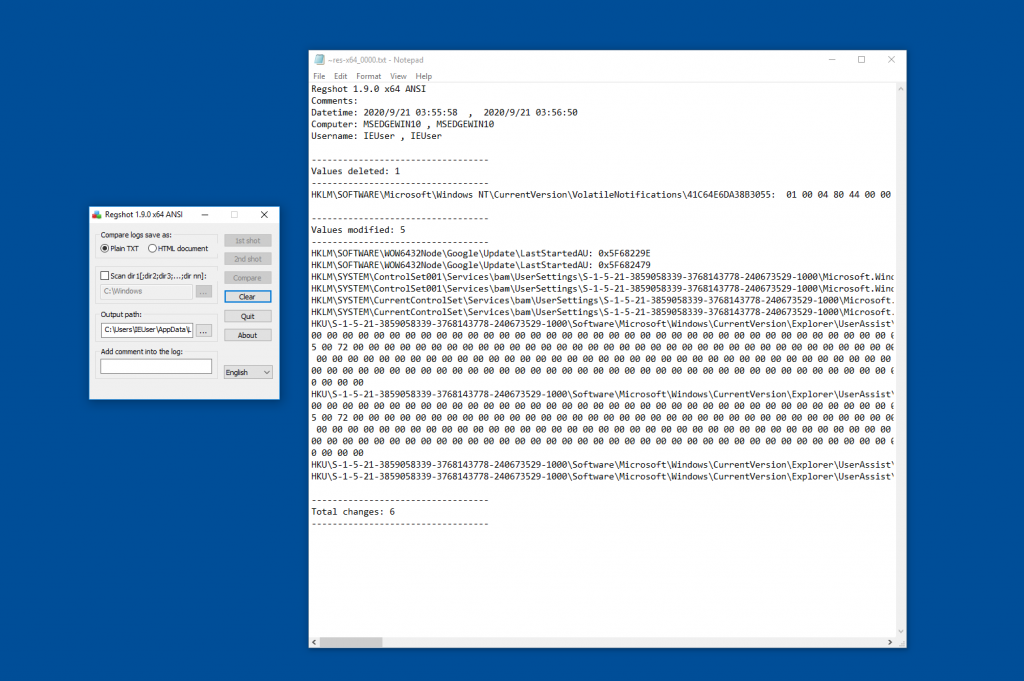
Regshot
Regshot is a useful tool to take snapshots of the system registry, I find this very useful for taking a screenshot before I run any malicious script and then after I run the script and confirm if any of the registry entries have been modified, It allows you to output the data to a text file or to a webpage.
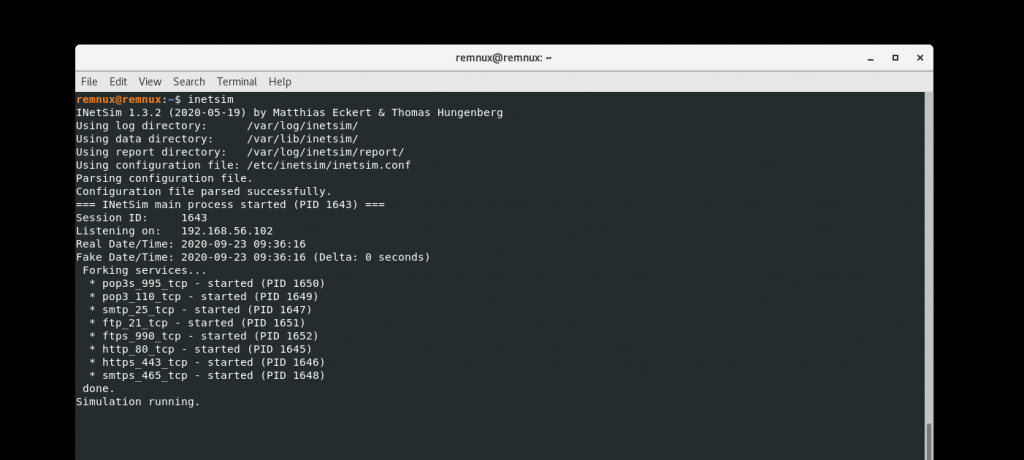
Network Monitoring.
As mentioned at the start I run the VM on a host only network, This connects to REMNux which is a A Linux Toolkit for Malware Analysis which helps in analyzing the traffic coming from the VM. It is useful to see if a script is connecting to a Command and Control server or downloading additional resources/payloads, REMNux allows you to simulate active POP, SMTP/SMTPS, FTP/FTPS, HTTP connections.
This article is a constant work in progress and as the project expands more information will be added